Tech support scams increasing in complexity – Part 2
Tech support scammers continue to adopt new techniques, including using AES to obfuscate scam content.
In my last post, I discussed the evolution of tech support scams and their growing penchant towards the use of code obfuscation to hide their malicious activity behind heaps of obfuscated JavaScript code. This growing trend was an endeavor, undertaken with a single and simple objective in mind: to avoid detection by string-based detection engines employed by various security vendors. This allowed the attackers behind these fake scams to remain under the radar and still be as effective as ever.
Since then, a year has passed and a lot of water has flowed under the bridge. The threat landscape has witnessed a lot of significant changes, some of which include the introduction of JavaScript-based coin miners, malware (in particular ransomware) exploiting vulnerabilities in Microsoft’s implementation of the Server Message Block (SMB) protocol to spread, and the continuing decline in exploit kit activity. But where do tech support scams stand in today’s threat landscape?
As it turns out, tech support scams have got meaner, adding new anti-detection techniques to their arsenal. Over the past year, there has been a growing trend towards so-called “living off the land” tactics, which involves attackers using tools and technologies already installed on target computers. The main benefits behind using this approach are twofold: the attacker can target a larger pool of victims (as most of the users have these tools installed by default or use these technologies frequently), and at the same time keep a low profile (as these tools are not inherently malicious, using them is unlikely to trigger any alarms). In this blog post, I will describe how tech support scams have embraced this approach by making use of the Advanced Encryption Standard (AES) specification algorithm to obfuscate their scam content.
What is AES?
Advanced Encryption Standard or AES is an encryption algorithm used to encrypt sensitive electronic data so as to protect it from unintended third-party use while the data is stored or is in transit. AES is fast in both software and hardware and is the first (and only) publicly accessible algorithm approved by the National Security Agency (NSA).
Now tech support scams are following the trend and are using the AES encryption algorithm as an anti-detection mechanism.
While I’m not going to deep dive into the intricacies of this algorithm, the fact that it allows for strong data encryption, and is in widespread use around the world to secure sensitive data, makes it an ideal candidate for living off the land attacks. We have already witnessed this algorithm being used in various ransomware threats, such as TorrentLocker (Ransom.TorrentLocker) and TeslaCrypt (Trojan.Cryptolocker.N), and in other attacks such as in phishing kits. Now tech support scams are following the trend and are using the AES encryption algorithm as an anti-detection mechanism.
The scam
The scam is initiated when an unsuspecting user visits a malicious website or is redirected to one by various means such as a malvertisement or compromised website.
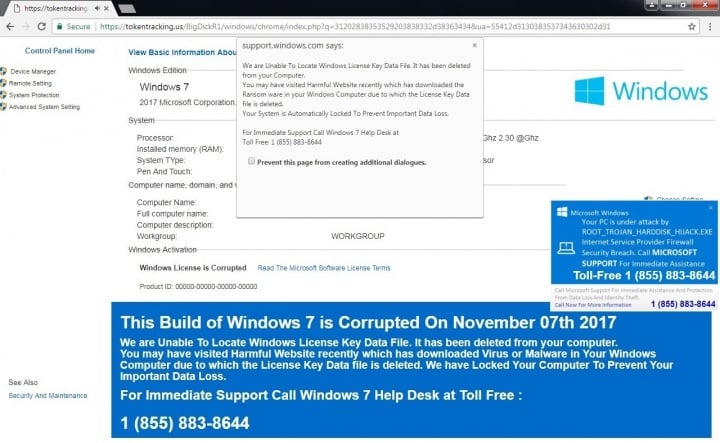
The scam web page informs the victim that the license key file has been deleted from the computer due to a malware infection and tries to lure the user into calling a “Toll free” number for assistance. An audio file, stating that the computer is infected, is also played in the background when the user arrives on the scam web page.
Joining the dots
A first look through the source code for the scam web page reveals the piece of code responsible for playing the audio.
