Why Security’s Future Depends on Effective Integrated Cyber Defense
Integrations are key to cyber security in the future
With more endpoints to manage, more networks to secure and more data to protect, the last thing enterprise companies need is an ever-growing yarn ball of fragmented tools that are hard to deploy and hard to manage – not to mention the fact that they undercut the goal of cohesive overall threat detection and prevention. This is where the importance and the strength of integrations help create a better security environment for customers and partners of Symantec, a division of Broadcom (NASDQ: AVGO).
It’s also clear that the threat landscape is moving too rapidly for enterprises to safeguard their data by clinging to a patchwork of one-off solutions. That may have been good enough in the past but not today. The shift from on-prem to cloud-based SaaS solutions means that yesterday’s conventional wisdom will only lead to a dead end – or just endless sprawl. Analysts estimate that the prevailing tactical approach to cyber security has resulted in nearly two thirds of large enterprises having at least 25 cyber security products in use. To be successful, things must work together easily and with little effort from the admins – regardless if the products come from the same or different vendors.
Key Integration Challenges:
At Symantec, we saw this trend start to develop years ago when it was in the early stages. We got to work to remedy that problem by building an Integrated Cyber Defense platform (ICD) with the idea that customers would benefit from the best-in-class security working together – whether we’re talking about protecting endpoints, networks, email, data or identities, integrated at key points to offer better protection and lower operational costs via a more streamlined and effective platform.
The result – Symantec’s Integrated Cyber Defense – features a single platform that brings together cloud and on-premises security along with protection across endpoints, networks, and applications. Given the profound security challenges that businesses need to contend with during this current tech transition, and beyond – we believed that enterprises would benefit from Integrated Cyber Defense as it’s simply a better concept to fit a new era.
Platform Integrations Three Ways
Symantec has also made a major effort to deliver integrations between existing standalone technologies at different levels, making sure that any connecting points are defined and documented so that customers don’t have to spend their budgets and time to make this work.
First, at the product level, we have reduced complexity by integrating previously standalone solutions into single, coherent products. The latest example is our newly released SES Complete. Customers only need to install one agent which performs all the necessary tasks. This kind of integration has more value for customers—not just because they get better protection, but it also makes it easier for them to configure and deploy.
For those often beleaguered Security Operation Center (SOC) defenders, we’ve made it easier for them to do their job thanks to SES Complete. Here’s an example:
- The SOC analyst receives an incident from the Symantec Endpoint Detection and Response (EDR), capabilities included in SES Complete.
- After doing some research, they identify how the threat ended up being in their environment.
- While still in the same console, they can then take the appropriate action.
- Not only that, but they can identify and block the particular behavior pattern from reoccurring by setting the behavior isolation policy to reduce the attack surface in the event of potential future attack attempts.
An added benefit: the system minimizes the number of alerts SOCs need to investigate, allowing them to focus on more pressing threats.
Secondly, provide better outcomes for our customers by integrating technologies across our products. As an example, we’ve consolidated the agents between Web Security Service (WSS) and Symantec Endpoint Protection (SEP). Agent consolidation is critical in maintaining lower operational costs, better security posture and better protections. A single agent for Endpoint Prevention, EDR and WSS allows for easy deployment among the products, less time to manage agents and increased protection as it is easier for the products to work together to detect and block threats.
The upshot: Customers get to use security products that complement each other and get more effective security at a reduced cost.
And third, we created a way to integrate across our platform, including third-party solutions via Integrated Cyber Defense Exchange (ICDx). It is a data exchange technology for sharing events and intelligence across Symantec and third-party systems. Before ICDx, customers needing protection across various control points had to engineer their own “glue” to collect telemetry across control points and normalize it so they could correlate that telemetry. With ICDx, customers essentially get “plug and play” data normalization, centralizing threat telemetry for better threat hunting.
We reached out to the broader industry to create an open ecosystem so technology partners can deliver essential integrations with Symantec’s portfolio and customers can easily deploy and connect in Symantec’s and third party products together through ICDx. It’s up to customers to choose what fits best for their environment. Whatever their solution is, our integrations will drive toward the common goal of building a more robust security ecosystem and help customers blunt the attempts of adversaries. The upshot: Customers get to use security products that complement each other and get more effective security at a reduced cost.
