Mobile Privacy: What Do Your Apps Know About You?
Just how much personal information are your apps gathering? And do they really need so much?
The average smartphone user these days has between 60 and 90 apps on their device. Most of these apps request some sort of information about you and the device you are using. They may want to know your name, your email address, or your real-world address. But because smartphones are so powerful, they can also get quite a bit more than that, such as your exact location. Some apps will even request access to the device’s camera or microphone.
While all of this is done with the user’s consent, you may be surprised at the level of access some apps have to personal data. Did you know that 45 percent of the most popular Android apps and 25 percent of the most popular iOS apps request location tracking, for example? Or that 46 percent of popular Android apps and 25 percent of popular iOS apps request permission to access your device’s camera? Some Android apps even ask you to give them access to your SMS messages and phone call logs.
Under the microscope
In order to find out what kind of data your apps may be looking for, we decided to put the most popular to the test. We downloaded and analyzed the top 100 free apps as listed on the Google Play Store and Apple App Store on May 3, 2018. For each app, we tried to find out two main things: how much personal information was the user sharing with the app and which smartphone features the app accessed?
Neither practice is inherently suspicious. In most cases, information is shared and device permissions are enabled with the user’s consent. And there is usually a very good reason why apps require either. For example, a taxi app will need to be able to access a user’s location in order to tell the driver where to go. Instead, we were more interested in whether any apps were requesting excessive access to information or if app developers were doing everything they could to protect users’ privacy.
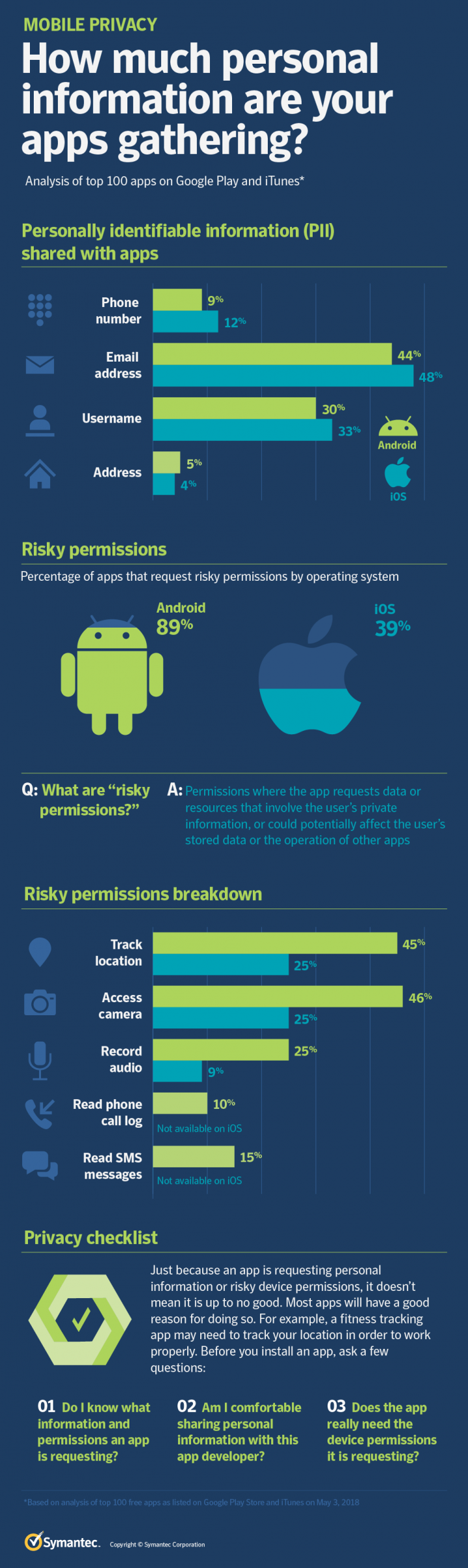
Personal information
One of the first things we looked at was the amount of personally identifiable information (PII) that apps requested users share with them. Email addresses were the most common piece of PII shared with apps and were shared with 48 percent of the iOS apps and 44 percent of the Android apps analyzed. The next most common piece of PII was the username (which is usually someone’s full name as they’ve entered it on social networking sites or on the app), which was shared with 33 percent of iOS apps and 30 percent of Android apps. Phone numbers, meanwhile, were shared with 12 percent of iOS apps and 9 percent of Android apps. Finally, the user’s address was shared with 4 percent of iOS apps and 5 percent of Android apps.
