Ransomware: Attacks Continue to Rise as Operators Adapt to Disruption
Available evidence suggests vulnerability exploitation has replaced botnets as a prime infection vector.
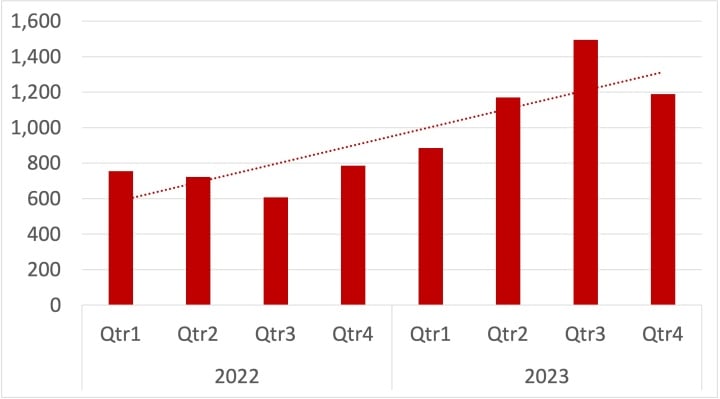
Ransomware activity remains on an upward trend despite the number of attacks claimed by ransomware actors decreasing by slightly more than 20% in the fourth quarter of 2023. Attackers have continually refined their tactics and proven quick to respond to disruption, finding new ways to infect victims.
Analysis of data from ransomware leak sites shows that attackers managed to hit significantly more victims last year (4,700) compared to 2022 (2,800). While the shutdown of the Qakbot botnet in June 2023 took a major malware distribution channel offline, attackers have quickly adapted and vulnerability exploitation now appears to be the primary vector for ransomware attacks.
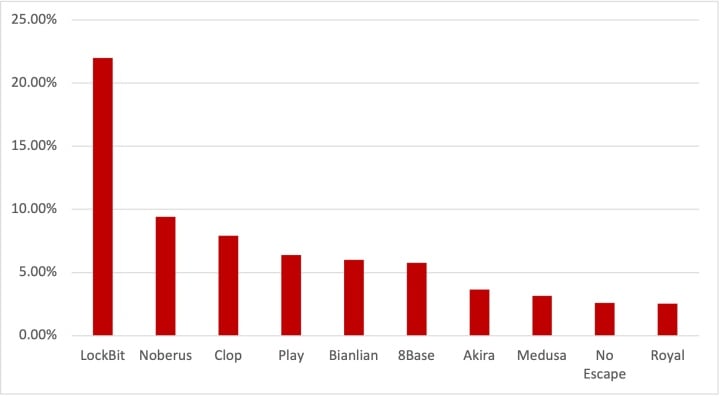
LockBit, the longstanding ransomware-as-service operation run by the Syrphid cybercrime group (aka Bitwise Spider), continued to be the largest ransomware threat in 2023, accounting for 21% of all attacks claimed on data leak sites. It was followed by Noberus (aka BlackCat, ALPHV) with 9% of all claimed attacks and Clop with 8%. Both LockBit and Noberus have been the target of law enforcement operations in recent weeks and it remains to be seen if these will significantly impact on activity levels from both threats over the long term.
Interestingly, there are significant disparities between overall, publicly claimed activity levels and ransomware activity investigated by Symantec. While LockBit was responsible for over 21% of the 4,700 attacks claimed in 2023, they were only identified as being involved in around 17% of the attacks Symantec investigated. Conversely, Noberus claimed 9% of all attacks in 2023 but it was involved in a little over 20% of all attacks Symantec investigated.
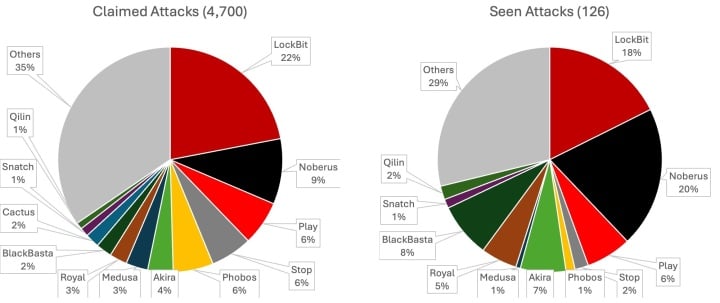
The comparison may give some indication of success rates experienced by actors linked to each operation. For Symantec to positively identify an attack as associated with a certain ransomware family, the attack has to advance to the stage where the attackers attempt to deploy a payload. This suggests that Noberus affiliates are more likely to advance their attacks at least to the payload deployment stage.
