Beware of Open Source Projects on Google Play
While open source projects can be beneficial, criminals can also take advantage of them to create shady versions of familiar apps.
The Google Play Store has lots of legitimate applications which are open source projects, some of which are very popular. Taking advantage of these open source projects is an easy way for unscrupulous Android developers to create malicious applications and gain a lot of attention fast.
Open source describes software that is freely available to everyone to use, modify, and improve. In terms of security, it's a double edged sword. On the one hand, the transparency of open source means that flaws can be quickly found by other developers and fixed. But on the other hand, the transparency of open source means that flaws can be quickly found by the bad guys and exploited.
Another risk that can arise from open source projects is imitation. Criminals can use the open source code for an application and create an almost identical one but with some potentially malicious differences.
Teligram app
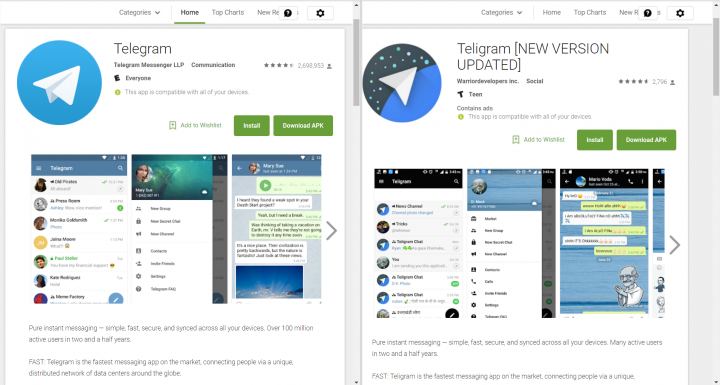
Symantec recently found an application named “Teligram [NEW VERSION UPDATED]” on the Google Play Store which is based on the official open source instant messaging app Telegram. The only differences, at least at first glance, are the (mis)spelling of Telegram, with an “I” replacing the second “e”, the bracketed addendum “[NEW VERSION UPDATED]”, and a slightly different app icon. These differences are an attempt to trick users into thinking the app is the latest updated version of the legitimate Telegram app.
The screen style and app description used by the Teligram app on Google Play are identical to the legitimate app and it even functions as an instant messaging app. However, in the background, Teligram has added advertisement libraries to the open source code in order to make money.
The apps’ pages on Google Play are very similar with the only differences being a slightly modified icon and name (Figure.1).
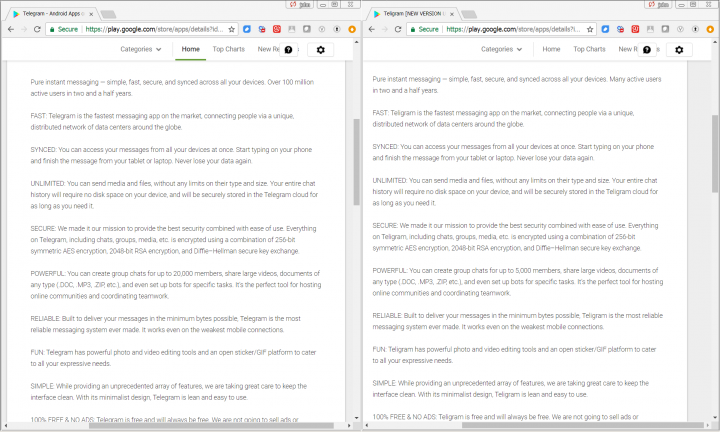
The apps’ description pages on Google Play are identical apart from the Telegram name being changed to Teligram (Figure.2).
Once installed, it becomes more difficult to tell the difference (see Figures 3 and 4).
