XDR: Aggregation and Analysis Overcome the Skills Gap
With cyber security expertise in short supply, consolidating telemetry data and applying ML analytics can keep your organization safe
Keeping your data safe is a big job and getting bigger all the time, so chances are you have deployed many cyber security tools. But do you have the skilled experts to manage all these tools – to keep them updated, to stay on top of their alarms and correlate their output? It’s not easy to find and keep qualified cyber security specialists -- and it’s unlikely to get any easier.
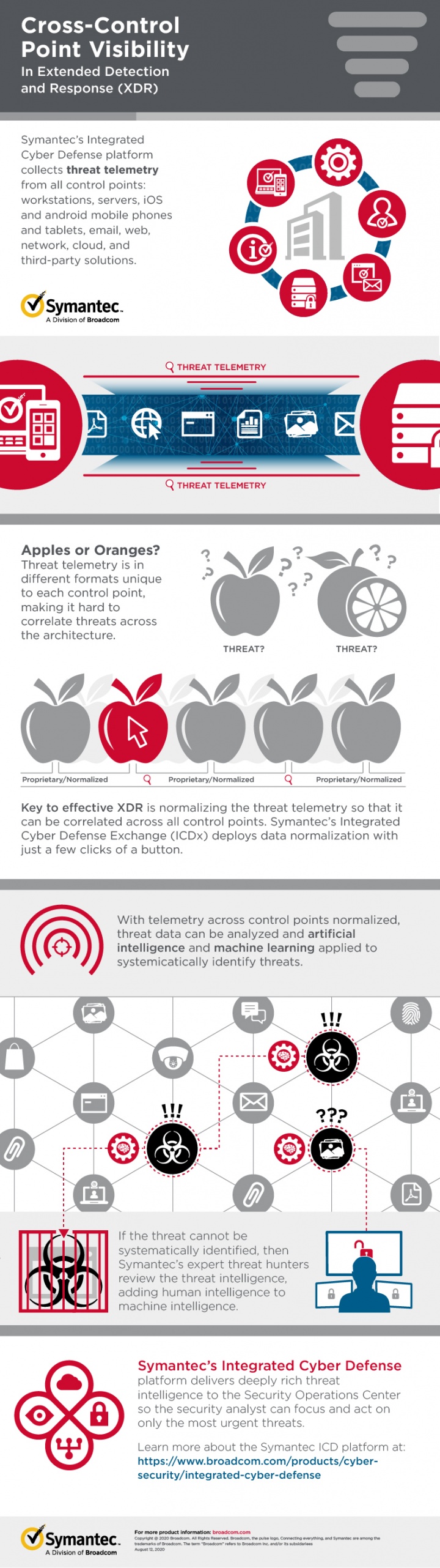
One of the best ways to cope with the cyber security skills gap is to make the experts you do have more efficient. That’s where Extended Detection and Response (XDR) comes in. Symantec Integrated Cyber Defense platform enables XDR, covering endpoint, network, and cloud workload protections, as well as sandboxing, threat intelligence and analytics. Integrated Cyber Defense simplifies and unites cyber security information to help your experts work faster and smarter.
As my Broadcom Symantec colleague Ryan Stolte explains, XDR builds on Symantec Endpoint Detection and Response (EDR), adding telemetry streams from multiple control points to provide a unified incident detection and response platform. XDR systems centrally store event data, actions and intelligence in a common format. That enables managers to study threat information in context, and correlate it across multiple systems, rather than receiving alerts from each system separately, which could easily overwhelm them with too much information.
And as Broadcom Symantec expert Javier Santoyo says, “XDR normalizes and correlates information to make your cyber security staff more efficient and effective in defending your organization.”
Identifying Unknown Threats
Once the telemetry is collected from across control points and normalized, Symantec, a division of Broadcom (NASDAQ: AVGO), takes a first pass at identifying unknown threats by comparing that intelligence against intelligence we collect through our Global Intelligence Network, or GIN, one of the largest civilian security threat intelligence networks in the world. Where does the GIN intelligence come from? Information is correlated from 175 million endpoints and more than 126 million attack sensors. Knowledge is correlated across seven research operations centers by more than 500 security experts, analyzing over nine Petabytes of security threat data.
