The Tea Cup Security Conundrum, or How to Prevent Targeted Attacks
Endpoint Security protects against hard-to-find threats at every stage of the attack chain, blocking hackers from moving laterally and exfiltrating your network
Every morning, before going off to help cyber defenders save the world, I start my day with a nice cup of tea. This morning, as I accidentally poured salt instead of sugar in my cup, I realized something: I was staring at one of the major security conundrums of our day. Separating the crumbling salt from the water is impossible and the only way to completely get rid of it is to dump the entire cup out. Same goes for an organization facing a targeted attack, in which malicious actors are skilled enough to penetrate the network and use a variety of techniques to move laterally, evade detection, and wreak havoc. Even if you found the machine on which the initial breach happened, the only way to get rid of an attacker’s privileges and persistency once they are inside is to rebuild the entire network from scratch.
The Targeted Attack Challenge
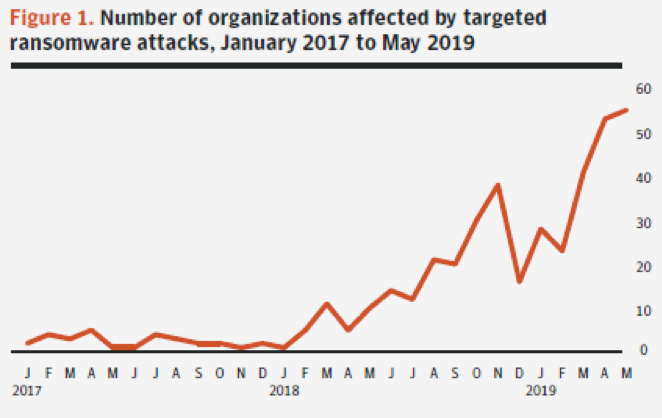
In the cyber threat landscape today, we’re increasingly seeing sophisticated targeted attacks on organizations, with these attacks growing more extensive, both in techniques and impact. Targeted ransomware, a type of targeted attack with a particularly lucrative payout for hackers, continues to be one of the biggest cyber crime challenges facing enterprises. According to Symantec’s Internet Security Threat Report on Targeted Ransomware, the number of businesses affected by these attacks has grown dramatically since 2017 – back then we saw a mere two organizations a month being attacked. Fast forward to 2019, and we’re seeing over 50 companies a month hit by targeted ransomware. Some attacks have resulted in thousands of computers being encrypted and sensitive data being stolen, leading to loss of business, reputation harm, and millions of dollars in clean-up costs.
With hackers seeking to reach and encrypt as many machines as possible in an organization, recent targeted ransomware attacks have seen malicious actors use a range of methods and tools to move laterally through a network. These include evolving living off the land techniques in which hackers use operating system features and tools already installed on targeted machines to traverse the network. The benefit for attackers is that they don't need to create as many or even any files on the hard disk, thereby reducing the chance they’ll be detected by traditional security tools. Frequently used living off the land techniques include: dual-use tools such as PsExec, which allows execution of processes on other systems; file-less tools such as Mimikatz, which is used to escalate privileges; and running PowerShell to execute commands and conduct reconnaissance.
The Early Bird Catches the Hacker
Enterprise security teams are aware of the risk from targeted attacks, but they continue to struggle to stay ahead of the threat. There is a common misconception that there is enough time to stop attackers in the window between when they breach the first machine and when they begin moving laterally through the network. Some security vendors say this window can last for an average of two hours and suggest that you can remediate the threat within 60 minutes to stay ahead of it.
While some targeted attacks may be like that, others – that are becoming more common today – can obliterate your environment in minutes, and waiting 60 minutes will, frankly, leave you in the dust. When a global transport and logistics company was hit by the crippling NotPetya ransomware in 2017, the malware propagated across the network in just seven minutes. In another instances, NotPetya was able to infect 1000 machines in under two minutes.