However, these stats don’t fully account for the full amount of PII being shared with apps.
Several apps integrate with social media so that the user can log into the app using their social media account and allow the app to post directly to the social networking site. For the user, this means they don’t need to manage passwords for every app, can invite friends to play mobile games, and share app info on their timeline.
But this symbiotic relationship also allows the app to collect user data from the social media account, while also allowing the social media service to collect data from the app. In the case of iOS apps using social media integration, we were able to see what PII was being shared. However, in the case of Android apps, we weren’t. This was because the apps in question all employed Facebook’s widely used Graph application programming interface (API) and the Android version of Graph uses certificate pinning, which prevented us from seeing what PII was being shared (we’ll discuss certificate pinning in more detail later).
Therefore, when we say that email addresses are shared with 44 percent of the Android apps, that figure could be higher because some Android apps use the Facebook Graph API and this may share an email address with them too.
Facebook Graph may be familiar to some people because it was used by Cambridge Analytica to compile personal information relating to 87 million Facebook users. This information was reportedly then used in targeted social media campaigns directed at voters during the 2016 U.S. presidential election campaign. Facebook responded to this incident by significantly tightening up its API and restricting the amount of personal information that can be shared through it.
While Facebook Graph may be the best-known integration service, it isn’t the most widely used. Of the apps we analyzed, 47 percent of Android apps and 29 percent of iOS apps offered the Google integration service, while 41 percent of Android apps and 26 percent of iOS apps offered the Facebook Graph API service.
Some permissions are more risky than others
Aside from personal information, apps will also need permission to access various features on your mobile device. For example, if you want to take a picture using Instagram, the app will need permission to use your device’s camera.
There is a massive amount of permissions an app could request, but not all permissions are the same. For that reason, we took a closer look at what we term “risky permissions” - permissions that could provide access to data or resources that involve the user's private information or could potentially affect the user's stored data or the operation of other apps. Examples of risky permissions include access to the user’s location, contacts, SMS messages, phone logs, camera, or calendar.
What did we find? Camera access was the most requested common risky permission, with 46 percent of Android apps and 25 percent of iOS apps seeking it. That was closely followed by location tracking, which was sought by 45 percent of Android apps and 25 percent of iOS apps. Twenty five percent of Android apps requested permission to record audio, while 9 percent of iOS apps did. Finally, 15 percent of Android apps sought permission to read SMS messages and 10 percent sought access to phone call logs. Neither of these permissions are available in iOS.
Two things should be stressed when talking about risky permissions. Firstly, they require the user’s permission to access this data. And secondly, just because we’ve called them risky permissions doesn’t mean they shouldn’t be granted. As explained before, there’s usually a reason they’re required. Instead, they should be seen as permissions the user should exercise more caution about granting, asking themselves if the app really does need this permission and if they’re comfortable granting it to this particular app. For example, do you really want to give an app access to your calls and text messages simply to provide personalized alerts?
Interestingly, in cases where we were analyzing both the Android and iOS versions of apps, some Android apps requested more risky permissions than their iOS counterparts. Seven Android apps requested access to SMS messages, while their iOS versions did not. One Android app requested access to phone call logs, while its iOS version did not. While neither permission is available in iOS, it does beg the question of why these permissions were requested in the Android version while the iOS version can do without them.
Are all permissions necessary?
Do some apps request too many permissions? We took a closer look at several that seemed to request a lot. The first was the Android horoscope app “Zodiac Signs 101 – 12 Zodiac Signs & Astrology", which has been downloaded more than 1 million times. Among the permissions it sought were:
- Precise user location
- Access to user’s contacts
- Send and receive SMS messages
- Receive MMS messages
- Permission to directly call phone numbers
- Permission to reroute outgoing calls
- Access to phone call logs
- Access to camera
- Read/write contents of USB storage
- Read phone status and identity
The second example we looked at was the Android flashlight app "Brightest Flashlight LED - Super Bright Torch", which has 10 million installs. Included in the list of permissions it sought were:
- Precise user location
- Access to user’s contacts
- Send SMS messages
- Permission to directly call phone numbers
- Permission to reroute outgoing calls
- Access to camera
- Record audio via microphone
- Read/write contents of USB storage
- Read phone status and identity
Ultimately, it may be up to the user to ask if these additional features are essential to the function of the app and if it’s worth granting permissions for features that only provide marginal benefits.
