Tech Support Scams Now Get Users to Install Potentially Unwanted Apps
Tech support scammers' new trick is to get users to install potentially unwanted apps instead of calling a support hotline.
Tech support scams continue to prey on unwitting victims. We have seen in recent months how these scams are constantly evolving, from the use of call optimization to the use of Advanced Encryption Standard (AES) and a multi-level obfuscation scheme.
Tech support scammers' modus operandi is to get the victim to believe that their computer has been infected with malware, and that their only recourse is to call a technical support number for assistance on cleaning the system. Once on the call, a purported support executive would ask the victim for remote access to their computer and then charge a fee for the supposed cleaning they did.
While scammers' playbooks remain more or less the same, we have recently seen how scammers are now tricking victims into installing a potentially unwanted application (PUA), rather than urging them to call a support helpline.
Quick scan, quick scam
Toward the end of 2018, we observed a tech support scam campaign that displays a fake Windows alert, warning the victim that their computer might be infected. The scam prompts the victim to approve a supposedly quick 10-second scan of their computer.
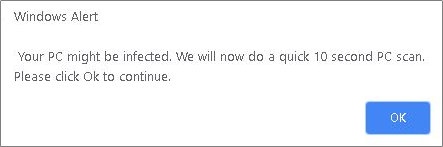
Once the user clicks OK, the scammers pull off a highly convincing but fake system scan that is almost identical to Norton Security's. We will provide details on how exactly the scammers pull this off later in this blog.

At the end of the fake scan, the victim is informed that their PC is indeed infected and then asked to download and install an update to their antivirus software. Upon clicking Proceed, a potentially unwanted application (PUA) is downloaded and installed onto the victim's computer.
Just like most tech support scams, this one typically begins after the user visits a malicious website, or is redirected to one through malvertising or a compromised website.
How the fake scan works
We went through the scam's source code to see how this fake scan trickery was achieved.
The code contains HTML div elements with the display property set to "none", as shown in Figure 3.
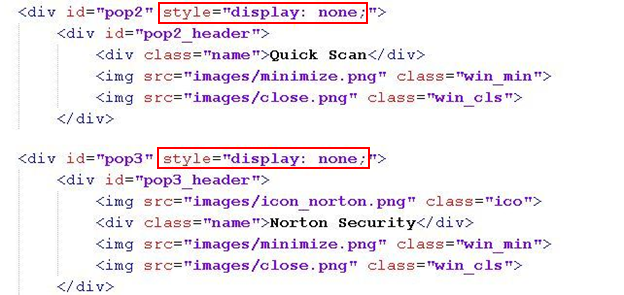
This setting of display property ensures that the div element is not visible to the victim as soon as the page loads.
Moving forward, we see JavaScript code, as shown in Figure 4.
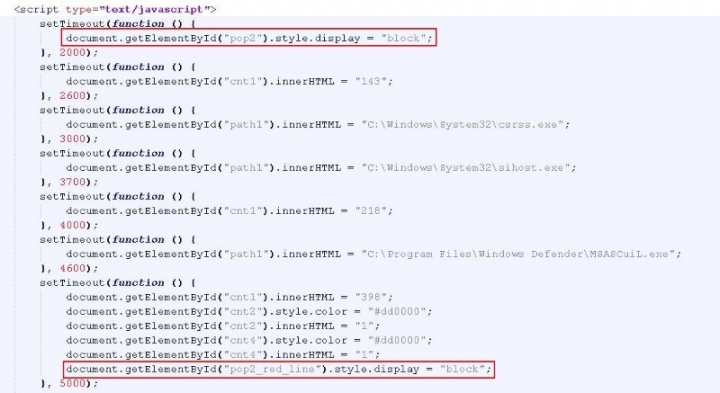
The setTimeout() method calls a function or evaluates an expression after a specified number of milliseconds. When the script shown in Figure 4 starts executing, it will first change the display style of the div to "block" after two seconds, thereby making the div visible to the victim. The scammer progressively increases the time period for the subsequent calls to the setTimeout() function. This makes the "windows" appear on top of each other, one after the other, on the front end. Thus, the victim first sees the start of the scan process, followed by the intermediate in-progress scan graphics, and finally the graphic box, which displays that the system is infected.
In Figure 4, we can see some values being assigned to different HTML elements via JavaScript. For example, the element "cnt1" is being assigned a value of 218, "path1" is assigned a value of "C:\Windows\System32\sihost.exe", and so on. These are the values for the number of files scanned and the current file being scanned as it appears on the front end. The scammer cleverly makes use of the setTimeout() function to change these values over a period of time, giving the victim the illusion that an actual scan is in progress and that their files are being scanned.
The scammer cleverly makes use of the setTimeout() function to change values over a period of time, giving the victim the illusion that an actual scan is in progress and that their files are being scanned.
PUAs vs helplines
In this scam, the scammer does not force the victim to call a support helpline, but rather tricks the victim into downloading a PUA. Typically, a PUA comes bundled with other intended software and gets installed along with the intended software.
PUAs have been known to perform the following actions on the computer:
- Display annoying pop-up windows
- Degrade the user's internet browsing experience by changing search engines and default home pages
- Perform random redirections
- Steal user information stealthily
- More recently, mine cryptocurrency in the background, degrading the health of the victim's hardware
In a typical tech support scam revenue-generation model, the scammer is dependent on the victim calling the support helpline to earn revenue. However, in this case, we have observed that the malicious code keeps track of the number of victims who are tricked into installing the PUA.

