Defeating the Monster (Part 2)
How Symantec Products Use Symantec Cloud Sandbox
Monster Stealer is an example of a Malware-as-a-Service (MaaS) Infostealer. In part one of this blog we looked at how Monster Stealer works and how Symantec Cloud Sandbox detects unknown variants of the malware. In this blog we look at how two Symantec products use the Symantec Cloud Sandbox.
How Email Security.Cloud Uses the Sandbox
In addition to blocking known threats, ETDR sends copies of files of interest to the Symantec Cynic cloud service. Cynic launches these files in the Symantec Cloud Sandbox. Cynic then correlates the data with data from the Symantec Global Intelligence Network to determine if the files are malicious.
Below is an example of Symantec Cloud Sandbox detecting Monster Stealer before it reaches the user via Email Security.Cloud.
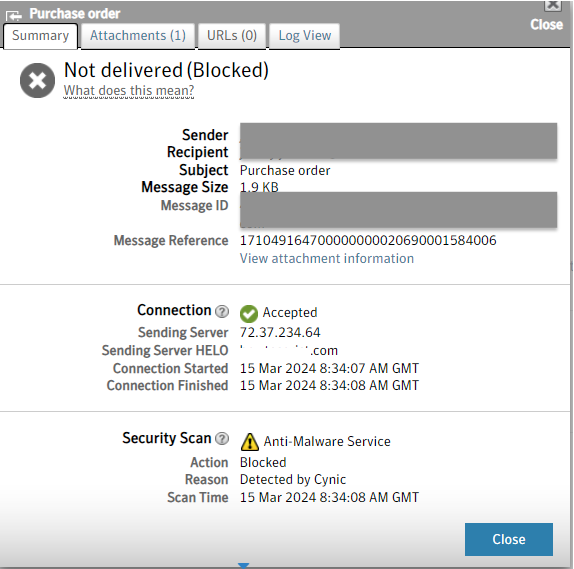
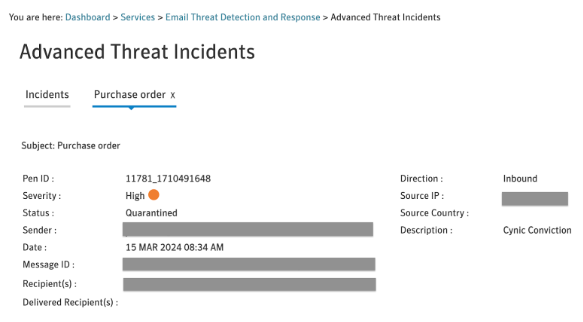
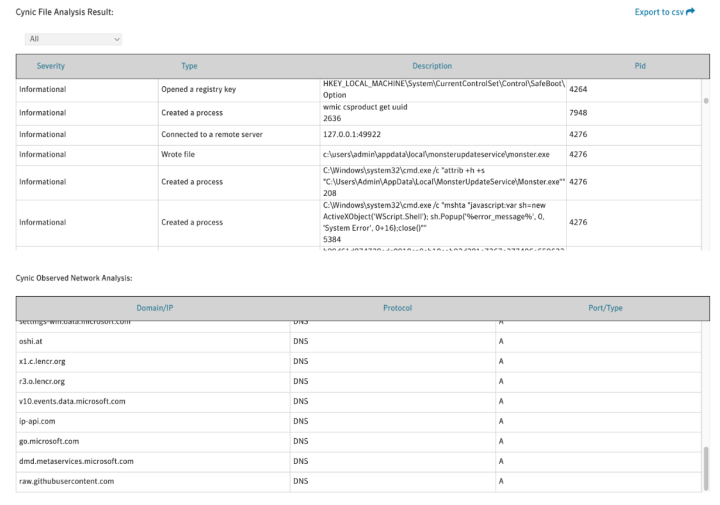
Details from the detonation are also provided, providing insight into the attack vectors.
How Symantec Endpoint Security Complete Uses the Sandbox
Symantec Cloud Sandbox is provided as an enrichment for Symantec Endpoint Security Complete. A file will be submitted to the sandbox in parallel to the file execution on the endpoint. It is possible that Symantec Endpoint Protections’s behavior, memory exploit mitigation and/or network IPS/Firewall components may have contained the threat. But either way, the sandbox conviction event is elevated and added to an Incident. The Incident exists to direct the security admin team to investigate and determine what actually happened on the endpoint in relation to this file.
