SES Complete: Add To Your SOC Toolkit For Greater Visibility and Efficiency with Symantec
Symantec introduces new tools to improve SOC effectiveness
Security professionals know that it’s not the quantity of alerts that lead to better cyber security, it’s the quality. For Security Operations Center (SOC) staff, the major challenge is discerning which of these alerts are signaling a real threat to their organizations. It’s a challenge made even more daunting by the sheer number of threats the typical large enterprise encounters each day. Indeed, a 2019 survey of security analysts revealed that the average enterprise SOC receives as many as 10,000 alerts per day. For security analysts, two major problems loom as obstacles to their ability to separate the signals from the overwhelming amount of white noise: visibility and efficiency.
To get ahead of the ever more sophisticated and growing threat landscape, SOC analysts need greater visibility into the threats, their enterprise endpoints, and the data that will allow them to find the really critical threats to their organizations. They also need tools that will allow them to streamline their activities and focus on identifying and meeting these threats.
Security professionals know that it’s not the quantity of alerts that lead to better cyber security, it’s the quality.
The good news for security professionals and SOC teams is that Symantec, a division of Broadcom (NASDAQ: AVGO), has got your back. Enter Symantec Endpoint Security Complete (SES Complete).
SES Complete combines all of Symantec’s endpoint security technology including SEP - the industry standard in attack prevention, and adds Endpoint Detection and Response (EDR), Mobile Threat Defense, Active Directory Response, Application Isolation, Application Control, and Threat Hunting--all in one comprehensive package to protect all endpoints and all OSs, at one very cost-effective price. Making SES Complete even more exciting is that it offers an easy upgrade that requires no new agent to install, vastly simplifying the costs and complexity of deployment. Another exciting capability is that SES Complete offers our enterprise customers a fully cloud-based EDR solution that can be managed in cloud or on-prem.
SES Complete provides SOC teams with new tools for prevention and detection. New tools that arm them with the visibility and efficiency they need to do their jobs more effectively and to stop threats before they become worse as they move across the attack kill chain. Let’s take a look at some of these features now.
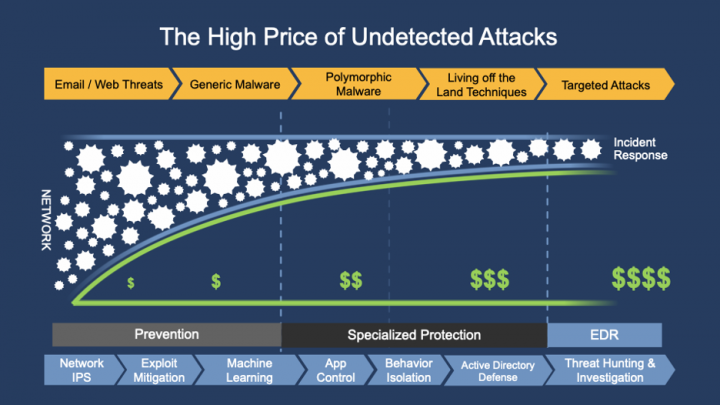
Machine Learning and Threat Hunting
As the graphic above illustrates, the longer an attack goes undetected, the greater the damage and cost to recover. It is critical for SOC teams to have full visibility over threats, and early detection and prevention. On the visibility front, SES Complete’s new features make it easier to identify threats. A capability even more important now with so many enterprise employees working from home -- and therefore more opportunities for cyber criminals to exploit. These new features augment the efforts of SOC teams to discover threats they may have missed seeing before.
An exciting new feature, Threat Hunter, further enhances the visibility of SOC teams to cut through the noise to prevent and detect threats. We know that every customer has a finite number of resources and people, and especially in their SOC. There is always a chance to miss something, particularly because customers are limited to data within their own organizations. Threat Hunter augments our customers’ efforts by combining input from our threat experts’ analysis enhanced with machine learning to expose more attacks.
With Threat Hunter, attacks that are discovered by Symantec’s expert analysts are shared with customers along with additional context. This ensures that critical attacks are quickly identified, and it accelerates investigations. The result creates a global threat intelligence network that augments each customer’s analysis by greatly expanding their knowledge of new and emerging threats worldwide. For customers, it also means gaining access and visibility to relevant threats other companies in the space are experiencing, which in turn aids in the early detection and prevention of threats in their own environment.