To effectively protect against targeted attacks, you need to act fast and prevent threats as early as possible at every stage of the attack chain. Here are the phases of an advanced targeted attack, according to the MITRE ATT&CK framework:
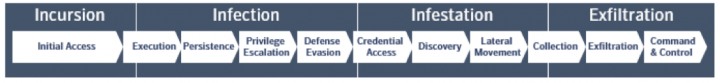
Because hackers are persistent and often move rapidly across the attack chain, you can’t afford to wait for a breach to occur before taking any action and you certainly can’t rely on manual response techniques. The only way to combat these advanced threats is to make the enterprise resilient to attacks as early as possible, even in the pre-attack phase, by reducing the attack surface. If hackers find a way in, thwarting them at the endpoint, before they have a chance to persist on the network, is critical.
The Symantec Endpoint Security Approach
That’s why at Symantec, we focus on providing protection not only across the entire MITRE ATT&CK chain, but beyond it, at the pre-attack and post-breach stages – with prevention and remediation as early as possible. To this end, our Endpoint Security platform is built on four pillars: Attack Surface Reduction, Attack Prevention, Breach Prevention, and Endpoint Detection and Response (EDR). Across these pillars, Symantec Endpoint Security delivers the deepest protection with the broadest coverage, and with the widest deployment options, via a single agent and unified management.
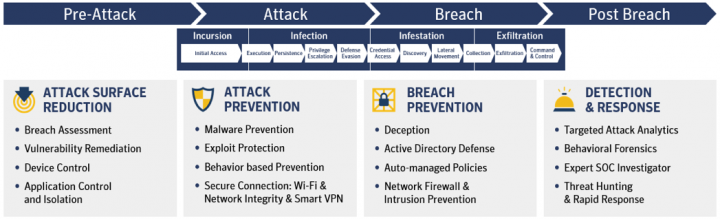
Attack Surface Reduction
This pillar covers measures we can take ahead of time to make organizations more resilient to attacks. This includes implementing pre-emptive advanced policy controls and technologies that mitigate vulnerabilities in applications, Active Directory and operating systems. Breach Assessment, a capability unique to Symantec, continuously works in the background to gather information about Active Directory configurations, privileged accounts, security settings, and more. We also use risk intelligence on known vulnerabilities to prioritize response, ensuring the most serious threats are remediated first.
With Device Control, App Control and Isolation Policies, admins can limit the ability of users or apps to introduce malware from outside of the corporate environment, minimizing the risk of exfiltration. Admins can control file, registry and device access, and use application whitelisting to allow known-good apps to run, while isolating unknown apps so they can’t execute malicious code on machines.
Attack Prevention
Our prevention stack includes malware prevention on workstations and servers, Mobile Threat Defense (MTD) for iOS and Android devices, and Network Integrity for modern operating systems (Windows 10, Windows 10 in S-mode and Windows on Arm devices). These tools use ML and AI-based detections to effectively protect against file-based and fileless threats at the device, OS, and app levels.
To block attackers at the Incursion and Infection stages of the ATT&CK chain, we use tools such as: advanced ML for pre-execution detection and protection against known and unknown threats, reputation analysis to determine the safety of files and websites using Symantec’s GIN, suspicious file behavioral monitoring, and memory exploit prevention to block zero-days in vulnerable applications and software. Additionally, our Secure Connection capability prevents network-based threats on roaming devices, by securing Wi-Fi connections with an automatic VPN.
Breach Prevention
If an attack has managed to bypass all attack prevention controls, it attempts to breach the enterprise by either moving laterally (east - west) or contacting a command and control server (north - south) to further advance infection or exfiltration.
A common technique used by attackers to move laterally is manipulation of Active Directory for high-privilege credential theft. Endpoint Security identifies such breach attempts by using deception techniques such as fake files, credentials and web requests to lure attackers in. By obfuscating to distort the attacker’s perception of an organization’s AD resources from the endpoint, it ensures early containment and prevention of the breach. Additionally, we use Network Firewall and Intrusion Prevention and IP blacklisting to prevent data exfiltration and hackers’ communication with command and control servers.