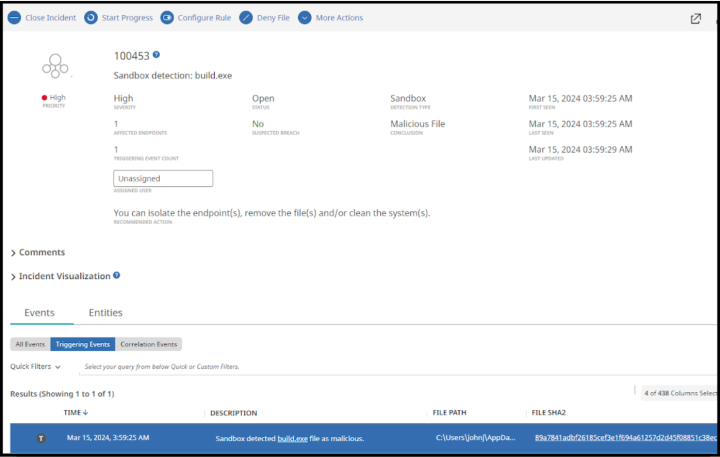
The Investigation will enable the security admin to understand how the file arrived, what activity it took (if any) and determine what security controls could be put in place to prevent the threat vector from being used in the future. Submitting files to the sandbox
The sandbox conviction event itself is effectively a meta-data event to draw attention to the conviction action. The File entity referenced by the conviction event will have a “Sandbox results” tab that includes all of the activity observed for the process when it ran in the sandbox. The events enriched with the field “Severity:5-Critical” identify the actions considered most important for the malicious disposition.
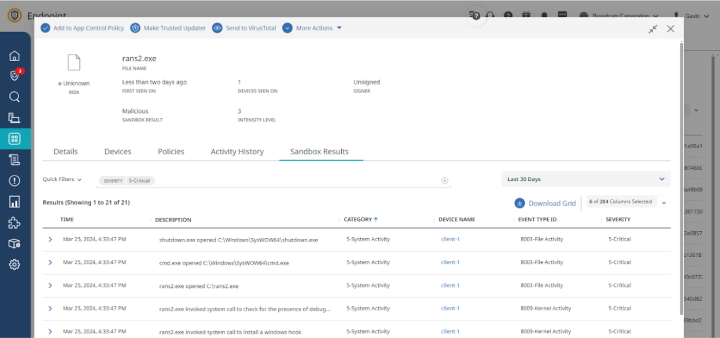
But the full activity is recorded in our standard ICD schema for an analyst to review.
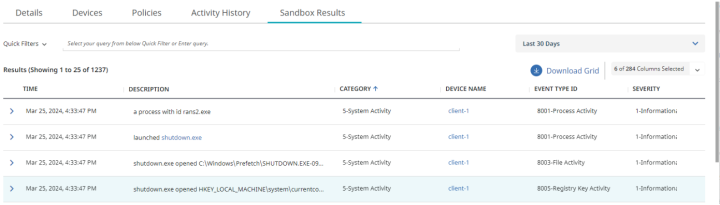
Conclusion
While the example above is specific to the Monster Stealer MaaS family, the advanced heuristics available in Symantec Cloud Sandbox can detect and alert on complex and customized attacks. When paired with Email Security.Cloud, Symantec Cloud Sandbox can identify these threats before they can even be launched. And with Endpoint Detection and Response, Symantec Cloud Sandbox can provide high-context visibility and alerts on potential attacks in the network.
Learn about the Endpoint Detection and Response feature of SESC: https://techdocs.broadcom.com/us/en/symantec-security-software/endpoint-security-and-management/endpoint-security/sescloud/Endpoint-Detection-and-Response.html
For instructions on how to enable Symantec Cloud Sandbox, please refer to: https://techdocs.broadcom.com/us/en/symantec-security-software/email-security/email-security-cloud/1-0/about-email-anti-malware/about-email-threat-detection-and-response.html










We encourage you to share your thoughts on your favorite social platform.