Super Users Need Super Protection
Accounts with super privileges require modern defenses
This is a blog from a Broadcom Knight, part of an elite group of Partner Technical Professionals who have demonstrated technical expertise in Broadcom’s products and are recognized as experts in their field.
As we all know, companies today rely on a range of systems, applications, databases, networks, firewalls and more. Yet only a few people are responsible for managing, maintaining and safeguarding these critical components that are so essential to business operations.
Because accounts with super privileges are often prime targets for attackers, they represent a unique risk to organizations. Unfortunately, many companies realize that privileged accounts require extra protection only after they’ve suffered a successful attack.
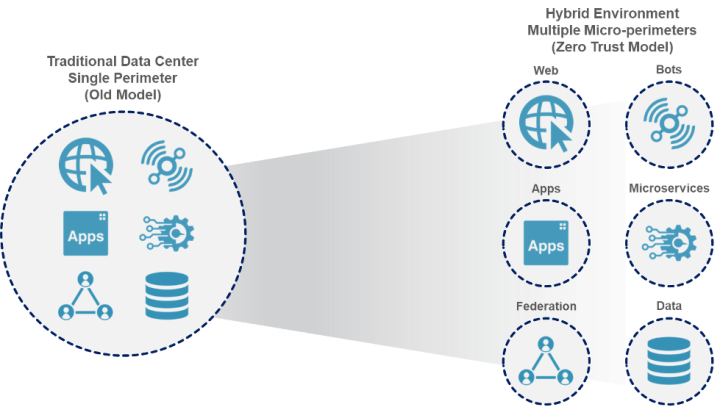
They also discover that outdated, single-perimeter cybersecurity models are an ineffective fit for today’s threat landscape—and more modern, hybrid environments with multiple micro-perimeters provide protection designed to protect against modern threats. The following graph illustrates the evolution of these models.
While perimeter security remains crucial for companies, it’s essential to recognize that securing critical components requires a layered approach with multiple robust solutions at each layer. The following graphic illustrates a security scheme for privileged accounts in a company.

5 benefits to a layered approach
When companies implement a solution to manage privileged accounts, they typically transition to a layered assurance model that is independent of the cloud hosting their critical applications. That approach comes with benefits that protect the user, the account and the organization. They include:
- Credential custody: Privileged credentials, such as passwords, are vaulted and encrypted within the solution. They can be rotated based on defined schemes to meet the complexity requirements of each application. Stronger authentication mechanisms can also be required before granting access to these passwords.
- Session recording: It’s often challenging for operations to gather evidence of activities across various infrastructure components and systems. Recording sessions of these activities aids in identifying potential issues resulting from changes. From a forensic standpoint, this data is key for thorough analysis if needed.
- Simplified login: Managing numerous users, clients and passwords for critical business infrastructure components can be a headache. However, a simplified single sign-on (SSO) panel where users can access what they need with just a single click—without the burden of remembering credentials—simplifies the day-to-day tasks of administrators.
- Policy controls: In many organizations, diverse environments with various types of applications, systems and platforms can lead to inconsistencies when applying least-privileged access controls. Not all administrators require identical access levels, with requirements varying at different times. Privileged Access Management (PAM) solutions should enforce granular controls to ensure separation of duties and just-in-time provisioning. These capabilities apply Zero Trust principles across all areas of the enterprise, from databases to cloud platforms and edge computing.
- Threat mitigation: Behavioral analytics and modeling bolster security by assessing activities in real time against historical usage patterns, identifying potential risks of unauthorized access. When usage or activity reaches predefined thresholds, automated mitigation actions engage so teams can respond faster to attacks than they could if they were simply relying on traditional security alerts.
Strategies that effectively safeguard critical operational IT assets is a must for every company. This includes employing solutions that help administrators manage privileged credentials with granular yet flexible controls. By implementing these solutions, your organization can mitigate the risks associated with unauthorized access to vital systems and sensitive data, including potential financial and reputational damage. That's why investing in a robust PAM solution is not just wise—it's essential.

5 Top EDR Use Cases
When preventative measures fail, these five actions can save you








We encourage you to share your thoughts on your favorite social platform.