Living off the Land: Attackers Leverage Legitimate Tools for Malicious Ends
Living-off-the-land techniques remain popular, with Symantec blocking 480,000 PowerShell commands in one month alone
“Living-off-the-land” tactics—where attackers take advantage of native tools and services already present on targeted systems—have been used by both targeted attack groups and common cyber criminal gangs for some time now. Symantec has previously published research that gives a general overview of living-off-the-land tactics and fileless attack techniques; however, our new research provides updated statistics on the dual-use tools utilized in these attacks—with a focus on PowerShell and Windows Management Instrumentation (WMI)—and how they are currently being used by different attack groups.
Malicious or benign?
The most frequently executed tools observed by Symantec in Q1 2019 were net.exe, PowerShell, the certification utility, the task scheduler, and the WMI command line (WMIC). However, only a fraction of the overall usage of these tools was malicious. The context and execution sequence must be considered when determining if usage is malicious or benign. To do this, we extract execution patterns from our data with the help of advanced machine learning, and the data is then analyzed by our AI-based Targeted Attack Analytics (TAA) component.
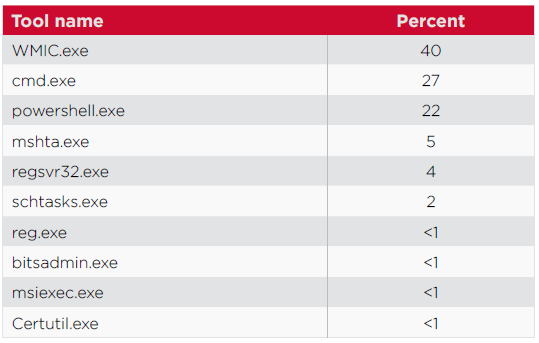
We also looked at more than 500,000 dual-use tool detections from the beginning of September 2019, which were either used to download or copy payloads to target computers. This revealed that WMI, the command line tool, and PowerShell were most frequently used for malicious purposes, accounting for 89 percent of all dual-use tools used as downloaders.
PowerShell
In September 2019 alone, Symantec blocked more than 480,000 malicious PowerShell scripts on endpoints. This number, while significant and steadily increasing, still only represents 0.8 percent of all observed PowerShell usage.
Symantec data from between September 2018 and September 2019 shows a 406 percent increase in the number of blocked PowerShell scripts, and this number is likely to increase even further.
We also analyzed 100,000 PowerShell command line arguments, keywords used, and frequency of occurrence of parent processes, to discover which were the most frequently used during attacks. Full details of this can be seen in the white paper.
WMI
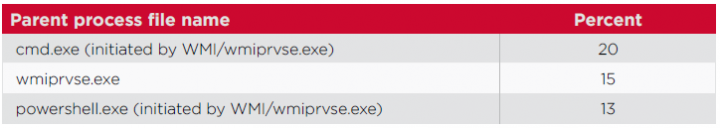
Interestingly, 48 percent of all malicious PowerShell commands were started through WMI. The tool is commonly used to spread PowerShell scripts laterally in internal networks. A typical process for executing a command on a remote system using WMI involves the remote system spawning an instance of wmiprvse.exe and then running the command which, as mentioned, is often a PowerShell command. This means that wmiprvse.exe is present in most process parent chains for malicious PowerShell scripts.
Targeted attack groups
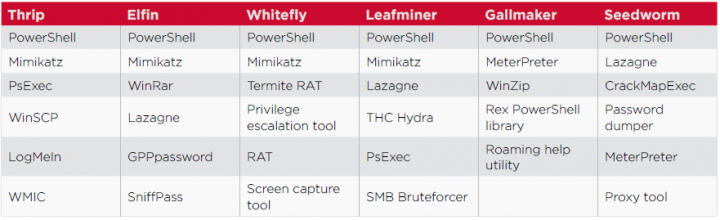
Targeted attack groups have been using living-off-the-land tactics for a long time, with almost all active groups having been spotted using dual-use tools at some point. Using these methods allows the attackers to hide their activity among legitimate administration work, and makes attribution difficult as there are no binaries to be analyzed and fewer indicators of compromise (IoC).
Looking at six active targeted attack groups and the living-off-the-land tools they use reveals that PowerShell is by far the most popular, with all six utilizing it in their attacks. In all, around 77 percent of targeted attack incidents made use of PowerShell. The credential-dumping tool Mimikatz, used by four of the groups, is the second most popular tool.
To learn more about the latest living-off-the-land tactics and techniques, download our white paper: Living off the Land – Turning Your Infrastructure Against You
Protection
Symantec solutions use multiple security technologies to defend against living-off-the-land and fileless attacks, including endpoint security, endpoint detection and response, email security, and network security.
Symantec Endpoint Protection solution includes various dedicated features that specifically tackle the living-off-the-land challenge.
- Symantec Endpoint Threat Defense for Active Directory restricts post-exploit incursions by preventing credential theft and lateral movement by combining AI, obfuscation, and advanced forensics methodologies at the endpoint to contain attacks in real-time.
- Deception technology uses baits to expose hidden adversaries and reveal attacker intent, tactics, and targets.
- Symantec Endpoint Application Control strengthens defense against advanced attacks by minimizing the attack surface and allowing only known good applications to run.
- Symantec Endpoint Application Isolation shields known good applications from tampering by stopping attackers from exploiting application vulnerabilities. It also isolates malicious and suspicious applications to prevent any privileged operations that can harm the endpoint.
- Non-PE file emulator de-obfuscates and detects JavaScript, VBScript, VBA Macro, and PowerShell threats.
- Command-line detection engine is specialized in monitoring dual-use tools and their behavior.
In addition to Symantec Endpoint Detection and Response (SEDR), Symantec’s Managed Endpoint Detection and Response Service (MEDR) leverages automated attack hunting provided by analytics as well as Symantec analyst security expertise to remotely investigate and contain incursions by adversaries in customer networks.
Mitigation
Symantec recommends users observe the following best practices to protect against targeted attacks:
Local environment
- Monitor the use of dual-use tools inside your network.
- Ensure you have the latest version of PowerShell and you have logging enabled.
- Restrict access to RDP Services. Only allow RDP from specific known IP addresses and ensure you are using multi-factor authentication (MFA).
- Implement proper audit and control of administrative account usage. You could also implement one-time credentials for administrative work to help prevent theft and misuse of admin credentials.
- Create profiles of usage for admin tools. Many of these tools are used by attackers to move laterally undetected through a network.
- Use application whitelisting where applicable.
- Locking down PowerShell can increase security, for example with the constrained language
- mode.
- Make credential dumping more difficult, for example by enabling credential guard in Windows 10 or disabling SeDebugPrivilege.
- MFA can help limit the usefulness of compromised credentials.
- Enable MFA to prevent the compromise of credentials during phishing attacks.
- Harden security architecture around email systems to minimize the amount of spam that reaches end-user inboxes and ensure you are following best practices for your email system, including the use of SPF and other defensive measures against phishing attacks.








We encourage you to share your thoughts on your favorite social platform.