Greater Efficiency
On the efficiency side, SES Complete addresses the problem every SOC has with being overwhelmed by the sheer number of alerts. The volume of alerts creates its own inefficiencies as SOC teams are forced to ignore potentially devastating attacks and often fall victim to the “alert fatigue” brought on by the physical inability to investigate them all. Symantec’s focus has always been on determining the quality of the alerts, not the quantity. The new features integrated into SES Complete reinforce that security approach.
Behavior Isolation
Another new feature, Behavior Isolation, further helps SOC teams be more efficient, simplifying the path from alerts to investigation. Based on MITRE ATT&CK® technique detections, Behavior Isolation includes more than 75 configurable rules that can block attacks. Behavior Isolation also allows SOC teams to link back to the alerts that triggered the malicious behavior, ensuring they never have to deal with the same threat again. This is part of a powerful “detect to prevent” process where past detections lead to a stronger prevention policy. Every investigation can actually improve your endpoint security posture over time, by adapting the Behavior Isolation policy. No other vendor has done this because they treat EDR and prevention as two completely separate sets of tools rather than one fully integrated solution.
Example:
In this alert, an attack was carried out using a base64 encoded PowerShell script.
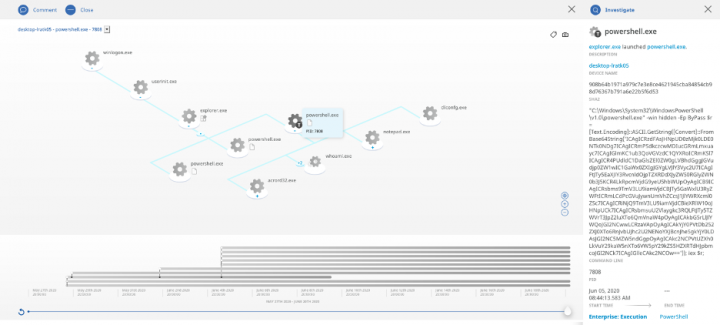
To prevent this type of attack from recurring in the future, or to prevent it from happening in the first place, the Behavior Isolation policy is configured to block this MITRE ATT&CK technique.
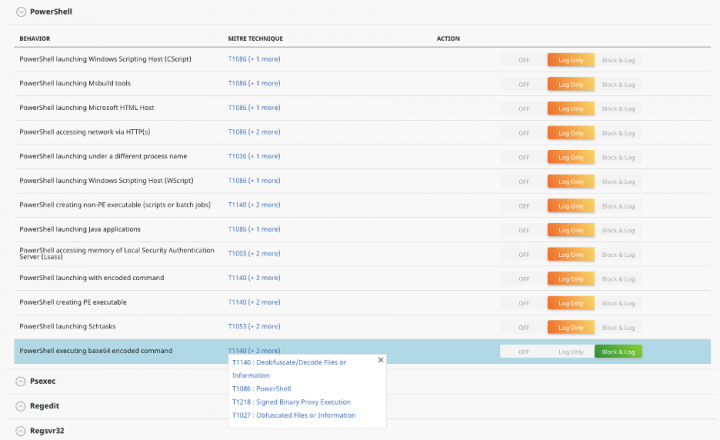
With new tools strengthening prevention and detection, Symantec Endpoint Security Complete is sharpening the SOC toolset by enhancing visibility into threats, delivering new efficiencies to work streams, and improving the effectiveness of customers to thwart critical threats to their organizations.
For more information, join me at our webinar on July 8 where SANS analyst Jake Williams and I discuss more about:
- One of the most powerful attack surface reduction tools and why it can be so useful in streamlining the SOC workload
- New detection and response techniques and tools that can help reduce alert overload and improve SOC performance

4 Secrets to Power Charge Your SOC - How prevention and detection can deliver new work stream efficiencies
In this session, SANS analyst Jake Williams and Endpoint Product Management Director Adam Licata discuss the four essentials of an effective endpoint solution and how prevention and detection tools join together to power charge your SOC.










We encourage you to share your thoughts on your favorite social platform.