Vectors
The evidence from recent ransomware investigations suggests that exploitation of known vulnerabilities in public facing applications is now the main vector for ransomware attacks. Likely infection vectors in recent ransomware attacks include:
- CVE-2022-47966 ZOHO ManageEngine
- Microsoft Exchange Server vulnerabilities. Exploits were unknown but first evidence of malicious activity in a number of attacks occurred on Exchange Servers.
- Citrix Bleed (CVE-2023-4966) Citrix NetScaler ADC and NetScaler Gateway
- CVE-2023-20269 Cisco Adaptive Security Appliance (ASA) and Cisco Firepower Threat Defense (FTD) VPN
Tooling
The number of tools deployed by ransomware actors continues to grow. In particular, there has been a marked increase in the number of dual-use tools (legitimate software installed by attackers for malicious purposes). Tools leveraging the Bring Your Own Vulnerable Driver (BYOVD) technique are also currently popular among attackers. New tools recently seen in ransomware attacks include:
- HopToDesk: A publicly available remote desktop tool, which was used by attackers using a variant of the leaked Conti ransomware. Remote desktop tools are frequently used by ransomware actors, with the most popular being: Atera, AnyDesk, and Splashtop.
- TrueSightKiller: A publicly available tool that leverages the BYOVD technique to disable security software.
- GhostDriver: Another tool that leverages the BYOVD technique to disable antivirus (AV) tools.
- StealBit: A custom data exfiltration tool associated with the LockBit ransomware operation. StealBit appeared to have fallen out of favour among LockBit affiliates for some time. However, usage of the tool resumed in early 2024, where it was deployed in two separate LockBit attacks.
Techniques
Noteworthy techniques that have recently been used by ransomware actors include:
- Esentutl: Dumping credentials using the Windows command-line tool that provides database utilities for the Extensible Storage Engine (ESE). A known technique, in recent weeks attackers have been using it to dump browser credentials.
- DPAPI: Using malicious tools to extract and decrypt sensitive user credentials stored using Microsoft's Data Protection API (DPAPI).
Ongoing threat
Ransomware will continue to be a major threat for organizations in 2024 and beyond. Incentivised by large payouts, ransomware attackers have proven to be persistent and adaptive, capable of responding to disruption by reorganizing themselves and consistently developing new tactics.
Protection/Mitigation
For the latest protection updates, please visit the Symantec Protection Bulletin.
Indicators of Compromise
If an IOC is malicious and the file available to us, Symantec Endpoint products will detect and block that file.
7ebe51d5a48cc3c01878e06c6db3f4f0189c4f9788bfe57b763b03f4ab910e26 – StealBit
ce26642327aa55c67a564f695ae3038d5afee9b8d14bb5146bf30dd0f1af24e5 – StealBit
c06e320ad2568e15baae155346c6fb92e18fc038e7465adfb5fc2a3f8af9caa5 – HopToDesk
8d5c521d7a52fd0b24d15c61c344a8f87b3b623a1ab3520ab55197b772377155 – TrueSightKiller
09f7622eb9ed3bbd375575c8a190ff152ef3572a717a20c1b2dd5556b8cc9eba – TrueSightKiller
005cfd8a4dd101c127bcb0f94f1fa143b24d91442ee9e1525b4c540c9fe88c63 – TrueSightKiller
4c1346eab3fb23ca0613d73bbd2dd87fedb6ca8b1ba7bf48d69a57868d05854d – TrueSightKiller
13d525588d2f6babe0b6de7d1456a6f3f39a0947128280a94b6f676dd5684201 – TrueSightKiller
6ec7a25adc9bf516e9150bebd773feafa64787769156ffbcb6eccabc579ee03a – GhostDriver
19707b18f750bae0214e2a6d36735b6723549899bf83751d3650b9ec8125b91f – DPAPI credential dumper







We encourage you to share your thoughts on your favorite social platform.