Defending Against Black Basta Ransomware
A comprehensive overview of attack chain disruption with Adaptive Protection
Black Basta overview
Operating as a ransomware-as-a-service (RaaS), the ransomware group known as “Black Basta” was identified by Symantec in April 2022. Symantec has continuously updated detections since then for tools and techniques used by this group.
The ransomware utilizes an array of attack tools and malware including the Qbot Trojan, Rubeus, SharpHound, SystemBC, Mimikatz, Cobalt Strike and many more.
Black Basta can cause serious damage, including stealing data or preventing access to critical resources. Once active, the Black Basta attack can quickly pivot and spread throughout the network.
Using Adaptive Protection to Stop Black Basta
While Symantec always has current protection, additional prevention can be put in place with Symantec Adaptive Protection to help protect against lateral movement and ransomware execution techniques used by an attacker. Adaptive protection provides a self-learning, customized policy for tools like PowerShell, PsExec, WMIC, and BITSAdmin. By enabling suggested Adaptive policies, attack chains are denied access to vectors that are critical for their operations while allowing legitimate usage of these tools in day-to-day operations. Adaptive for SEPM customers.
Adaptive policies can be a powerful tool to disrupt a Black Basta attack at multiple points.
Black Basta: How Adaptive Protection can disrupt the attack chain
Below a diagram of the attack chain of one variant of Black Basta is annotated at the points in the attack chain that Adaptive Protection can disrupt. Details follow.
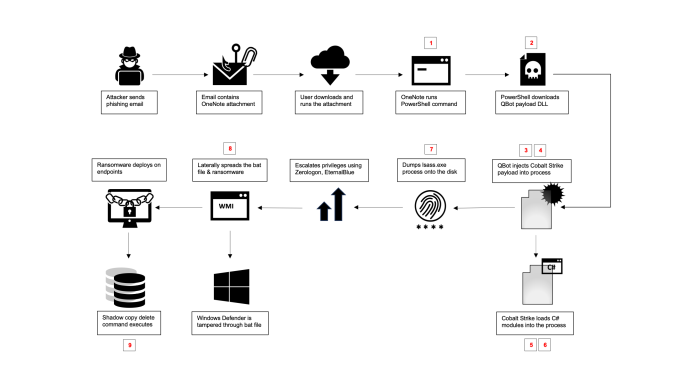
- Blocking the initial PowerShell execution: EncodedPowerShell commands are a common vector for hiding malicious actions.
Initial PowerShell base64 encoded command line can be detected and blocked by these Adaptive policies:
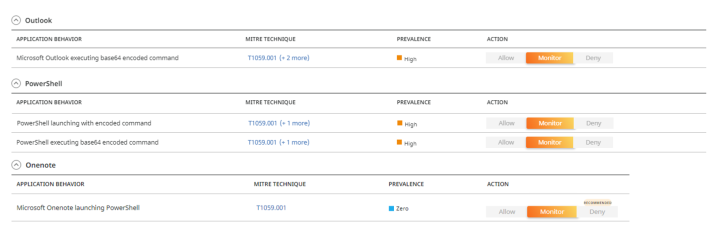
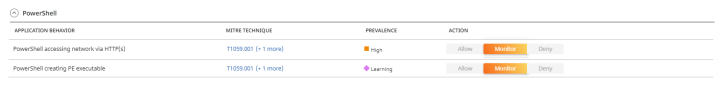
- Blocking the Qbot payload download and execution: PowerShell is often used in attacks to download and execute malicious payloads.
QBot DLL downloaded by PowerShell command can be detected and blocked by these Adaptive policies:
- Preventing initial compromise leveraging Qbot: QBot is deployed as a dll and executed by rundll32 to evade detection.
QBot DLL payload executed by rundll32 can be detected and blocked by these Adaptive policies:

