Alpha Ransomware Emerges From NetWalker Ashes
Emergent ransomware operation has strong links with shuttered NetWalker.
Alpha, a new ransomware that first appeared in February 2023 and stepped up its operations in recent weeks, has strong similarities to the long-defunct NetWalker ransomware, which disappeared in January 2021 following an international law enforcement operation.
The NetWalker Connection
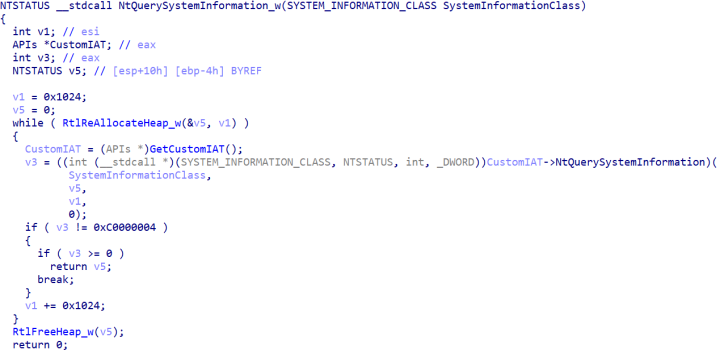
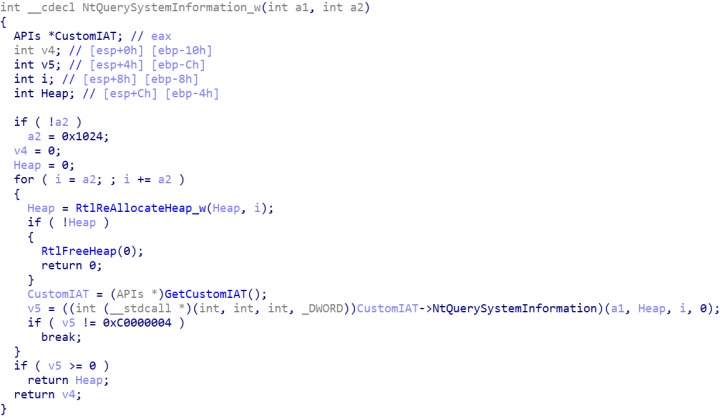
Analysis of Alpha reveals significant similarities with the old NetWalker ransomware. Both threats use a similar PowerShell-based loader to deliver the payload. In addition to this, there is a significant amount of code overlap between the Alpha and NetWalker payloads. This includes:
- The general execution flow of the main functionalities of both payloads.
- Two functionalities handled within a single thread: termination of processes and termination of services.
- A similar list of resolved APIs. While APIs are resolved using a hash, the hashes used are not the same.
- Both payloads have similar configurations, including their lists of skipped folders, files, and extensions; and their lists of processes and services to kill.
- Both payloads delete themselves using a temporary batch file after encryption is completed.
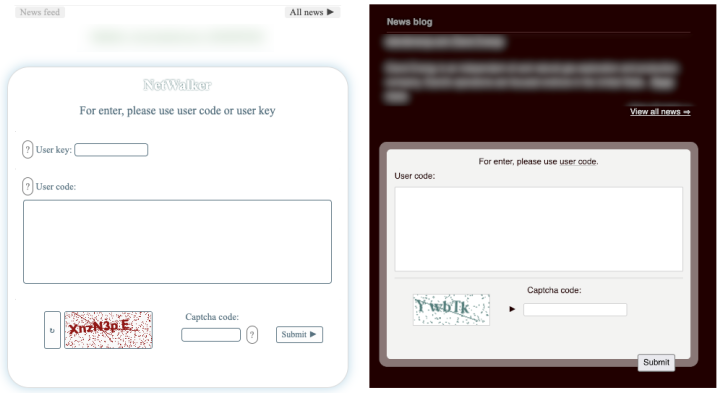
- Both have similar payment portals, containing the same message: “For enter, please use user code”.
| NetWalker | Alpha |
|---|---|
| nslsvice.exe | nslsvice.exe |
| pg* | pg* |
| nservice.exe | nservice.exe |
| cbvscserv* | cbvscserv* |
| ntrtscan.exe | ntrtscan.exe |
| cbservi* | cbservi* |
| hMailServer* | hMailServer* |
| IBM* | IBM* |
| bes10* | bes10* |
| black* | black* |
| apach* | apach* |
| bd2* | bd2* |
| db* | db* |
| ba* | ba* |
| be* | be* |
| QB* | QB* |
| oracle* | oracle* |
| wbengine* | wbengine* |
| vee* | vee* |
| postg* | postg* |
| sage* | sage* |
| sap* | sap* |
| b1* | b1* |
| fdlaunch* | fdlaunch* |
| msmdsrv* | msmdsrv* |
| report* | report* |
| msdtssr* | msdtssr* |
| coldfus* | coldfus* |
| cfdot* | cfdot* |
| swag* | swag* |
| swstrtr* | swstrtr* |
| jetty.exe | jetty.exe |
| wrsa.exe | wrsa.exe |
| team* | team* |
| agent* | agent* |
| store.exe | store.exe |
| sql* | sql* |
| sqbcoreservice.exe | sqbcoreservice.exe |
| thunderbird.exe | thunderbird.exe |
| ocssd.exe | ocssd.exe |
| encsvc.exe | encsvc.exe |
| excel.exe | excel.exe |
| synctime.exe | synctime.exe |
| mspub.exe | mspub.exe |
| ocautoupds.exe | ocautoupds.exe |
| thebat.exe | thebat.exe |
| dbeng50.exe | dbeng50.exe |
| *sql* | *sql* |
| mydesktopservice.exe | mydesktopservice.exe |
| onenote.exe | onenote.exe |
| outlook.exe | outlook.exe |
| powerpnt.exe | powerpnt.exe |
| msaccess.exe | msaccess.exe |
| tbirdconfig.exe | tbirdconfig.exe |
| wordpad.exe | wordpad.exe |
| ocomm.exe | ocomm.exe |
| dbsnmp.exe | dbsnmp.exe |
| thebat64.exe | thebat64.exe |
| winword.exe | winword.exe |
| oracle.exe | oracle.exe |
| xfssvccon.exe | xfssvccon.exe |
| firefoxconfig.exe | firefoxconfig.exe |
| visio.exe | visio.exe |
| mydesktopqos.exe | mydesktopqos.exe |
| infopath.exe | infopath.exe |
| agntsvc.exe | agntsvc.exe |
| notepad.exe | |
| genshinimpact.exe |
Alpha Attacks
While Alpha first appeared in February 2023, it maintained a low profile until recent weeks when it appeared to begin scaling up its operations and launching a data leak site.
