5 Top EDR Use Cases
When preventative measures fail, these five actions can save you
Attackers are growing more stealthy, their methods evolving to the point where their attacks can evade even more advanced preventative cybersecurity defenses. This blog offers examples of use cases where endpoint detection and response (EDR) can help you identify and stop sophisticated attacks.
What is endpoint detection and response (EDR)?
Endpoint detection and response (EDR) is an integrated endpoint security solution that combines real-time continuous monitoring and collection of endpoint data with rules-based automated response and analysis capabilities.
EDR offers a second line of defense after traditional antivirus and even next-generation antivirus (NGAV) protections, which is increasingly needed as attackers use advanced techniques to evade those first-line defenses. EDR equips security teams to detect and respond to advanced attacks quickly, to pinpoint how attackers infiltrated the environment, and (when deployed with NGAV and some other solutions) can set up policies to prevent similar attacks in the future.
Endpoints are under attack in part because that’s where the people are–and people are vulnerable to social engineering, phishing and other attacks that take advantage of busy, distracted users. (Indeed, the human element plays a role in 74% of all breaches.) Vulnerabilities in endpoints themselves, including out-of-date software and operating systems, further leave organizations open to attacks.
EDR defends against all of these threats by acting as a safety net helping you catch threats that slip past your endpoint protection and equipping you to respond promptly and efficiently.
EDR examples: Advanced actions for security teams
EDR solutions allow security teams to engage in advanced detection and response activities that would be difficult, time-consuming, and haphazard without the help of EDR. EDR examples, and the advanced capabilities EDR enables, include incident response, remote remediation, alert triage/visualization, threat hunting, and forensic investigations.
Incident response
The ability to respond rapidly and with confidence to detected cybersecurity incidents can spell the difference between minimal disruption to the business and catastrophic damage. Proper incident response (IR) strategies and tactics are essential to limiting the blast radius of attacks. According to the Cost of a Data Breach Report 2023, the most effective IR strategy for identifying and responding to a breach faster is to form an IR team and test your IR plan before you have to implement it. According to the report, doing this reduces the time required to identify breaches by 54 days.
While effective IR plans and procedures are essential, so is having the right information to act on–and that means having the right components in your security stack. This is where EDR solutions come in. When comparing EDR solutions, look for one that continuously records and stores endpoint activity data. This will give your IR team an endpoint activity system of record to track evidence of identified threats and to detect patterns of behavior. Advanced EDR provides the visibility and context IR teams need to do their jobs effectively–actionable insights that legacy antivirus and even many endpoint protection solutions simply cannot provide. EDR vendors should offer EDR protection via a range of models, from on-premise to hybrid environments and managed services.
Remote remediation
We noted earlier how vital it is to move quickly and decisively once a threat is detected. This can be challenging in an age where security and SOC team members work from multiple sites, including home offices. Ask EDR vendors if their solution will allow your team to securely and rapidly perform full investigations and remediation and from any location in the world.
Advanced solutions will take advantage of cloud-native architectures to, for instance, give administrators a remote shell that delivers visibility directly into every endpoint throughout the enterprise–a key capability when teams need to respond as quickly as possible to infected hosts.
Alert triage/visualization
Ask any SOC team member and they’ll confirm: alert fatigue is real. One of the most important capabilities for fighting alert fatigue are visualizations that allow analysts to triage alerts. With the right tools, analysts can quickly and easily understand and digest what occurred during the attack sequence. This helps set up policies to prevent a similar attack from happening again.
It’s a good idea to explore what alert visualization capabilities each EDR vendor offers. Look for solutions that visually represent all events associated with the alert. You should be able to select an individual process or event to see reputation, TTPs (tactics, techniques, and procedures), command line used, and other information. The visualization should deliver actionable information about the events that occurred during an alert, including where prevention was applied, source, and what the attacker may have been attempting. You should settle for nothing less.
Threat hunting
Threat hunting isn’t new to the industry, but it’s definitely a new concept for many security teams, especially those new to EDR. Threat hunting is the pursuit of indicators of compromise (IOCs) within public and private cloud servers, endpoints, and networks. These IOCs can signal a compromise, intrusion, or data exfiltration.
Threat hunting differs from incident response because threat hunting is proactive, whereas incident response is reactive. The two roles work hand in hand, however. In fact, many security teams assign staff members to the task of threat hunting; often these are successful incident responders whose experience helps them accurately determine how an attacker will behave and what they may do next.
To streamline threat hunting and ensure its effectiveness, look for solutions that collect comprehensive data and extensive threat intel, giving you all the information you need to proactively hunt threats, uncover suspicious behavior, disrupt attacks in progress, repair damage quickly, manage vulnerability and address gaps in defenses. Superior solutions allow you to search through raw unfiltered endpoint data, even if the endpoint is offline. By establishing automated watchlists, you should be able to scale your hunt across large enterprises–and never hunt the same threat twice.
Forensic investigations
Pinpointing how an intrusion took place, including identifying TTPs and understanding the path attackers took, is vital to preventing similar attacks in the future. This is where extensive visibility comes in: the more data forensic investigators have access to, the more thorough their analysis.
Your EDR solution should be able to visualize the entire attack chain. This makes it easier to identify the root cause of an incident. Analysts should also be able to quickly jump through each stage of an attack to gain insight into the attacker’s behavior, close security gaps, and learn from every novel attack technique.
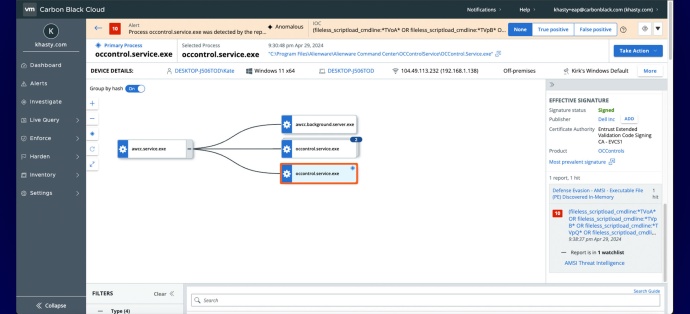
Carbon Black EDR: Advanced threats call for advanced defenses
Threats are evolving so rapidly that you’re likely considering an EDR deployment–if not now, then soon. The examples described above all form an argument for making a strategic choice in your EDR platform. For a growing number of organizations, that choice is an acclaimed EDR solution from Carbon Black, which pioneered EDR and is now part of Broadcom’s Enterprise Security Group portfolio of solutions.
Carbon Black EDR detects and responds to advanced attacks via a comprehensive and integrated approach for security teams. You’ll gain immediate access to the most complete picture of an attack, reducing lengthy investigations from days to minutes–a crucial advantage when every second counts. Security teams can proactively hunt for threats, uncover suspicious behavior, disrupt active attacks, and address gaps in defenses before attackers can.
Carbon Black EDR robustly supports every example use case discussed here–from incident response, remote remediation and alert visualization to threat hunting and forensic investigation. In fact, Carbon Black EDR delivers all the endpoint visibility, contextualized information (including attribution, details on the threat actor, and other attack information) to respond quickly to limit damage and stop lateral movement. Carbon Black EDR is built to track down attackers and give them nowhere to hide.
Find out for yourself how Carbon Black EDR can deliver your next line of defense. Contact us to arrange a demo today.

RSAC 2024: 3 Insights You May Have Overlooked
And how to apply them








We encourage you to share your thoughts on your favorite social platform.