Do these apps really need all of these permissions? In each case, there were features in the app which made use of the permission. For example, Brightest Flashlight LED offers the user extensive customization options and the ability to make it flash in different ways when the user receives incoming calls or texts. In order to do that, it would need access to calls and messages.
Are some app developers adding features simply to gain access to permissions? It’s a possibility, but something we can’t provide a definitive answer to. Ultimately, it may be up to the user to ask if these additional features are essential to the function of the app and if it’s worth granting permissions for features that only provide marginal benefits.
Lax security practices
Worryingly, a small number of the apps we examined employed very poor security and privacy practices. Four percent of the Android apps and 3 percent of the iOS apps requesting risky permissions didn’t have any privacy policy. Ideally, every app should have a privacy policy which states clearly what data is being collected, where it is being stored, who it is being shared with, and so on.
Meanwhile, only a minority of apps implement certificate pinning at login: 8 percent of Android apps and 11 percent of iOS apps. What is certificate pinning? It’s a security precaution that helps prevent attackers intercepting supposedly secure communications. It does this by ensuring the app only communicates with a server using the correct security certificate.
However, there are differing opinions about certificate pinning. For example, Apple says it doesn’t recommend that apps do their own certificate pinning, as it’s an approach that can lead to overall fragility and problems in enterprise environments.
Bamboozled by privacy policies
Even when apps do have privacy policies, users can still find it difficult to keep track of what they are consenting to. While each app has its own set of permissions and privacy policies, there are several complicating factors.
- While some apps are self-contained, there are many that require additional apps or links to third party websites to function correctly (e.g. display advertising) or provide additional functionality, such as installing themes or providing additional levels in games. Some of these may be third-party apps.
- Each additional app may have its own privacy policy (or none) and the user cannot assume the top-level app’s privacy policy covers subsequent app downloads.
- However, most apps will disclaim any responsibility for use of the data by third parties.
In short, while you may be sure of your ground when it comes to a single app with a single privacy policy, once additional apps are plugged into it, the picture becomes increasingly complex, particularly when it comes to third-party apps.
Is this something to be concerned about? A significant number of apps that request risky permissions are tied to third-party apps. Of the Android apps that require risky permissions, 40 percent have links to third-party apps. Either normal app functionality is interrupted with advertisements or there were links to third-party apps for normal functionality (for example purchase links to seller sites). Meanwhile, 16 percent of the iOS apps that require risky permissions have links to third-party apps.
Guarding your privacy
How to avoid granting excessive permissions
Before you install an app:
- Read the permissions required for the app.
- Think about why an app needs the permissions it requests. If the permissions seem excessive, ask yourself if it’s likely they are there simply to acquire data about you.
- Read the privacy policy. If there's none, or if it's impossible to determine from it where your data will go, don't install the app.
If you have already installed the app:
- In the case of Android apps, you can remove unnecessary permissions by going to the Settings menu and then clicking on Permissions. Removing permissions may cause a poorly designed app to stop working. Well-designed apps will indicate if they need a permission when you attempt to perform the function that requires it.
- In the case of iOS apps, you can remove unnecessary permissions by going to the Settings menu and then clicking on Privacy.
How to protect your personal information
- Read the privacy policy on each social networking site and app you use.
- Ideally, don't sign into an app using your social networking site account. If you do, check what data the app will receive from the social network account.
- If you do sign into apps using your social network account, be frugal about how much information you provide in your public profile on social networking sites.
- When you post data to a social networking site from an app, think about whether you want the social networking site to have this information about your app.
How to check what apps are using data from your Facebook account
- Go to the small down-arrow at the top right of the homepage and select Settings.
- Select “Apps & Websites in the menu on the left to discover what apps are actively using your data.
- Select each app to view and edit the permissions on the data it uses.
How to check what apps are using data from your Google account
- Visit https://myaccount.google.com/permissions
- Here you can review and edit what third-party apps have access to your Google account.
You can also review and edit which apps are using Google for sign in and what information is being shared with them.







We encourage you to share your thoughts on your favorite social platform.