In recent attacks involving Alpha, the attackers made heavy use of a number of living-off-the-land tools, including:
- Taskkill: Windows command-line tool that can be used to end one or more tasks or processes.
- PsExec: Microsoft Sysinternals tool for executing processes on other systems. The tool is primarily used by attackers to move laterally on victim networks.
- Net.exe: Microsoft tool that can be used to stop and start the IPv6 protocol.
- Reg.exe: Windows command-line tool that can be used to edit the registry of local or remote computers.
Rebrand or Return?
NetWalker was part of the first wave of cybercrime operations to profit from targeted ransomware attacks, where attackers attempt to encrypt entire networks in order to extort their victims. One jailed group member alone is alleged to have earned over $27.6 million from attacks.
Following the law enforcement operation and long cessation of activity, it had been assumed that NetWalker had completely departed. However, the similarities between Alpha and the NetWalker ransomware suggest a strong link between the two threats. Alpha may be an attempt at reviving the old ransomware operation by one or more of the original NetWalker developers. Alternatively, the attackers behind Alpha may have acquired and modified the original NetWalker payload in order to launch their own ransomware operation.
Protection/Mitigation
For the latest protection updates on Alpha, please visit the Symantec Protection Bulletin.
Indicators of Compromise
If an IOC is malicious and the file available to us, Symantec Endpoint products will detect and block that file.
46569bf23a2f00f6bac5de6101b8f771feb972d104633f84e13d9bc98b844520 - PowerShell loader
6462b8825e02cf55dc905dd42f0b4777dfd5aa4ff777e3e8fe71d57b7d9934e7 - PowerShell loader
6e204e39121109dafcb618b33191f8e977a433470a0c43af7f39724395f1343e - PowerShell loader
89bfcbf74607ad6d532495de081a1353fc3cf4cd4a00df7b1ba06c10c2de3972 - PowerShell loader
e43b1e06304f39dfcc5e59cf42f7a17f3818439f435ceba9445c56fe607d59ea - PowerShell loader
e573d2fec8731580ab620430f55081ceb7153d0344f2094e28785950fb17f499 - Alpha ransomware loader
e68dd7f20cd31309479ece3f1c8578c9f93c0a7154dcf21abce30e75b25da96b - Alpha ransomware loader
ab317c082c910cfe89214b31a0933eaab6c766158984f7aafb9943aef7ec6cbb - Alpha ransomware loader
df15266a9967320405b3771d0b7353dc5a4fb1cbf935010bc3c8c0e2fe17fb94 - Alpha ransomware loader
b7ca6d401b051712cb5b1a388a2135921a4420db8fe41842d51d2ec27380b479 - Alpha ransomware loader
5f3bf9c07eedde053f19ce134caa7587f8fb6c466e33256e1253f3a9450b7110 - Alpha ransomware loader
c00fbf3fb992e7f237c396d69081246570cbd60d6c7a2262c01ae4d8e6f17ddd - Alpha ransomware loader
b2adf8ec7ab5193c7358f6acb30b003493466daee33ea416e3f703e744f73b7d - Alpha ransomware loader
a8d350bbe8d9ccfbb0c3e9c2dd9251c957d18ce13ae405ceb2f2d087c115db15 - Alpha ransomware loader
2d07f0425dc465b3a1267a672c1293f9a3d0cd23106b7be490807fea490978ea - Alpha ransomware loader
f5d25777331ba55d80e064dea72240c1524ffcd3870555a8c34ff5377def3729 - Alpha ransomware loader
9d6ed8396ee79ae92a5e6cef718add321226def3461711cf585e0fd302c961ae - Alpha ransomware loader
1c12ff296e7d9f90391e45f8a1d82d8140edf98d616a7da28741094d60d4779d - Alpha ransomware loader
9c71500a9472814f7bf97a462fe9822cf93dc41e2e34cc068734586d5e5146ef - Alpha ransomware loader
480cf54686bd50157701d93cc729ecf70c14cd1acd2cb622b38fc25e23dfbc26 - Alpha ransomware loader
0bad18cb64b14a689965540126e0adbc952f090f1fb7b6447fe897a073860cdb - Alpha ransomware loader
c5f7492a3e763b4456afbb181248fdb8e652575cea286db7861e97ffcd1b72e4 - Alpha ransomware loader
f3858d29073ae90f90c9bb284913752533fe1a6437edd6536e4b1775fc8f6db4 - Alpha ransomware loader







We encourage you to share your thoughts on your favorite social platform.