After that we come across some interesting pieces of JavaScript code.
The first piece of code loads a file named aes.js, which is actually a library code implementation of the AES algorithm. As is the usual practice with software code development, this library is then used to decrypt AES obfuscated content on the fly, as we will see later.
The second piece of code contains two JavaScript functions. The first function takes AES encrypted hexadecimal content as input and uses a predefined hardcoded encryption key. The function proceeds as follows:
- The hexadecimal input is first converted into normal byte format.
- The AES library is then used to decrypt this byte content which is then presented to the victim. In particular, the AES algorithm in the “Counter” mode is used.
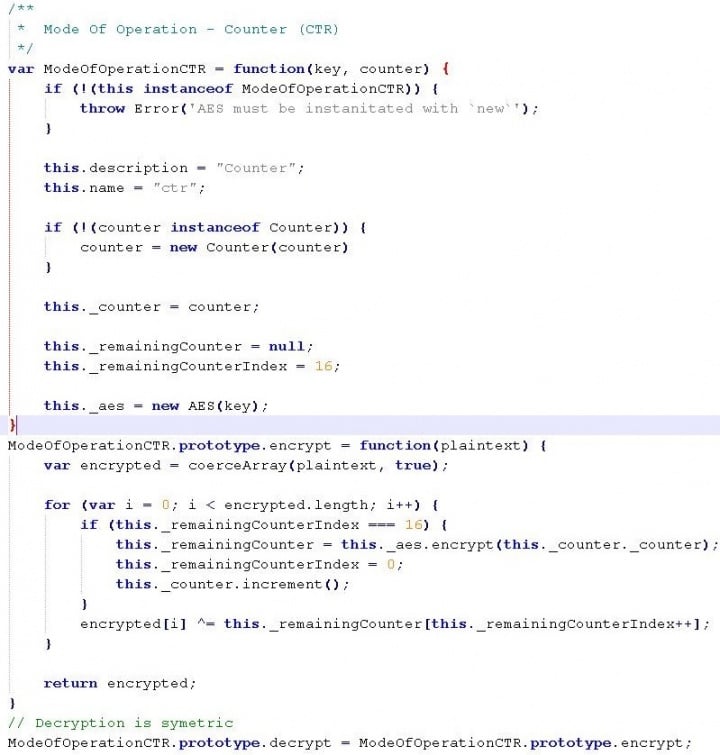
The code in Figure.2 is a sample from the AES library which is used for this decryption process.
The second JavaScript function works in a similar fashion except for a minor difference in the input format. The function takes a HTML DOM element as input, from which it then extracts the encrypted HTML content. The function then proceeds to decrypt this content, similar to the earlier function, and then replaces the encrypted HTML content in the DOM element with the decrypted content which is then presented to the user.
Moving forward, the scammers use the first function repeatedly by feeding it with pre-calculated encrypted hexadecimal content, to decode it on the fly into the scam messages, which are then presented to victims. A sample block of code can be seen in Figure.3.
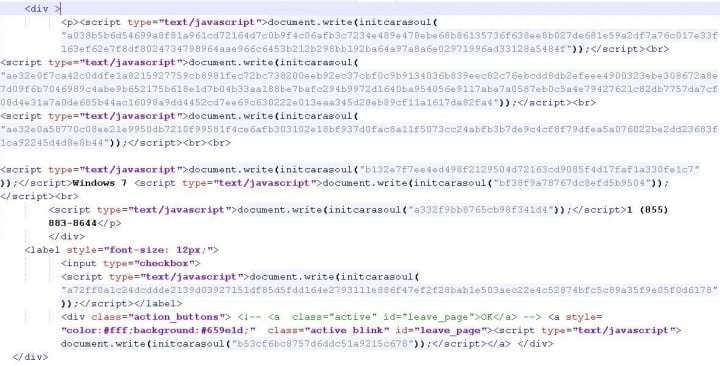
The code seen in Figure.3 decodes into the sample seen in Figure.4.
