The Revival and Rise of Email Extortion Scams
Almost 300 million extortion scam emails were blocked by Symantec in the first five months of 2019.
An email arrives in your inbox, with one of your old passwords in the Subject line. Your curiosity is piqued, and you click into the message, only to discover that someone has allegedly hacked your webcam and recorded you engaged in some intimate acts, and they are now threatening to send this recording to everyone in your contact list. However, if you send the anonymous blackmailer a few hundred dollars in bitcoins they promise that no one will see the embarrassing footage.
This is a situation many people found themselves in over the last year, as we witnessed a revival and evolution in email extortion scams, which are exactly what they sound like: scam emails that attempt to extort cash from victims. These sorts of scams have been around for many years, but the scenario outlined above—often referred to as a "sextortion" scam—is one of the main types of extortion scams we have started seeing more frequently again since about mid-2018.
When we look at the number of these kinds of scams that have been blocked by Symantec since the start of this year, we can see the trend is going upwards, with a spike visible during a two-week period in February especially notable.
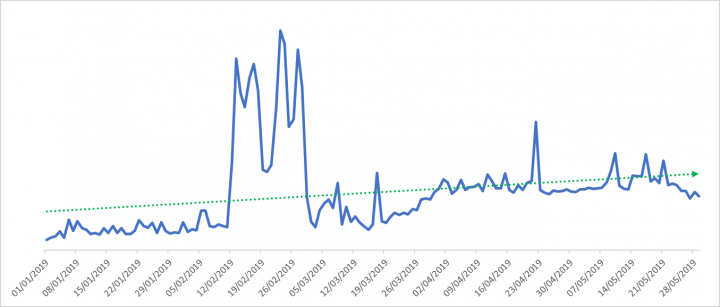
Between January 1 and May 29, 2019, just under 289 million of these types of emails were blocked by Symantec technologies. Just over 85 million of these emails (almost 30 percent) were blocked during this 17-day period in February when we saw a big spike in these types of scams. We didn’t just see a surge in one particular type of scam in this period, but a surge in a few different variations of extortion scam emails, including:
- English language: Plaintext, no URL in body
- Bomb threat theme
- Using PNG and JPEG images: Email has a PNG or JPEG attachment, which contains the Bitcoin wallet address
- Using PDF attachment: Coin wallet address present in the PDF
- Use of SegWit Bitcoin address
How these scams work
Most of these sextortion-style scams follow largely the same pattern, with variations in the messages such as using attachments or obfuscated characters, etc., applied in an attempt by attackers to evade email protection technologies. For example, some spam filters might work by blocking emails with Bitcoin addresses in the body—hence why attackers may have then turned to using PDF attachments or obfuscated text to try to bypass the spam filter.
Most of these emails also contain a password or partial phone number previously (or perhaps still) associated with the email address the email is sent to. This is included to make it appear the attacker has access to private information about the recipient—when in fact they almost certainly obtained it from one of the many large password dumps of recent years.
In most of these scam emails, the attacker claims to have a recording of you visiting a porn website, though in some cases the attacker pretends to be a member of law enforcement who has found child pornography on your device.
The big exception to this is the bomb scare emails, where the sender claims to have planted a bomb in your building that will be triggered if the requested amount of money is not paid.
Some of the typical characteristics and features we have seen in these spam emails are outlined in the table below.
| Typical Characteristics | Email type variations | Obfuscation techniques seen | Cryptocurrencies requested |
|---|---|---|---|
| Email contains an old password/partial phone number associated with target account – likely swiped from a data dump | English language – plain text, coin wallet address in email body | Use of obfuscated and encoded characters | Bitcoin |
| Threatening tone – threaten to embarrass/expose you to family and friends | Foreign language – 13 different languages seen by Symantec (Chinese, Bosnian, German, Japanese, Italian, Spanish, Dutch, Russian, Korean, Swedish, Norwegian, French, Latvian) | Use of zero-width space (ZWSP) between letters | Litecoin |
| Sense of urgency – 24-48 hours to pay up – from hundreds to thousands of dollars requested | JPEG/PNG/PDF attachment – wallet address in attachment | Use of Cyrillic UTF characters | SegWit Bitcoin |
| Most follow a similar template (see Figure 2) | URL in body – claims link shows proof scammer has your info | Use of online clipboard – link in email brings victims to online clipboard with details of scam | SegWit Litecoin |
| Many English-language emails have poor spelling, unusual phrasing | Bomb threat theme (see Figure 3) | ||
| ZIP attachment – claims attachment contains proof scammer has your info |
Are these scams successful?