Endpoint Security is the only solution that blocks hackers where a breach starts – at the endpoint – before they can utilize Active Directory to get to other assets and achieve persistence.
Detection and Response
Even if you found a machine that was breached in an attack, and completely destroyed it, attackers generally infect multiple endpoints in an organization and may leave them in sleeping mode. These dormant machines are difficult to find, which is why Endpoint Detection and Response (EDR) is critical. Symantec’s EDR, combined with expert SOC analysis, provides incident responders with complete visibility into attacker activity on the device. Using real-time cloud analytics that can identify the stealthiest targeted activity, responders can quickly investigate and close out incidents to minimize attack impact.
Our Targeted Attack Analytics is a foundational element for preventing attacks because automation ensures we can respond within seconds or minutes. Our researchers analyze telemetry from more than 175 million endpoints secured by Symantec to provide insight on attackers, techniques, impacted machines, and remediation guidance. Our Threat Hunting tools include built-in playbooks with best practices for anomalous behavior detection. Lastly, Rapid Response takes direct action on the endpoint for remediation.
How Symantec Prevents GoGalocker and APT28
Now that I've gone over our protection stack, let’s see how some of these capabilities work in action. I take GoGalocker and APT28 as an example of targeted attacks. In the sections below, I show which techniques these attack groups use, and how Endpoint Security blocks the hackers at each stage of the attack chain.
GoGalocker
GoGalocker, a highly-disruptive targeted ransomware family that appeared in early 2019, has attacked organizations in a range of business sectors. In March 2019, Norwegian aluminum giant Norsk Hydro revealed that it had suffered a ransomware attack appearing to be GoGalocker, crippling the company’s computers and operations. This and other targeted attacks like it, demonstrate the extent of damage sophisticated hackers can cause to business, quickly and covertly.
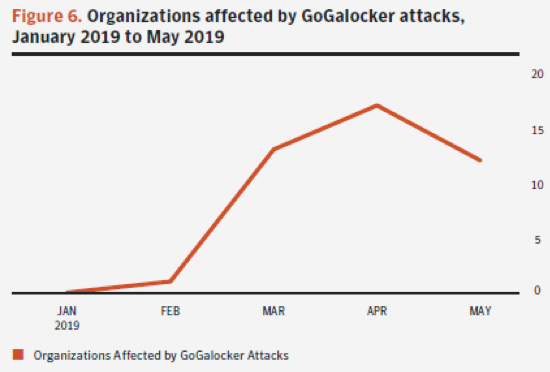
Below are the attack techniques GoGalocker has been found to use to infiltrate organizations and encrypt machines on a large scale. These techniques are mapped to the MITRE ATT&Ck framework.
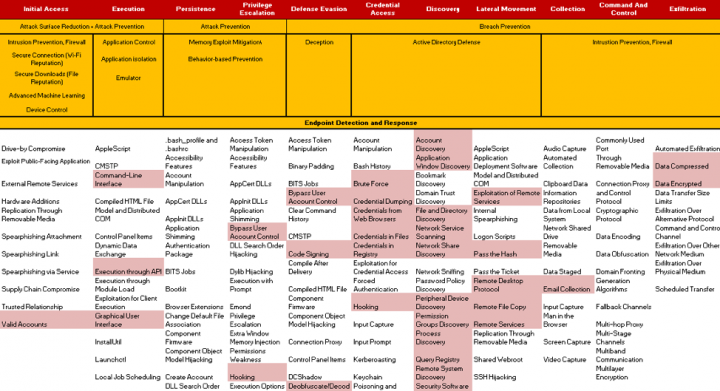
In a nutshell, once GoGalocker attackers manage to get into a victim’s network, they focus on mapping out the network and obtaining credentials to access other machines and escalate privileges. The attackers use popular living-off-the-land techniques to leverage resources in the victim’s environment such as Windows resources that can be used to run shellcode. They also use tools such as Mimikatz and PuTTY to disable security software and change privileges. Once the attackers acquire credentials, they proceed to spreading the ransomware. Lastly, they log off the current user, likely as a way to prevent anyone from logging in and stopping the encryption process.