If we can’t identify the threat from GIN intelligence, we then start a series of analysis to continually research and understand the threat. Some of those analyses include applying artificial intelligence and machine learning, behavioral analytics, targeted attack analytics, and even Symantec human experts. These resources enable us to discover and block advanced targeted attacks that would otherwise go undetected.
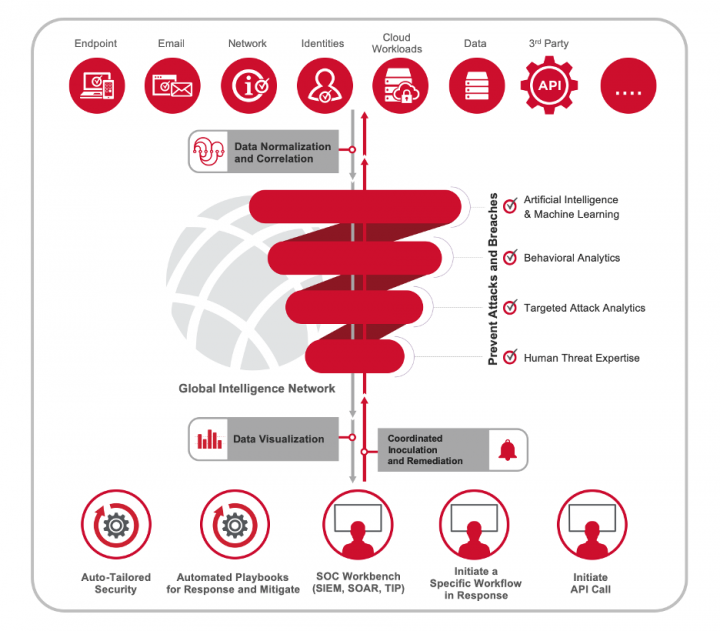
User and Entity-Based Analytics
It’s important for threat analysis to take a customer’s business context into consideration, not just alerting on unusual behavior, but prioritize remediation in terms of how risky that behavior is to the business. As an example, user and entity-based analytics (UEBA), studies user behavior patterns, searching for anomalies that might indicate suspicious activity.
For example, if an engineer is typically working from 8AM to 5PM, and that person downloads large files at 3AM, his or her activity would be flagged for review by security specialists. Because not all anomalous behavior is due to persons, studying “entities” is also important. Entities can include devices such as servers, desktops and mobile devices – and increasingly, the rapidly expanding multitude of Internet of Things (IoT) devices.
UEBA tools can also correlate normalized data across control-points, enabling the identification of high-fidelity alerts composed of different telemetry streams. This type of intelligence can then also direct response actions at the control points for enhanced protection and mitigation of the detected threat.
The ML-based UEBA system feeds its information into a SOC front-end tool such as an information-centric analytics (ICA) system or a security orchestration and response (SOAR) tool. A SOAR is a rules engine that coordinates responses to security information. Although you can perform this integration yourself using APIs, we let you use the tool of your choice by offering turnkey integrations with many partners.
Keeping Your Data Safe
There’s a vast quantity of threat information out there -- too much for mere humans to keep track of. By aggregating, correlating and automating through XDR, then integrating through point-to-point solutions, we free up your cyber security experts to do the work they’re trained to do by reducing noise and focusing on true positives that have been enhanced with intelligence. By leveraging ML, we help you automate 80% of the work, which enables your analysts to focus on the remaining 20%. And that 20% is typically the most important threat data. It’s our way of making those valuable experts more efficient and effective – and helping to keep your organization’s precious data safe.

Symantec XDR: A Streamlined Approach to Enterprise Security
Simplifying Enterprise Security Architecture








We encourage you to share your thoughts on your favorite social platform.