Understanding Risk with People, Processes and Technologies
Symantec helps you manage your business for greater success
Risk is an issue that everyone has to acknowledge and deal with, whether it is financial risk, safety and most importantly in our opinion: cyber security risk. You need to understand what your risk is in order to prioritize your efforts to mitigate it to an acceptable level. As enterprises implement their information security programs, they have to look at people, processes and technologies for effective programs. Symantec is committed to assisting our customers in the implementations of their information security programs.
While information security programs involve people, processes and technologies, let’s concentrate on the people aspect. Certain actions, whether well intended or not, present a risk to an organization’s information. These risks could lead to a data loss event or potentially a disruption of service, further leading to damage to the organization’s reputation. In order to protect against their actions, you need to understand the user’s actions and behaviors. Understanding what your users are doing and comparing them to others in your organization gives you insight that can help you decipher who the outliers are. These outliers could be unusual authentication events indicating a potential compromised account, downloads of sensitive information to a personal device, uploads of information to a personal cloud account, or broken business processes that go against corporate policies. With this understanding, you’ll be able to develop your plan and prioritize efforts to mitigate the risk.
Symantec is committed to assisting our customers in the implementations of their information security programs.
The context organizations need are often provided by user and entity behavior analytics solutions. According to Gartner, a technology research and consulting company, “User and entity behavior analytics (UEBA) solutions use analytics to build the standard profiles and behaviors of users and entities (hosts, applications, network traffic and data repositories) across time and peer group horizons. Activity that is anomalous to these standard baselines is presented as suspicious, and packaged analytics applied on these anomalies can help discover threats and potential incidents. The most common use cases sought by enterprises are detecting malicious insiders and external attackers infiltrating their organizations (compromised insiders).”
Reinforcing our UEBA functionality
At Symantec, as part of Broadcom Software, we are making significant enhancements to our UEBA capability in CloudSOC, our Cloud Access Security Broker (CASB). We will be using the deep expertise of our Information Centric Analytics to provide enhanced functionality for our CloudSOC customers. The initial capability will help our CloudSOC customers understand who their highest risk individuals are so they can prioritize their efforts and put controls in place to mitigate risk presented by their users.
On the Detect page (Users), you’ll see three columns on the bottom half of the page. The purpose is to convey who the riskiest individuals are in general, and then take a look at individuals from a policy violation perspective and from a user actions perspective. The columns will have a ranked listing of individuals for each category.
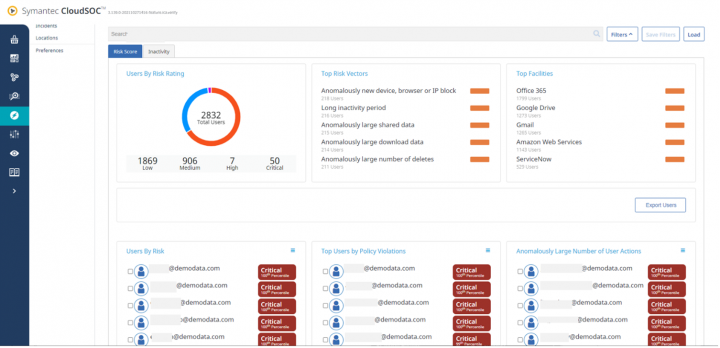
Risk is not static though. This is especially true when considering individuals’ behavior. As you educate individuals to understand security policies and modify their behavior to comply better, or put controls in place to limit access, or prevent actions, you will see a reduction in risk posed by those individuals but someone else rises to the top. So, understanding how an individual compares to his or her peers and to the overall organization is important. An individual’s ranking is dynamic and so dealing with the risk presented is an ongoing effort.
Within CloudSOC, there will be new concepts and terms introduced that will help organizations see the rankings of their individuals. It is not just a score, but how individuals are creating incidents as they relate to other individuals.
- Risk percentile. This is determined by comparing the risk score to all other risk scores for that entity type.
- Risk rating. This is an analysis of an individual or entity’s behavior and then compared with other individuals or entities within the organization. The risk ratings are critical, high, medium, low and unrated. Other than unrated, these rating category thresholds are configurable. The intent of these ratings is to quickly show who the security team needs to deal with sooner rather than later.
- Risk vectors. Risk vectors are used to calculate risk scores. Risk vectors show the activities that determine the risk rating. These risk vectors can be weighted so that customers can put emphasis on events they deem more critical to their security program. For example, if data loss prevention is more important, customers can weigh DLP incidents more heavily. In essence putting a lens on that category of events. The risk score that is produced is a sum of all weighted scores for that entity.
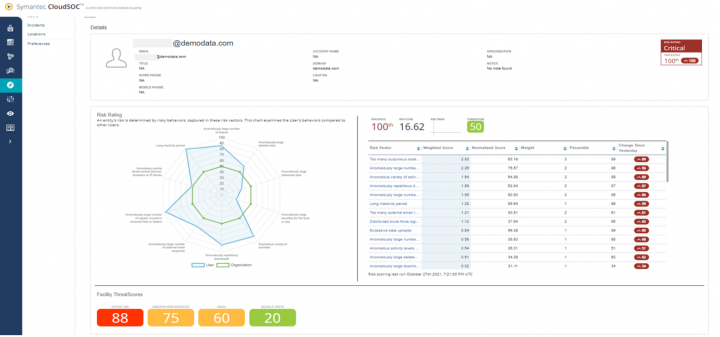
We’ll be introducing a User Details page. When you click on an individual from the Detect page, it will take you to that individual’s page. The details page is meant to provide one page with pertinent information so that security analysts can see what is causing the user to be risky. They then can take actions to triage those incidents.
The radar graph on the User Details page replaces the threat tree. It is a display showing the risk vectors associated with the entity and shows their behavior compared to the organization. This will help easily identify if the individual is an outlier and potentially requiring attention.
In summary, Symantec is committed to helping our customers effectively manage risk to their information and the improvements that were discussed are the first steps in expanding our analytics capabilities in CloudSOC. Our solutions are a part of a robust information security program. Managing risk though starts with understanding where your risk is and who/what is creating it. Then it is a matter of putting control measures in place to mitigate it. Those measures are a combination of people, processes and technologies.

Symantec Secure Web Gateway - Product Update
A fireside chat with Symantec Product Management








We encourage you to share your thoughts on your favorite social platform.