Streamlining ZTNA Administration
The cornerstone of ZTNA transformation
When it comes to network security, every minute counts. Time spent on administration takes skilled threat hunters away from focusing on threat investigations and stopping attacks. Finding ways to streamline administration is like discovering a hidden treasure chest. With the advent of Zero Trust Network Access (ZTNA) and its promise of heightened security, implementation certainly introduces opportunities for stronger security but also can create anxiety around increased administration tasks…at least that may be the perception. The reality is far from that. The quest for streamlined administration is actually the cornerstone of ZTNA security.
Security teams face numerous challenges in managing and maintaining secure access to resources. The rise of ZTNA as a transformative approach to network security helps organizations seeking ways to simplify administration, while ensuring robust protection. However, the transition from traditional VPNs to ZTNA introduces complexities that require careful consideration and strategic planning. But the effort is worth it.
Security teams already deal with a lot of VPN maintenance, including user provisioning, access control management, and troubleshooting, and it can be very time-consuming. The shift towards ZTNA, if not done properly, can make administration even more intricate because of the adoption of the "least privilege" model.
ZTNA's "least privilege" model emphasizes restricting access to resources based on specific user roles and conditions. While this enhances security, it can add complexity to administration. Implementing least-privilege access requires constant monitoring and adjustment to accommodate changes in user groups, applications, and access conditions. This ongoing maintenance work can strain resources and create bottlenecks for security administrators.
The quest for streamlined administration is actually the cornerstone of ZTNA security.
To effectively address these challenges, organizations must rethink their approach to administration. One key strategy is to delegate administrative privileges to individual teams or projects, offloading the burden from the central administrator. By empowering teams to manage their access permissions, organizations can streamline administration and improve efficiency.
This concept is exemplified by Role-Based Access Control (RBAC), which enables organizations to assign control over specific environments to different teams based on their roles and responsibilities. RBAC enables teams to autonomously manage access permissions within their designated scope, reducing dependency on the central administrator and fostering a more agile and responsive security posture.
By embracing RBAC and empowering teams to take ownership of access management, organizations can achieve a balance between security and efficiency in their ZTNA implementation. Delegating administration privileges enables teams to adapt quickly to changing requirements and reduces the administrative burden on centralized security resources.
But what about the administration of RBAC? Symantec has an answer.
ZTNA Collections – Easing Administrative Burden
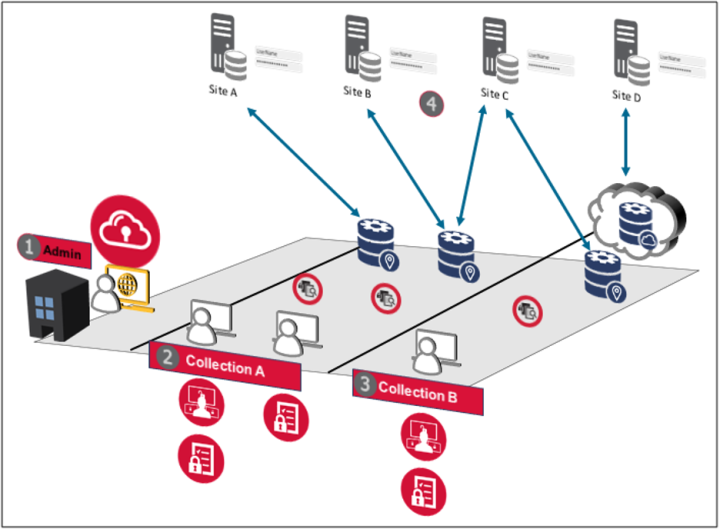
The Symantec ZTNA team has engineered an ingenious solution to streamline administrative maintenance and supercharge business operations. The feature called “Collections” is an effortless system designed to distribute maintenance tasks across multiple teams, individuals, or machines while enforcing the principles of least privilege control. With Collections, SecOps teams can enjoy a hands-free experience, freeing up valuable time and resources for strategic initiatives.
So, what exactly are Collections? Think of them as administrative boundaries that define a set of resources and grant permissions to users, groups, and API clients for specific applications and policies. Essentially, Collections empower administrators to delegate "mini tenant" responsibilities to individual teams, radically reducing the maintenance effort associated with managing access controls.
Imagine a scenario where each department within your organization has its own Collection, tailored to its unique requirements and access needs. Marketing, finance, HR – each has its own dedicated space within the ZTNA ecosystem, allowing teams to autonomously manage their access permissions without relying on centralized oversight. This not only streamlines administrative tasks but also promotes agility and collaboration across the organization.
Using the Collections feature, the days of manual access management and cumbersome administrative overhead are a thing of the past. Say goodbye to tedious policy configurations and hello to a more efficient, scalable, and secure approach to network access control. Whether you're a small startup or a global enterprise, Collections can revolutionize the way you manage and maintain your ZTNA infrastructure, paving the way for a more seamless and productive future.
Deploy ZTNA and Streamline Secure Access
Simplifying administration is essential for the successful implementation of ZTNA. By leveraging RBAC and delegating administration privileges to individual teams, organizations can navigate the complexities of ZTNA while maintaining robust security controls. By embracing this approach, organizations can enhance efficiency, agility, and resilience in their security operations, paving the way for a more secure and productive digital environment.

No One is Immune
Microsoft, HPE, and the need for data-centric security








We encourage you to share your thoughts on your favorite social platform.