APT – A Significant Risk that Won’t Go Away
A closer look at how Symantec Privileged Access Management technologies protect against APT
Advanced Persistent Threats (APTs) are not new. Ten years ago, there were numerous stories in the news about how APT attacks were used to successfully breach different companies, but these attacks have not stopped. State-backed and well-organized groups continue to leverage APT attacks to breach organizations worldwide today. Additionally, a recent article in Dark Reading reported that new research from BlackBerry found that at least five Chinese APT groups have been involved in a long running campaign to steal intellectual property and other sensitive data, and that “the access these groups have acquired in recent years could allow them to exploit the recent surge in teleworking, due to the COVID-19 pandemic.”
The Primary Attack Steps of an APT Attack
Unfortunately, the APT attack pattern is repeatable and sustainable, which is what makes it so compelling, and worse yet, we know what this pattern is – cyber security teams at Lockheed Martin first identified the attack vector, and they coined the term “kill chains” because disrupting the attack sequence at any point can “kill” the attack.
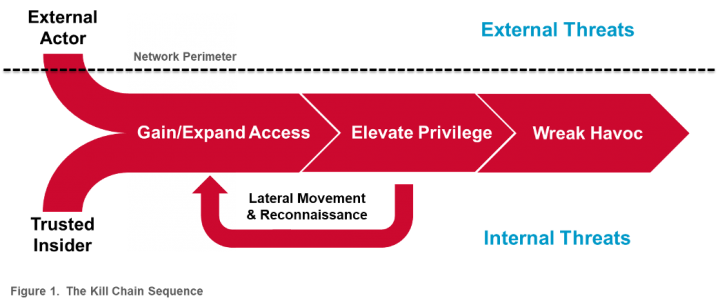
The attack steps are surprisingly simple:
- Gain Access and Expand. To access the network, APT Groups will exploit a vulnerability in the system to steal the credentials necessary to gain access to the network.
- Elevate Privileges. Once inside, APT Groups will try to elevate their privileges, so they can issue commands and gain access to whatever resources they’re after.
- Investigate and Move Laterally. APT Groups rarely land in the exact spot where the data they’re seeking is located, so they’ll investigate and move around in the network to get closer to their ultimate goal.
- Wreak Havoc. Once APT Groups have the access they need and have found exactly what they’re looking for, the attackers are free to wreak havoc (e.g., theft, business disruption, etc.).
So, where does Symantec’s Privileged Access Management (PAM) help to disrupt this attack sequence?
The Importance of PAM in Defending Against APT
Although there is no silver bullet to defending against APTs, there are several approaches and technologies, that when combined, help to reduce both the potential for a breach and mitigate the damage if one were to occur. Traditionally, the initial approach was to secure the perimeter using firewalls and intrusion detection systems. These systems are still critical and widely used by many organizations, but as the perimeter is shifting to the “edge”, organizations are moving to Zero Trust models. However, no matter how secure you make your perimeter, you must assume that hackers will find a way inside your outer defenses (they don’t call them “persistent” for nothing), and this is where PAM technologies step in to continue the fight.
PAM technologies implement the principal of Zero Trust and least privileged by only granting policy-based access to these accounts and credentials.
Once a hacker gains a toehold in the network, the next step is to expand and elevate their privileges until they can gain access to the data they are seeking. In fact, Forbes found that almost 74 percent of data breaches start with privileged credential abuse. PAM tools form the core defense against APT by controlling access to privileged credentials and accounts and monitoring their usage as a means of early detection of unusual or risky behavior. PAM technologies implement the principal of Zero Trust and least privileged by only granting policy-based access to these accounts and credentials. They also track all activities to both help ensure accountability and to assist in a security breach investigation. Additionally, the Dark Reading article also stated that although APT attacks are “cross-platform attacks” on backend servers, “Linux [is] a particular focus since enterprise Linux systems are often not as well protected as other infrastructure.” Here again, PAM technologies can step in to help harden your mission critical servers, especially your Linux environment.
Fine-Grained Access Controls for your Mission Critical Servers
Fine-grained access controls, aside from being good security practice, are particularly helpful in preventing and mitigating the damage caused by an APT. Once attackers gain administrative privileges, they usually install backdoor “rootkits” and begin to export sensitive data. With proper access controls, an attacker with even privileged access controls is limited in what he or she can do, and may be prevented from accessing sensitive files, executing malicious commands, installing programs, stopping or starting services, or changing log files. On a system where fine-grained controls are implemented, an attacker may be forced to compromise multiple accounts in order to do what was previously possible with a single account. Furthermore, implementing fine-grained access controls can also mitigate the risk of one of the greatest security weaknesses in an organization: its people. By limiting access to critical systems and data to your privileged employees, the damage that can be done by an attacker who gains access to their accounts through social engineering is diminished.
Introducing Symantec Privileged Access Management
Symantec PAM is designed to prevent security breaches by protecting sensitive administrative credentials, controlling privileged user access, proactively enforcing security policies and monitoring and recording privileged user activity across virtual, cloud, hybrid, and physical environments. Symantec PAM is a foundational component to not only establishing Zero Trust, but the solution also provides several critical capabilities that defend against APT, including a privileged credential vault, session recording, and threat analytics to manage and monitor user access to privileged accounts and credentials.
Symantec PAM also provides server hardening for Windows, Unix, and Linux via its server control agents. These agents are kernel-based and are installed on the target endpoints, and can control both inbound and outbound communications, restricting packets by source IP, protocol, and TCP port. They can block code execution exploits and installation of “backdoor” software and can enable file integrity monitoring to detect changes to key files, such as those made by “root kits”. Finally, the server control agents can be configured in such a way that no user is authorized to shut them down without having physical access to the system. This would prevent an external hacker from attempting to disable the agents.
Combined these capabilities address the challenges poised by APT attacks by disrupting their ability to further elevate their privileges and compromise your mission critical servers. In addition, our appliance-based solution installs quickly and is easy to use and maintain. It also offers unparalleled performance and 10x the scalability compared to our leading competitors; this yields the lowest total cost of ownership in the industry.

Digging Deeper Into Zero Trust
Enterprises can’t any longer rely on the once-popular castle-and-moat approach. The future is in Zero Trust Networks








We encourage you to share your thoughts on your favorite social platform.