Ransomware: Activity Levels Remain High Despite Disruption
Activity levels dipped slightly in the first quarter of 2024 as two major ransomware operations were the targets of law enforcement operations.
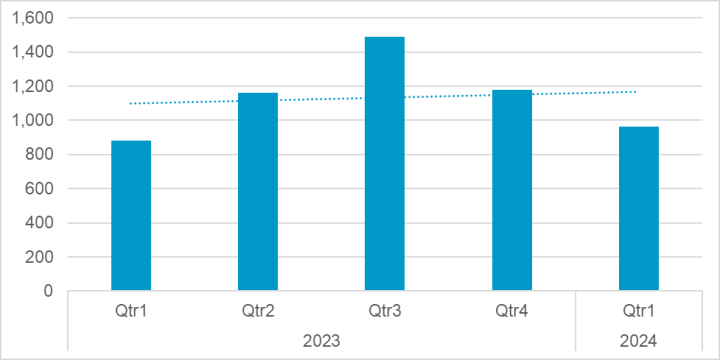
Ransomware activity fell slightly during the first quarter of 2024, most likely as a result of disruption to two major ransomware groups. However, overall activity levels remain on an upward trend and the number of attacks claimed in the first quarter of 2024 was ahead of attacks claimed in the corresponding quarter of 2023.
Analysis of data from ransomware leak sites found that ransomware actors claimed 962 attacks in the first quarter of 2024. The figure was down from the 1,190 attacks claimed in the fourth quarter of 2023, but still above the 886 attacks claimed in the first quarter of 2023.
The drop in overall activity levels is likely linked to disruption experienced by LockBit and Noberus, which were the two most prolific ransomware operations in 2023. Noberus (aka ALPHV, BlackCat) was the target of a U.S.-led law enforcement operation in December 2023. Although Noberus attempted to reestablish itself in the following weeks, it eventually closed in March 2024, citing the impact of the law enforcement operation, amid reports of a falling out with many of its affiliates. LockBit meanwhile was the target of a second international law enforcement operation in February 2024, but it has continued to operate.
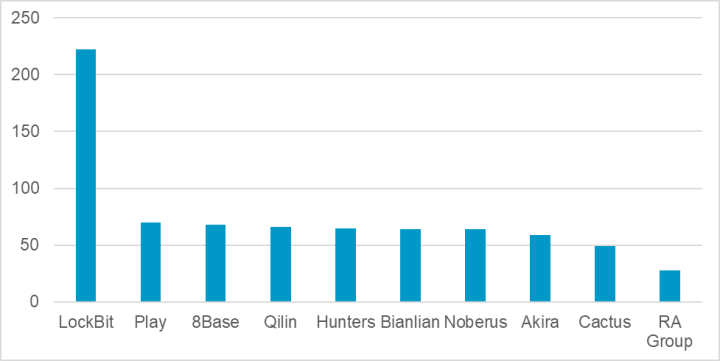
LockBit’s position as the number one ransomware threat remained unchallenged in the first quarter of 2024, accounting for over 20% of all claimed attacks. It was followed by Play, which was recently reported as having started a ransomware-as-a-service (7%), the prolific Phobos affiliate 8Base (6%), and the emergent Qilin ransomware (6%).
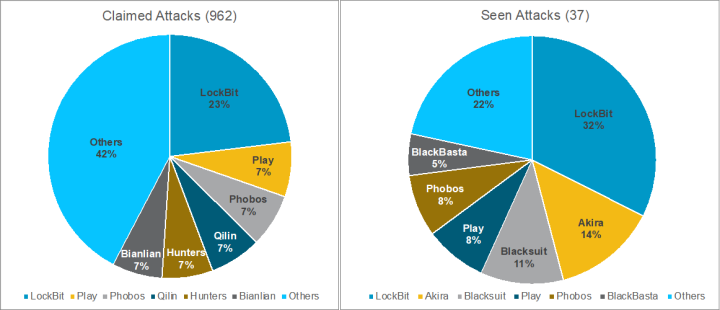
Once again, there were some big disparities between overall, publicly claimed activity levels and ransomware activity investigated by Symantec. While LockBit in both cases counted for the largest proportion of attacks, Akira was the second most prevalent ransomware family in attacks investigated by Symantec in Q1 (14%), yet it only accounted for 5.5% of all claimed attacks. Similarly, Blacksuit was involved in 11% of attacks investigated by Symantec, but only claimed 1.6% of all publicly reported attacks. The comparison may give some indication of success rates experienced by actors linked to each operation. For Symantec to positively identify an attack as associated with a certain ransomware family, the attack has to advance to the stage where the attackers attempt to deploy a payload. This suggests that attackers using Akira and Blacksuit are more likely to advance their attacks at least to the payload deployment stage.
Attack vectors
Available evidence suggests that exploitation of known vulnerabilities in public-facing applications continues to be the main vector for ransomware attacks. Attackers are continuing to target recently patched vulnerabilities in a bid to find unpatched systems. For example, in recent weeks, Symantec uncovered an ongoing campaign where attackers targeted web servers by exploiting a recently disclosed PHP vulnerability. The vulnerability (CVE-2024-4577) is a CGI argument injection flaw affecting all versions of PHP installed on the Windows operating system. The issue also affects all versions of the XAMPP development environment installed on Windows. Successful exploitation of the vulnerability can lead to remote code execution.