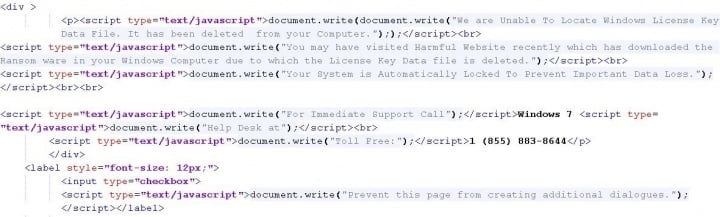
This is essentially what is visible to victims when they land on the scam web page. The scam page also has JavaScript code to look out for certain keyboard key presses. Any attempt to press ESC, F11, or the Ctrl+Alt+Delete combination is thwarted by the web page going full screen, making the scenario more alarming for the user.
Work In progress
While this tech support scam does, to a certain extent, manage to avoid detection, it fails in other aspects. For example, by using hardcoded values such as, for example, the operating system that the victim is supposedly using (hardcoded value is Windows 7), there is a risk that users will figure out it’s a scam. Considering these types of scams are usually tailored to each victim, it’s a likely assumption that this is still a work in progress and the scammers could well add more features in the future.
A continuing menace
Even though the threat landscape has evolved a great deal in the year since my last tech support scam blog, these scams have continued to persist and keep generating revenue for the criminals behind them. Tech support scams have also started integrating JavaScript-based cryptocurrency miners into their web pages, which serves a dual purpose in the sense that cryptocurrency can be mined using the victim’s CPU power and, as the computer’s performance becomes sluggish due to mining, it also makes the victim believe that their computer really is infected.
These new techniques employed by criminals demonstrate that this type of scam is continuing to evolve and that there is still plenty of money to be made, as such I think it is safe to assume that tech support scams are here to stay.
Protection
At Symantec, we provide a variety of products to protect our customers. Our Intrusion Prevention System (IPS) security component proactively protects customers from tech support scams by blocking the malicious network activity associated with such scams using a wide variety of detections. The scam is thus blocked even before it reaches the end user.
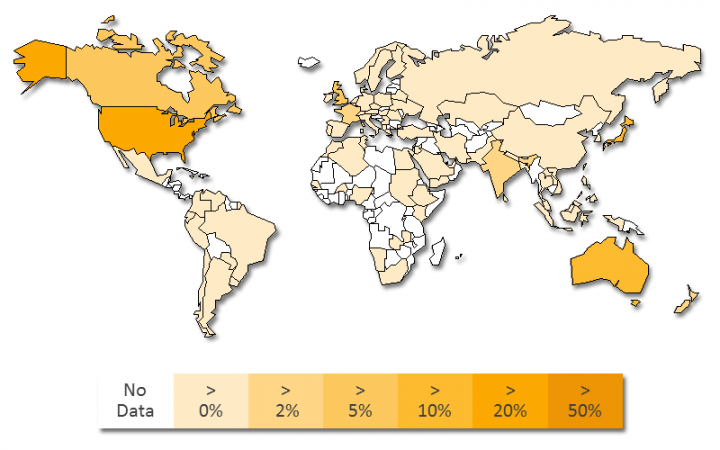
Our IPS telemetry for this year shows that the countries targeted the most by tech support scams were the U.S., UK, Canada, Australia, and Japan.
Mitigation
Norton Security, Symantec Endpoint Protection, and many other Symantec security products have comprehensive network-based protection features such as firewall and IPS built in. To protect yourself from these types of scams, ensure that none of these features are turned off.
Also make sure you visit legitimate websites when you need support for any product.
If you notice any piracy related to our products, please feel free to contact us here. Last but not the least, make sure your antivirus product is updated regularly. More information on tech support scams is available here.







We encourage you to share your thoughts on your favorite social platform.