Defeating the Monster
Stopping Monster Stealer with Symantec Cloud Sandbox (Part 1)
Infostealer trojans are designed to stealthily gather and exfiltrate sensitive data. This data can then be monetized or used for staging large-scale targeted attacks. Monster Stealer is an example of a Malware-as-a-Service (MaaS) Infostealer: a malicious tool customized and sold for specific and targeted data theft. Monster Stealer has been associated with PrivateLoader, a larger MaaS suite sold to infect targets with malware, including ransomware. Each version of Monster Stealer is a unique file, delivered by unique malware, and used for different purposes.
MaaS malware presents a challenge to traditional detection methods as the files and behaviors will differ with each targeted distribution. Using a new behavioral classifier in Symantec Cloud Sandbox, Symantec created flexible detections for the Monster Stealer family. It starts by monitoring the IOCs listed. But rather than simply detecting the presence of IOCs, it looks at how they are being used and makes determination of the ultimate purpose. All permutations are tracked and evaluated.
Detecting and blocking complex attacks
Complex attacks, such as Monster Stealer, use multiple files, processes (including LOLBins), and network connections to infiltrate, persist, steal information, and exfiltrate gathered data.
Symantec Cloud Sandbox detonates potential malware in a safe and controlled environment. It employs multiple, leading-edge security engines to inspect and analyze the vectors of the attack (e.g. files, processes, network activity, and system behavior). These vectors can often reveal suspicious behaviors that appear to be Indicators of Compromise (IOCs).
However, these behaviors could also be legitimate software. On a live machine, it can be difficult to differentiate attack behavior from normal background activity. For example, a system administrator running diagnostics looks very similar to an attacker probing for system information. Typical behavior-based protection technology can block legitimate software or allow variants of Monster Stealer to run for fear of a false positive. Because the sandbox environment is completely controlled and predictable, we can tune these security engines to aggressively target these IOCs in the absence of legitimate background noise.
Because Monster Stealer can be customized, the behavior can differ widely from one attack run to another. However, there are core IOCs that are critical for a successful attack.
Unique to the sandbox is a new behavioral classifier that identifies the minimal IOCs in combinations that are necessary for core aspects of the malware’s purpose. This provides robust detection for complex malware families that are customizable and hide behind potentially legitimate behavior.
The Monster Stealer Attack Chain
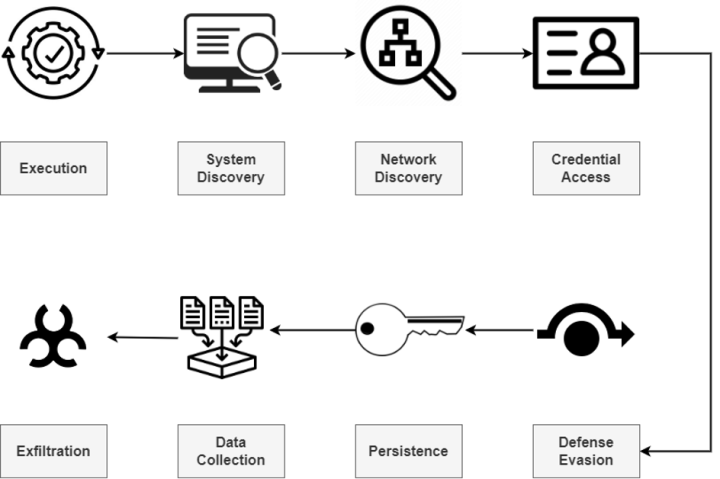
Execution: The initial code execution.
build.exe is attached in a phishing email. On execution, build.exe drops and launches stub.exe which uses various system tools to gather information.
System Discovery: Gather information about the endpoint
stub.exe launches multiple system tools such as ‘wmic’, ‘net’, and ‘sc’ to gather information on the OS, user accounts and groups, etc… and writes these to a file on disk for later retrieval.
Running processes and services are also enumerated to identify security software.
Network Discovery: Gather information about the network
stub.exe launches multiple system tools such as ‘netsh’ and ‘ipconfig’ to gather information on the IP address, network connections, and firewall configurations and writes these to a file.
Credential Access: Gather information that can be used to identify and/or validate a user
stub.exe locates and steals web browser user data, social media data, game data, history, and credentials and writes these to multiple files.
stub.exe also steals the session cookies for later use
Defense Evasion: Bypass security software and OS safeguards
stub.exe utilizes the list of running processes/services in the System Discovery phase to disable security software.
Persistence: Add one or more persistence points to automatically restart the attack periodically or after a reboot
build.exe copies itself to Monster.exe and creates a run key in the registry to relaunch after reboot.
build.exe also creates multiple scheduled tasks to re-launch Monster.exe on timed intervals.
Data Collection: Gathering sensitive data from the user session
Powershell.exe is used to gather screenshots and copy information from the clipboard.
The session cookies stolen in the Credential Access phase are now used for Browser Session Hijacking.
Exfiltration: Send collected data to the attacker
All collected data is uploaded to the attacker
Symantec products can use the verdict from Symantec Cloud Sandbox to provide robust protection. In part two of this blog we’ll look at how Email Security.cloud and EDR detect Monster Stealer and other custom MaaS malwares using this information.

Better Together
Third party validation already exists










We encourage you to share your thoughts on your favorite social platform.