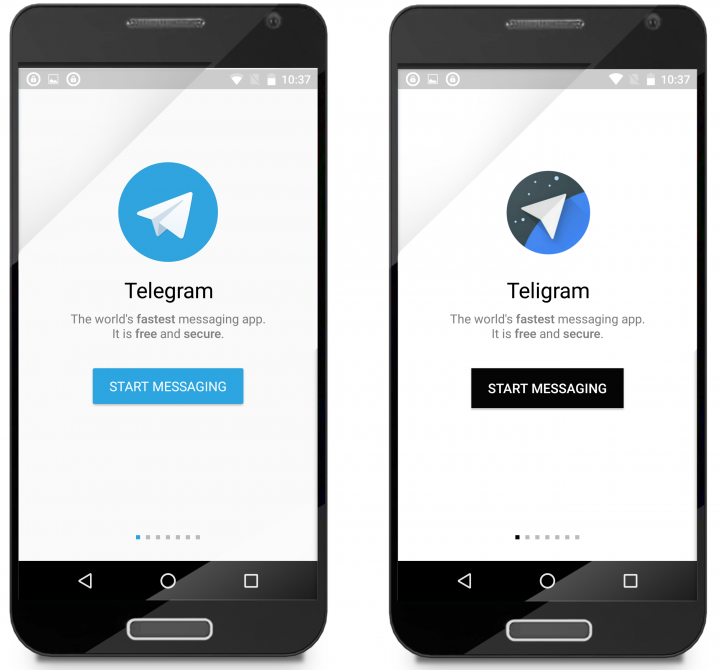
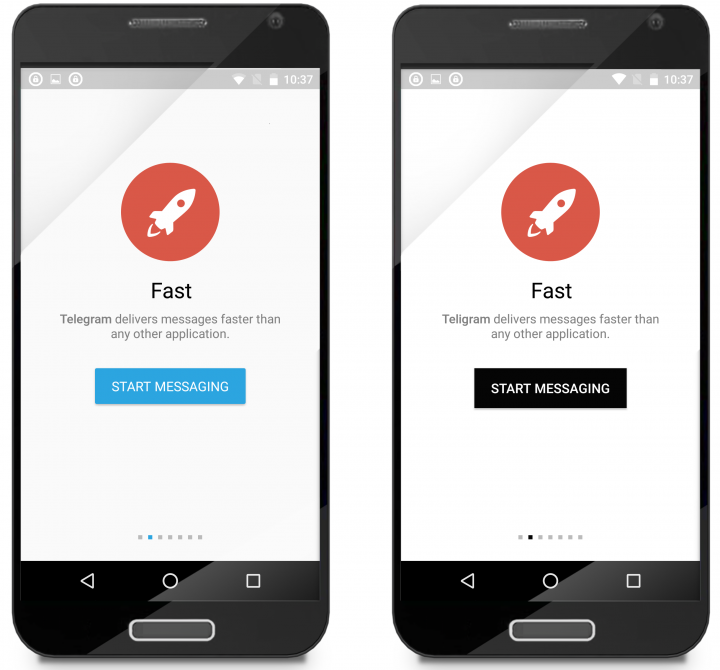
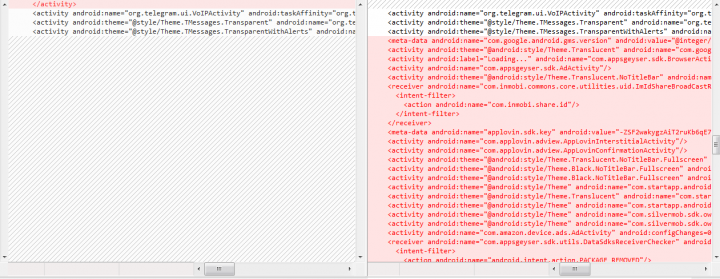
Comparing the apps’ manifests reveals that Teligram has added advertising libraries in order to create revenue for the fraudsters behind the deceptive app.
Teligram displays advertisements in two different ways, within the chat list and by showing intermittent full screen advertisements (Figure.6).

Google has removed the Teligram app from the Play Store.
Malware built on Telegram open source code
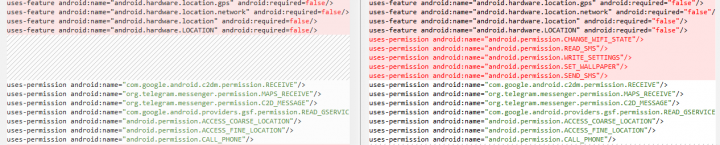
We also detected a malware sample built using the open source Telegram code, which is distributed on third-party app stores (detected as Trojan.Gen.2). The malware uses the same package name (org.telegram.messenger) and icon as the official Telegram app but requests more sensitive permissions and has added malicious receivers and services (see Figure.7).
While open source projects can be of huge benefit to developers and consumers, they can also be used by criminals to create convincing imitations of trusted apps.
Once installed and launched, the malware decrypts a URL from a byte array. It then downloads an external JAR or DEX file from the URL and invokes the payload, which can enable the malware authors to carry out a variety of actions, such as installing a backdoor or an ad clicker.
Compared to this malware, Teligram users are lucky as advertising revenue appears to be the main motive behind the app. Although no malicious behavior has been added to Teligram, its developers could potentially add any behavior they wish.
While open source projects can be of huge benefit to developers and consumers, they can also be used by criminals to create convincing imitations of trusted apps. Users should take care to ensure the app they are downloading is exactly what they think it is.
Protection
Symantec has the following protection in place to protect against the malware mentioned in this blog:
Mitigation
Before installing applications, especially for open source projects, be sure to confirm they are official by checking the following:
- Developer name. The developer’s name is listed on the download page for the app on the Google Play Store. Do an internet search for the official creator of the app and make sure the developer name matches up with what is shown on Google Play.
- Comments. Check the comments section on the app’s download page. If the app has any suspicious functionality or doesn’t perform in a similar manner to the real app users will tend to leave negative feedback here.
- Ratings. Although fake apps can receive high ratings, the number of ratings tend to be much lower than the legitimate version.
Users can also stay protected from mobile malware by taking these precautions:
- Keep your software up to date
- Do not download apps from unfamiliar sites
- Only install apps from trusted sources
- Pay close attention to the permissions requested by apps
- Install a suitable mobile security app, such as Norton, to protect your device and data
- Make frequent backups of important data







We encourage you to share your thoughts on your favorite social platform.