Trickbot: U.S. Court Order Hits Botnet’s Infrastructure
Symantec assists in cross-industry initiative to disrupt virulent botnet tied to ransomware spread, banking credential theft, and other campaigns.
A global partnership of security, software, telecommunications and financial services firms have struck a blow against the notorious Trickbot botnet by securing a court order directing hosting providers to take down its infrastructure. The order was obtained in a U.S. lawsuit filed by Microsoft and the Financial Services Information Sharing and Analysis Center (FS-ISAC) against Trickbot’s anonymous operators and was based on technical evidence provided by the Symantec, a division of Broadcom (NASDAQ: AVGO) Threat Hunter Team and others. The legal action marked the culmination of a years-long, cross-industry collaboration to find innovative ways to thwart a pernicious botnet that has fueled numerous cyber-crime sprees.
In written testimony provided to the court, Symantec technical director Vikram Thakur said Trickbot has spread prolifically across the internet for years and become one of the most commonly blocked types of malware, suggesting it is now one of the world’s largest botnets.
Thakur described the serious harm caused to users whose computers are infected with Trickbot and whose banking credentials and other sensitive information are frequently stolen by the attackers. He also described its impact on financial institutions, which have borne significant losses due to Trickbot fraud.
In recent times, Trickbot has been implicated in targeted ransomware attacks, where credentials stolen by the malware were used by the Ryuk ransomware operators to compromise victims’ networks and encrypt all accessible computers. This assessment has been confirmed by Europol, which recently noted that “the relationship between Emotet [another botnet], Ryuk and Trickbot is considered one of the most notable in the cybercrime world”.
The botnet’s impact on banks and other financial sector organizations prompted a successful and close collaboration between the security industry and the financial sector, represented by FS-ISAC.
Unlike prior legal “takedown” actions against botnets, this case did not involve seizure of malicious infrastructure or redirection of network traffic but instead relied upon intellectual-property laws to effectively evict the botnet operators from the command-and-control servers they need to maintain access to victim machines.
What is Trickbot?
Trickbot is a major botnet consisting of computers that have been infected with the Trickbot Trojan (Trojan.Trickybot). The Trojan is modular in nature, meaning it can easily be customized with one or more of an array of custom components designed to carry out a range of malicious activities on infected computers. To date, it has mainly been used for two main purposes: stealing credentials from infected computers and acting as a distribution channel for other malware. Symantec believes that Trickbot’s operators earn most of their revenue from selling stolen credentials on the cyber underground and leasing out the botnet as a distribution channel for other malware authors.
Trickbot is spread through spam and phishing email campaigns which usually bear a Microsoft Word attachment containing malicious macros. If the document is opened by the unsuspecting user, Trickbot will be installed on the victim’s computer. In some cases, other malware, particularly ransomware, is also installed on the victim’s computer.
Trickbot will also attempt to leverage known software vulnerabilities to move across the victim’s network and install itself on other computers.
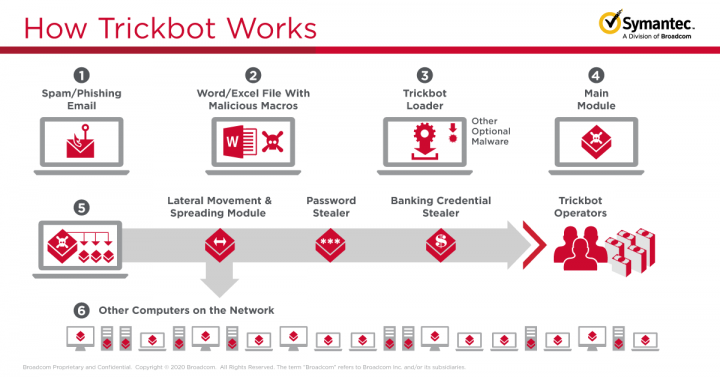
How Trickbot works
Trickbot is modular malware, capable of performing a range of different malicious activities. The first module to be installed on the victim’s computer is the loader, which contains an encrypted list of IP addresses from which it can download its main module.
Once downloaded, the main module will check the architecture of the victim computer and save this along with the bot’s own information. The main component then prepares a framework for additional modules and initiates a connection to one of a pre-configured list of command and control (C&C) servers.
The main module downloads one or more additional modules. Known modules include:
- Banking credential stealer (injectDll): For injecting malicious content into browser windows displaying banking websites in order to steal credentials
- Reconnaissance module (networkDll): For gathering system information and network/domain topology to determine whether the device can be infected with ransomware
- Data stealer (importDll): For stealing data from a web browser
- Password grabber (Pwgrab: For stealing passwords from various locations
- Cookie stealer (cookiesDll): For stealing cookies from the infected computer
- Information stealer (mailsearcher): For searching all files in all drives in the system looking for specific information
- Point-of-Sale recon (psfin): Reconnaissance module to determine if there are any Point-of-Sale (POS) devices connected
- Remote control module (vncDll): Virtual Network Computing (VNC) module
- SMB spreader (tabDll): For spreading over Server Message Block (SMB) using the EternalRomance exploit and other vulnerabilities patched by Microsoft in March 2017 (MS17-010)
- Outlook stealer (outlookDll): For stealing data saved by Microsoft Outlook
- Lateral movement module (shareDll): For lateral movement/enumeration via Lightweight Directory Access Protocol (LDAP) and SMB exploitation
- Lateral movement module (wormDll): For lateral movement/enumeration via LDAP and SMB exploitation. The shareDll and wormDll modules work in cooperation.