- Stoping lateral movement by preventing discover actions: Qbot initiates a series of discovery commands to collect information about the environment. The following commands have been observed running within the environment.
QBot launching net commands for discovery can be detected and blocked by these Adaptive policies:

- Stopping Black Basta from establishing a persistent foothold: Persistence is required for any attack to continue over an extended period of time or across reboots. In this variant, a Scheduled Task is created to continue the attack.
QBot/Cobalt Strike establishing persistence can be detected and blocked by these Adaptive policies:

- Preventing the injection and execution of Cobalit Strike: In our investigations, we have detected the usage of Cobalt Strike and SystemBC by the actors to establish a communication channel with their command-and-control servers.
Leveraging the functionalities provided by Cobalt Strike, the actors were able to load and execute multiple tools directly from memory, harnessing the framework's inherent capabilities. Based on our engagements, we observed the attackers employing in-memory execution of tools like Rubeus, SharpHound, and other similar utilities.
QBot injecting into random window processes can be detected and blocked by these Adaptive policies:

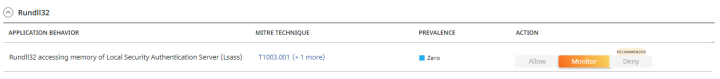
- Preventing credential dumping: Actors tried to dump the lsass process memory in attempt to gather additional credentials that can be later used for moving laterally in the network. The following command has been observed running within the environment.
rundll32.exe CSIDL_SYSTEM\comsvcs.dll, #+000024 796 \Windows\Temp\zSC7U.wpd full
- Preventing lateral movement by blocking remote exeution: Based on the information gathered from the preceding steps, the attackers employed “wmic” commands to execute their payloads. They initiated the execution by running a batch file script. Subsequently, they copied the ransomware payload to the “windows” directory and executed it remotely through “wmic”.
Black Basta using WMI for lateral movement can be detected and blocked by these Adaptive policies:

- Preventing loss of data by protecting the Shadow Copy: Historical analysis of the ransomware reveals that in older versions, the actors would employ the "vssadmin" command to eliminate the shadow copy, effectively removing a potential avenue for data restoration prior to encrypting the machines.
Black Basta deleting shadow copies can be detected and blocked by these Adaptive policies:

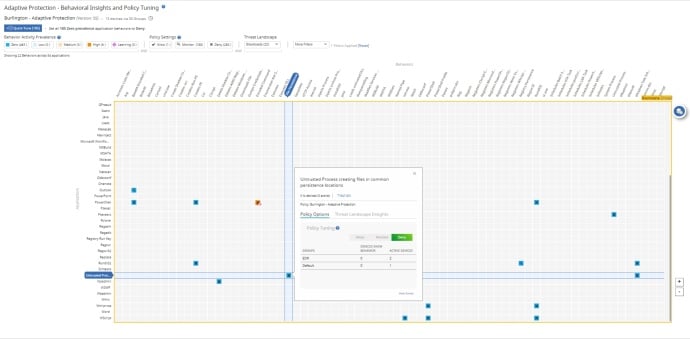
Adaptive Heatmap for Black Basta
Adaptive Protection shows which behaviors have been observed in your enterprise, helping administrators to distinguish which potentially dangerous behaviors can be blocked without interfering with ongoing business processes. Adaptive Protection has a 3 month, 6 month and 1 year look back period of these observed behaviors. The Heatmap below contains the current policies that can help disrupt a Black Basta attack.
Conclusion
While the examples above are specific to Black Basta, Adaptive Protection can be used to prevent any threat actor attempting to use legitimate tools as part of their attack. It presents the SOC a clear view of legitimate usage of dual use tools in their organization, and combined with Symantec’s knowledge of the threat landscape, provides one-click hardening of end-points. More information on Adaptive Protection can be found here: Adaptive for SEPM customers.

Curiosity – Our Path to Risk Insights
An open framework and curious mindset provides great insights










We encourage you to share your thoughts on your favorite social platform.