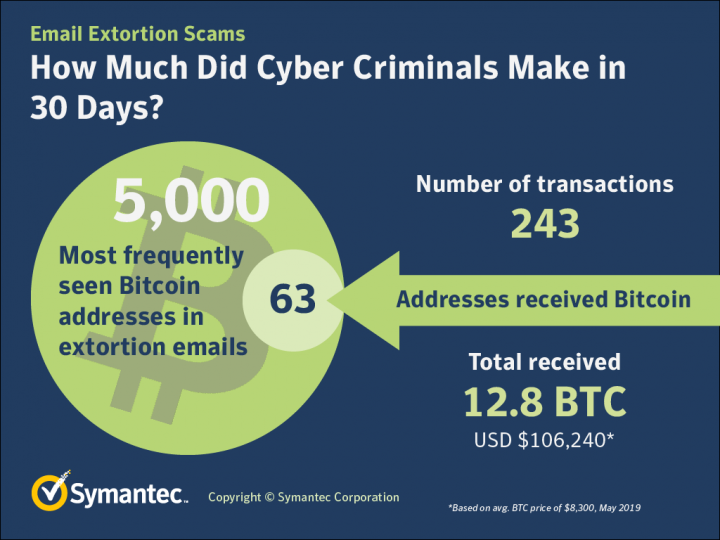
When it comes to the success of these scams, if we examine the 5,000 most-seen Bitcoin addresses in May, we can see that 63 of those wallets received bitcoins in 243 transactions. In total, the wallets received 12.8 bitcoins in that period—at the end of May one bitcoin was worth approximately US$8,300, meaning these wallets received a total of approximately US$106,240. If we take that as an average amount to make in a 30-day period for these kinds of scams, it means they are making just over US$1.2 million in a year ($1,292,586). For the amount of effort and skill that is required to carry out these scams, it represents a pretty good return on investment.
Almost all these wallets had been cleared out when we examined them at the end of May—it appears the criminals involved are not leaving any funds in these wallets for too long.
Who is behind these scams?
These scams don’t appear to be targeted—they are sent out as part of automated mass-mailing campaigns, seemingly using email and password combinations found in the many data dumps of recent years. The Necurs botnet was even reportedly being used to send these scams at one point. Some of these scams were reportedly also being used to spread the now-apparently-retired GandCrab ransomware, giving cyber criminals two chances to scam victims out of money.
As these email extortion scams are typical cyber crime activity, it is not clear exactly who is behind these attacks, but Symantec believes that a minimum of two cyber crime groups are engaged in this kind of activity, though there are potentially also many others. The barriers to entry for criminals are quite low for these scams—they do not necessarily require a huge degree of technical knowledge, and criminals only need a small percentage of them to be successful to make a profit.
These scams are still being actively sent, so consumers should be aware of these scams and the steps they can take to avoid falling victim to them.
Best practices
- Ensure you have strong email protection technologies in place, such as the products provided by Symantec, that will stop these emails from ever reaching your inbox.
- Do not open emails or attachments, or click on links in emails, that are unsolicited or from unknown sources.
- If you do receive one of these emails, do not panic, do not respond, do not click any links or open any attachments, and do not send money to the attackers. Mark the email as spam and, if you feel it is necessary, alert authorities about the email.
- Ensure all your online accounts are protected with strong, unique passwords, and enable two-factor authentication where possible. If you think your account has been compromised or your password revealed in a password dump, you should change it immediately.
Protection
Symantec proactively protects against email extortion scams with its email security suite of products:







We encourage you to share your thoughts on your favorite social platform.