Once the attackers gain access to a vulnerable server, they download several tools, including a malicious HTA file that contains a copy of the open-source privilege-escalation tool BadPotato; a custom web shell; and a loader previously observed being used to deploy TellYouThePass ransomware.
Changing tactics
One notable development in Q1 was the return of the Clop (aka Cl0p) ransomware. Clop is operated by the Snakefly cybercrime group and fell into disuse during 2023 as the group began to forego encryption and focus purely on data theft for extortion. The threat actors achieve this chiefly by exploiting zero-day vulnerabilities in software that allow them to hit multiple victims at once, stealing their data before the activity is discovered, and threatening to publish it if a ransom isn’t paid. The most high-profile attack Snakefly was involved in in 2023 was the exploitation of vulnerabilities in Progress Software’s MOVEit Transfer managed file-transfer application. However, in recent weeks Symantec’s Threat Hunter Team has seen the Clop payload being used once again, suggesting that Snakefly is returning to mounting conventional double extortion attacks.
Bring-Your-Own-Vulnerable-Driver (BYOVD) continues to be a favored tactic among ransomware groups, particularly as a means of disabling security solutions. Since drivers are signed and can obtain kernel access, they are frequently used to kill processes. A correctly written driver will contain checks to ensure that only the software it’s designed to work with is issuing commands and that it’s only used for its intended purpose. A vulnerable driver, in the wrong hands, becomes a de facto privilege escalation tool.
The most recently seen tool in this category is Warp AV Killer, which has been used by at least one LockBit affiliate in recent weeks and leverages a vulnerable Avira anti-rootkit driver to disable security products.
Continuing danger
Although ransomware operations have experienced a high level of disruption to date in 2024, the impact on activity levels has been relatively limited. Ransomware is likely to continue as one of the main threats faced by enterprises for the foreseeable future.
Protection/Mitigation
For the latest protection updates, please visit the Symantec Protection Bulletin.
Indicators of Compromise
If an IOC is malicious and the file is available to us, Symantec Endpoint products will detect and block that file.
4de4621da1b7da597c2c8def4c08b8d405672dadb9c70d7dffd647c8d6abd394 – Web shell
95279881525d4ed4ce25777bb967ab87659e7f72235b76f9530456b48a00bac3 – Loader
5e446efb6c4f296fb8f25ef7a1a0a482f51dc475bd5ef3e89be9d43782a9f60f – TellYouThePass
7d6877eb8a3e2da1e8b06e2ed41604c6c3d5ced8293f7cc7e760ba972303bd0e – TellYouThePass
f572898ab9f9a0fabac77d5d388680f84f85f9eb2c01b4e5de426430c6b5008f – TellYouThePass
7101db8cb05e989c018ebc5df47819029cd76c4093b22c4582288795e46f6689 – TellYouThePass
2881194b7e0939d47165c894c891737d8c189ee8fb4720e814a4bcdd804d00d1 – TellYouThePass
ea59d6a130a279dfde4df53640bd720419c7b5d9711a21a78af9453b1b3b5805 – TellYouThePass
170d654b61810992fef6f18dbce5b4c7f5762cf36c9b41c36a14c9f6609f6e7d – TellYouThePass
aa0ef20f9f8ca111b0d8a550daf6651f5b0557f0acb0a26545755c5a02263a9b – TellYouThePass
3e65437f910f1f4e93809b81c19942ef74aa250ae228caca0b278fc523ad47c5 – TellYouThePass
2fc2d747847eb04561a435e65954f0103101e2190458eb3c125deda49326c597 – TellYouThePass
21ff399e57cc306a1ae1daab6009ea40c8aa96c39296d0f8781626de6bd19256 – TellYouThePass
d18453e564ca27514227478f225d85811fe15d08aa5fb1f613022c43155c5c54 – TellYouThePass
9562ad2c173b107a2baa7a4986825b52e881a935deb4356bf8b80b1ec6d41c53 – TellYouThePass
3f41e2ceff3a04cd6de6aadce7e7b7c8584940e4320a7db55dd712debb061510 – Clop
4d571f4d0008deb01e3144e0e3d5f882c5422acfcb4dd260082852a822d8d2fb – Clop
6192488729850a7a28498f233346e856b0097e4b3160baa641f8cf9571b56da8 – Clop
a702a671b7911a09ccb5b4f42923e8b301e0bbb851443dd52622022959a3055a – Clop
bef2d817f1813eb0629222112fd3721865a2a4eb1f4d51ad1f09fd807d4380ab – Clop
f6afa84b0847414220bb15517b8b5e2c505b64b53efbba73b753379c66ac5017 – Clop
6fb438feeb8369c5b82bfaa77144a641f7645c321f0b24dd97cfe2687b1ebd44 – Suspected Clop
88efa81984852dac62d325f2091a09de1e6423a711d7913aeac103c50664cf84 – Suspected Clop
38f0750cbe49b30db326b53b9f752b66c4f5e23cc3bbbd6d1844e2878a19b9a7 – Suspected Clop
aa43f34c3fa67aea994c1babeb71b46c7b24eccaa0455ae21aa561e251e7cc4d – Suspected Clop
1453179d46ef89eb780f8b82632f352017a3586e8d49fc3f087f633f7bebbf0a – Warp AV Killer
67e4c18e80d4d1acb9395f4a1fe9c2a75d95fcccdb33bcdd5259ba6f47e60e57 – Warp AV Killer







We encourage you to share your thoughts on your favorite social platform.