In this scenario, the scammer earns revenue by maximizing the number of PUA installs. Digging into our telemetry, we located an unsecured attacker dashboard, which shows the revenue distribution for this model.
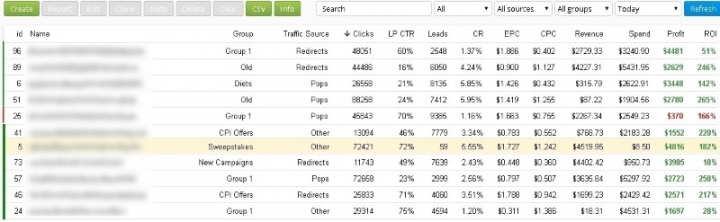
In Figure 6, we can clearly see the number of clicks generated by each traffic source and the corresponding returns on investment (ROI) from these sources.
This model is similar to that used in the exploit kit (EK) space, where malware authors use EKs as a mechanism to deliver their malware to more and more victims and thereby maximize their profit.
Not exclusive to Norton
In the past few weeks, we have also seen similar tech support scams that follow the PUA revenue-generation model. One such scam tricks the victim into believing that their Windows drivers are not updated and asks them to download and install the "latest drivers", which are actually PUAs.
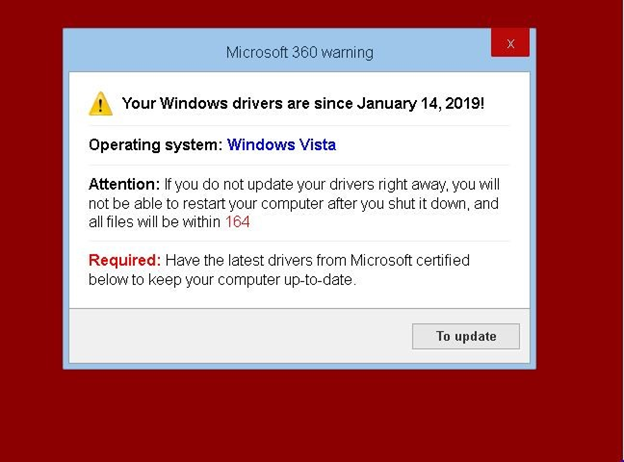
If this new model proves more profitable than the helpline route down the road, we are likely to see its adoption increase among scammers.
How to stay safe
Know what's real from fake. Even though the "Norton" scan looks almost indistinguishable from the real one, there are many attributes that easily indicate it is fake:
- The files on a computer system cannot be scanned by a website running inside a web browser. Thus, any website pretending to scan your system is performing a fake scan.
- Updates to the Norton security product are attempted through the product GUI and do not require manual user interaction, such as the download of any additional components via the browser.
- The scam has hardcoded attributes, such as "30 days of subscription remaining", which vary from user to user.
Prevalence and protection
Symantec proactively protects customers against tech support scams. Our intrusion prevention system (IPS) technology protects customers by blocking malicious network activity associated with such scams using a wide variety of detections.
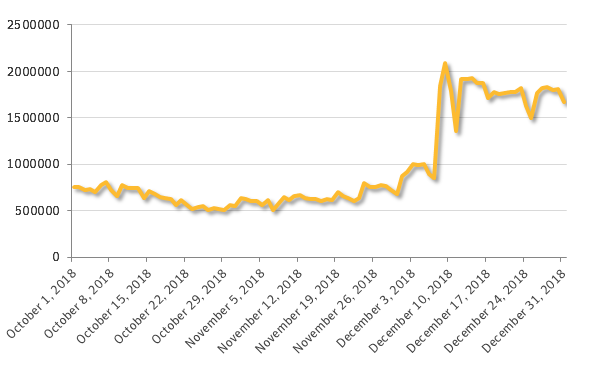
In the last quarter of 2018, Symantec's IPS blocked more than 89 million tech support scams.
Mitigation
Norton Security, Symantec Endpoint Protection, and many other Symantec security products have comprehensive network-based protection features such as firewall and IPS built in. To protect yourself from these types of scams, ensure that these features are enabled.
Also, make sure to visit only legitimate websites when you need support for any product. Last but not least, make sure your security product is updated regularly.
More information on tech support scams can be found here.







We encourage you to share your thoughts on your favorite social platform.