XDR: Helping Keep Your Users Safe
Control points share information for automatic remediation
Keeping your data safe never gets easy. Take the case of a major enterprise platform that was compromised by malicious code. Cyber security specialists thought they had mitigated the threat, but it kept coming back. That’s because the threat remained in the network, despite efforts to eradicate it.
Unfortunately, the same could happen to you, unless you establish a cyber security defense that enables different control points to talk to one another. Without an information sharing network, a threat can effectively hide, only to re-emerge repeatedly.
At Symantec, a division of Broadcom (NASDAQ: AVGO), ICD is our strategy for simplifying and uniting cyber security tools.
Symantec’s ICD (Integrated Cyber Defense) platform functioning as a core component of Symantec’s XDR can help you set up such an information-sharing network. At Symantec, a division of Broadcom (NASDAQ: AVGO), ICD is our strategy for simplifying and uniting cyber security tools. ICD builds on Endpoint Detection and Response (EDR), adding telemetry streams from multiple control points. ICD also normalizes and aggregates data. When an incident happens, ICD enables you to identify it across all control points: network, email, cloud, and endpoint. You can observe how the malware got in, how long it stayed, and what it did.
For this blog I'll explain how a few foundational pieces of ICD, network scanning and EDR, integrate and why even with automation, the human element remains important. When a threat attempts to compromise a network, here's how ICD detects and responds:
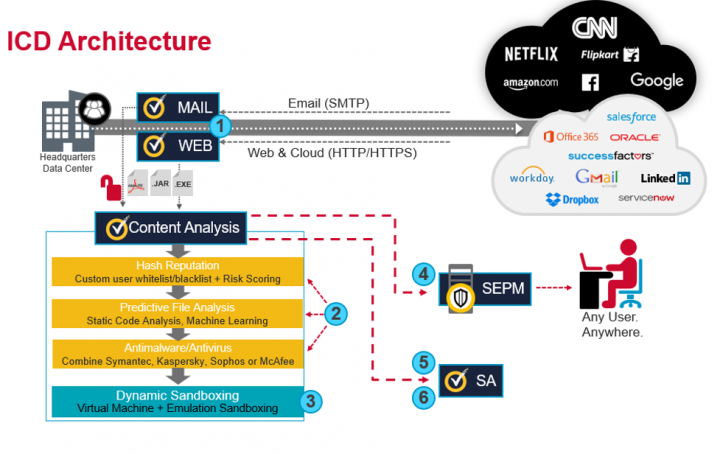
At the network:
Step 1 – The network control point, in this case a Web Gateway, receives a file as part of a download. The reality is that any type of termination point, such as mail gateways, file storage appliances, or web application firewalls, can be a termination point.
Step 2 – Files are extracted in their entirety and sent to Symantec’s Content Analysis System (CAS) first stage for scanning. (Symantec's CAS is a platform that can integrate with many technologies such as web gateways, mail gateways, and file storage solutions to scan and mitigate threats without allowing users access to a single byte of the malicious file until it is deemed safe). This is a multi-stage scan utilizing three distinct detection methods in a specific order to reduce the number of files scanned by each subsequent process:
- Hash Reputation - Verifying content against a known good / known bad hash lists
- Predictive File Analysis - Static code analysis, Machine Learning
- Antimalware/Antivirus - Traditional antivirus signatures. Up to two different vendors can be used for this scan increasing the number of vendors that can scan content.
Step 3 – Unknown files are sent to the second stage of CAS, the sandbox. Sandboxing can be an active inline tool in this process since it's only analyzing unknown files. All known good and known bad files are handled by earlier steps. Telemetry of the sandboxing is sent to the requesting service for it to decide what to do. In the case of our termination points, they deny any malicious files automatically.
Response
Step 4 – CAS sends file telemetry to Symantec Endpoint Protection Manager to disseminate to all endpoints. Endpoints are now alerted to the new malicious file, can scan for and isolate the file across any endpoint, anywhere in the world.
Step 5 – CAS also sends a report of the sandbox to Security Analytics (SA), a recorder of data on the network, which retains full packet histories for investigation, file scanning and verification against third party entities. SA constantly records traffic to create a historical record and acts as a single source of intelligence for SOC personnel.
Step 6 – An investigation can then begin with deeply enriched data from SA.
The Human Element
Much is made of automation – and automation is absolutely necessary. There are too many threats to deal with manually, and qualified cyber security experts are expensive and hard to find. However, the human element of cyber defense will never go away. In fact, you could consider human involvement Step 6.
The important thing is to make sure that when a SOC analyst does become involved, his or her time is well spent. ICD makes sure this is the case. For example, once a breach has occurred and has been mitigated, a SOC analyst should examine what happened to make sure it won’t happen again. The response to one attack can form the basis of a threat-hunting exercise for a future attack. Your overall defense is improved because you can discover vulnerabilities before compromise occurs.
Making XDR Work for You
As you can see, the sharing of information between control points, endpoints and the SOC analyst enables a thorough examination and understanding of content. And feeding information back to the endpoints for remediation helps prevent malware from reappearing or spreading further.
In the future, XDR will be able to aggregate even more information, including Symantec Information-Centric Analytics (ICA) and feeding that telemetry into the security tools or control points to make automated decisions. XDR has an open ended outcome. Tools will be designed to share telemetry that we haven’t yet conceived. Being able to automate intelligent decisions within the security stack is going to be an ever changing situation and one I’m welcoming in the future.

Why Security’s Future Depends on Effective Integrated Cyber Defense
Integrations are key to cyber security in the future










We encourage you to share your thoughts on your favorite social platform.