Like many targeted attacks, the bulk of this ransomware’s activities are focused on credential theft and lateral movement. Symantec provides protection at every stage of GoGalocker’s attack chain. Techniques such as Intrusion Prevention and firewall block command and control setup by hackers; and Active Directory Security prevents lateral movement and credential access through obfuscation of an attacker’s AD perception.
APT28
APT28 is a threat family has targeted government, military and security organizations. The heat map below shows techniques used by APT28 to steal information.
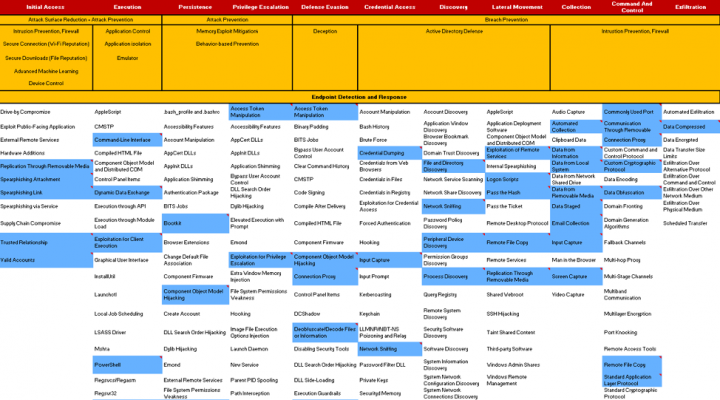
In order to gain a foothold in the victim’s environment, the hackers generally use specially-crafted spearphishing emails and bait individual users to open them. They may also use vulnerability scanning, waterhole attacks (exploiting legitimate websites to deploy malware), and zero-days for initial infiltration. Once inside, the hackers steal domain credentials using Mimikatz and Keyloggers, tools that steal credentials from browsers and email clients. Now that they’ve obtained credentials, which are used later to access other endpoints, they need to locate their targets. This is not as complicated as you may think. They ask Active Directory because that is where all the information about the resources is located. Think of it as an organization’s treasure map.
After they find their targets, they need to move laterally. Using legitimate services and Pass-The-Hash techniques with stolen credentials, they proceed to infect more endpoints. Lastly, after they’ve stolen valuable data inside databases, documents, and email, they exfiltrate the data.
Symantec protects against APT28 by covering every stage of the kill chain. In the initial access stages, we use our pre execution advanced machine learning for detecting malware based on static attributes. Throughout the execution phase, we used advanced heuristics and deep reputation data for on-execution threat prevention. We disrupt internal reconnaissance and stop lateral movement using Active Directory obfuscation, and block outgoing communication using IPS and laser-focused threat hunting.
Timing is Everything
The cyber security landscape has changed. Just like it’s nearly impossible to scoop out particles of sugar from a warm cup of tea, so too is it impossible to expel targeted attackers from your organization once they’re inside. Today’s hackers are moving fast and are more persistent than ever. They will follow the path of least resistance in your organization to find a way in. This includes using multiple entry points such as mobile, and quickly hunting for domain admin credentials once they are inside, to achieve total enterprise control. If that happens, the only way to get rid of them is to rebuild your entire domain. These attacks can happen in mere minutes – not hours or days – requiring defenders to prevent threats early across the attack chain, before damage is done.
Symantec Endpoint Security truly reduces, from beginning to end, the possibility of a breach in your organization, in an automated manner. We protect all operating systems and endpoints – traditional and modern – in your environment, in a single solution. You benefit from attack surface reduction, detection and prevention at every stage of the attack kill chain – the only way to be at the point of breach on time and prevent it.
In the next blog in our series about Symantec Endpoint Security, we'll discuss management architectures to help customers where they are: on-premises, and where they are going: the cloud.

Endpoint Defense Starts with Prevention
It’s no longer enough to discover and expel attackers as the dangers posed by endpoints continue to climb









We encourage you to share your thoughts on your favorite social platform.