- RDP brute-force module (rdpScanDll): A new module that uses brute-forces the Remote Desktop Protocol (RDP) for a specific list of victims
Stealthy threat
Trickbot includes a number of features designed to minimize the risk of detection by security software. For example, the main module is designed to evade execution within “sandboxes,” which are controlled environments used by security companies to analyze malware.
This module will also check the current user’s privileges and, if they have low privileges, it will elevate them using User Access Control (UAC) bypass, a technique that allows execution of programs with elevated privileges without the user being prompted.
When it obtains elevated privileges, Trickbot will attempt to identify any security software that is installed on the computer and attempt to stop it and end any related services.
Credential theft
One of the main threats for Trickbot victims is credential theft. This is carried out by a module that monitors for browser visits to a pre-configured list of banking websites. If the user visits any of these websites, the module intercepts and alters network traffic between the computer and the website, allowing the attackers to steal the victim’s banking credentials after they are input by the user.
Trickbot will also attempt to steal other credentials from Chrome and Internet Explorer’s password storage features, from various RDP and SSH related services, and from other password managers.
Immediate threat
While infected computers are added to the Trickbot botnet, they yield the most value to attackers immediately after infection. Other malware families are usually delivered at the point of initial infection. Credential theft happens immediately after infection, while banking credentials are stolen the first time the victim attempts to log into their bank. Even if the malware is subsequently detected and the computer is removed from the botnet, much of the damage will have been done at this point, with stolen credentials exfiltrated by the attackers and likely sold to other cyber criminals.
Ongoing battle
By pooling resources and intelligence and utilizing available legal avenues, the information security and financial sectors hope to strike a major blow against Trickbot. Symantec is grateful for the leadership of Microsoft and FS-ISAC and the support of ESET, NTT, and Lumen Technologies. This latest action, however, is just one step in an ongoing campaign. Complete eradication of this botnet will likely require additional actions from government partners in multiple jurisdictions. However, this action proves that successful private industry collaboration can be effective in countering cyber-crime and we hope that this set a new precedent for further initiatives.
Protection
The following protections are in place to protect customers against Trickbot activity:
- Trojan.Trickybot
- SONAR.Trickybot
- Trojan.Trickybot!g7
- Trojan.Trickybot!g8
- Trojan.Trickybot!g11
- Trojan.Trickybot!g13
- Trojan.Trickybot!g16
- Trojan.Trickybot!gen2
- Trojan.Trickybot!gen5
- Trojan.Trickybot!gm
Mitigation
Symantec recommends users observe the following best practices to protect against Trickbot attacks:
- Enable 2FA to prevent compromise of credentials.
- Harden security architecture around email systems to minimize the amount of spam that reaches end-user inboxes and ensure you are following best practices for your email system, including the use of SPF and other defensive measures against phishing attacks.
- Restrict access to RDP Services: Only allow RDP from specific known IP addresses and ensure you are using multi-factor authentication.
- Implement proper audit and control of administrative account usage: You could also implement one-time credentials for administrative work to help prevent theft and usage of admin credentials.
- Create profiles of usage for admin tools: Many of these tools are used by ransomware attackers to move laterally undetected through a network. A user account that has a history of running as admin using PsInfo/PsExec on a small number of systems is probably fine, but a service account running PsInfo/PsExec on all systems is suspicious.
| Indicators of Compromise |
|---|
| 486a3a7e45aa168de7761da674396231 |
| cf63b9cc0187cd8344b71464c0172ab8 |
| 1db0a0786a1394aeda9e9d0adf8b846f |
| 1b557b166ddf21da002086de783f4aa5 |
| aef03ddd3134451e1efe137fb22e3a0c |
| be593f6c6a77f61d20bb31196aabf86a |
| 7353c6afe9fa2f2c1dca1d9910abfe6a |
| 54aee5682a03b2432820755e4fdbdacf |
| ac7a01eb09e803b7933c04e2c90960e4 |
| 9a7f353a1809f290b52aec98172f4a4f |
| 6a3e154c10c0d9afff59bee320844748 |
| 03b4eb88ab2829fa148814c10a7236fa |
| 00b7be1d568106e570d36ce5d4592904 |
| d8ef2838bb27c42eddd31c6e65b00963 |
| 71b9c5da0a6be4c53565d56734885c13 |
| 4b71dba2a5b69a949bc63e3493f45ad1 |
| 30baf5b280eaf26fddd9b0c7a26862ca |
| ada6d7921efa942620e3a2df2e842437 |
| 6c0a8a2b30b2e35564f83da09a143cf2 |
| 8acd8ad8a953a4a4bda5c9adc6f43dbd |
| 84b42db47d25a2fa0d649d6a83b93ba1 |







We encourage you to share your thoughts on your favorite social platform.