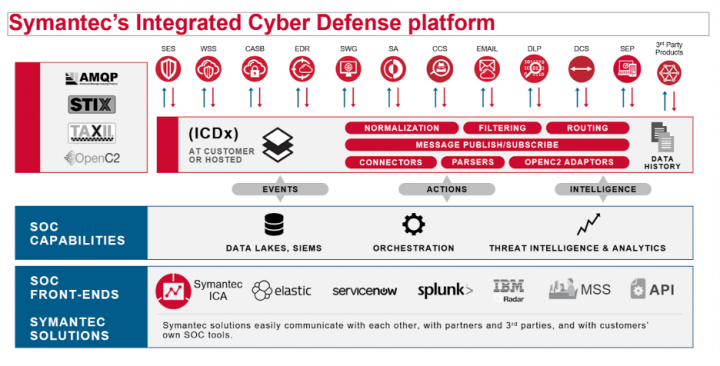
For example, multiple Symantec products are currently integrated with multiple 3rd party solutions such as SIEM, SOAR and TIP. Splunk, Cybersponse and Anomali are some partners we have integrated using ICDx as the single integration point across the portfolio.
ICDx simplifies the integration which drives better intelligence, monitoring, and stronger cyber risk management and reporting.
For overworked SOC analysts who spend a lot of their time trying to configure disconnect, point security tools instead of investigating and analyzing threats, ICDx simplifies the integration which drives better intelligence, monitoring, and stronger cyber risk management and reporting.
Three Security Pillars of Strength
Symantec’s approach to building an integrated platform rests on three important security pillars: evolving threats, digital transformation and privacy and compliance.
Evolving Threats: The basic idea is that integrating information from multiple solutions - whether on-prem or cloud based – simply offers better threat visibility. It also affords customers a far greater opportunity to conduct correlations and apply threat intelligence to identify and catch threats they might otherwise have missed had the products not been integrated properly. It also reduces response times between the time a suspicious file gets identified and the time it gets blocked.
Digital Transformation: As more companies transition from on-prem solutions to cloud and SaaS-based services, they face new challenges and requirements as they set up their environments. More than ever, that means they’ll need solutions working together to help them successfully engineer this transformation in a secure way. They need the ability to understand who's accessing what types of data and from where. That's where Integrated Cyber Defense integrations, such as Symantec Web Security Services (WSS) and Symantec Cloud Access Security Broker (CASB), for instance, provide secure access as enterprises set up proper policies for this new era of corporate computing.
Privacy and Compliance: Organizations need to be able to store and retrieve data from different places. What’s more, PII data is going to get treated differently than non-PII data. Organizations need to set proper access rules and also decide where the information gets stored. Will they use a public cloud? A non-public cloud? A hybrid approach? These are key decisions that each company must decide. Similarly, they need to account for privacy considerations. This can get complicated quickly as different regions around the country and globe have different regulations, so they need to make sure that they’re following the local rules governing privacy. With integrated cyber defense, there’s no longer guesswork involved. The platform offers a way to handle data in a normalized and centralized way, allowing for field filtering, types of events and forwarding to the right destinations.
Platform Power
With every new breach, we get another reminder that no single technology is going to adequately protect an enterprise against all cyber-security risks. That’s where our ICD platform is answering the challenge in a way that sets it apart from the legacy security approaches that still predominate in some corners. What’s more, this isn’t a “one-and-done.” In the months and years ahead, we’ll continue to invest in our platform as we extend ICD’s capabilities and integrations even further.
If you have 2 or more Symantec solutions - you can download ICDx for free HERE

Symantec, a Division of Broadcom, Ranks Best-in-Class on CRN’s 2020 Annual Report Card
Solution Providers Recognize Symantec as a Top-Class Channel Provider of Data Security









We encourage you to share your thoughts on your favorite social platform.