'Congratulations, you won' Malware Scam Crosses Over to Android
Symantec mobile researchers observe an old scam popular among desktop malware making the jump onto Android devices.
Protect against "Congratulations You Won" malware with Norton Mobile Security.
"Congratulations, you won!" would normally be a welcome phrase to see when you go online, instantly making you think of an all-expenses-paid vacation someplace exotic, or perhaps a substantial amount to add a few more zeroes to your bank account. If only it weren't a favorite phrase among scammers too, you could actually already be on your way somewhere nice and sunny.
We have recently seen such "You won" scams increasingly being adopted by mobile threat actors on Android. We've been seeing queries from our end users and samples from our partners in the field growing significantly since the summer.
While scams like these have just begun crossing over to Android, they are quite well known and have a long history. In addition to the specific malware involved, we will also discuss some of the forces that drive the success of this particular type of scam.
While scams like these have just begun crossing over to Android, they are quite well known and have a long history.
Context
"You won" scammers use localization to zero in on their targets. The malware (Android.Fakeyouwon) discovered on our users' devices identifies device location/region using the device's IP. Once the region is discerned, scammers can tailor different scam campaigns accordingly. These may range from generic ad library revenue generation to fake coupons or rewards programs from well-known local shopping outlets.
In Singapore, for example, two of the most ubiquitous grocery stores include Giant and FairPrice. It is no surprise that scammers have homed in on these household names for their scam campaign.
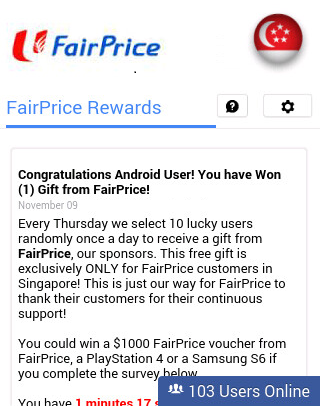
Users are shown a scam page that spoofs the FairPrice page, complete with the grocery chain's logo and an icon of the Singapore flag. The purported promotion even promises users who complete the supposed survey one of three things: a S$1000 (around US$750) voucher, a new gaming console, or a mobile handset. However, through the survey form, scammers collect users' personal information such as name, address, phone number, etc. The malware then sends the collected data to a remote server.
In other instances, scammers may also try to take advantage of recent trends in interesting topics. Examples used in this scam include fake offers for users to make money using the emerging Ethereum cryptocurrency.

Lending legitimacy
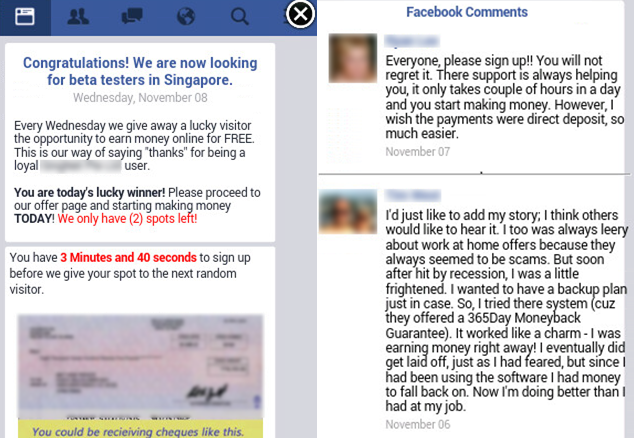
Once the victim has taken the bait, scammers try to reinforce the legitimacy of the content presented to the user. This usually involves making a reference to the large number of other people who are participating, either explicitly as Figure 1 demonstrates ("103 users online"), or implicitly, using spoofed pages of well-trusted platforms such as Google or Facebook. Scammers often craft fake testimonials and endorsements supposedly by other users that look like these were posted on the said platforms.
Once a victim takes the bait, scammers try to reinforce the legitimacy of the content presented usually by making a reference to the large number of other people participating, or by using spoofed pages of well-trusted platforms.
The strategy of "safety in numbers" can apply in protecting yourself, even when selecting reliable apps in the App store, but the strategy can also be exploited, as this case shows.
Excitement
Of course, the main human factor is the level of excitement or suspension of disbelief that results from an exceptional situation such as winning a cash award, being under a time pressure to sign up, or finding a lucrative business opportunity in an area that's popular, or in an area that you've been recently studying. Even the wisest and most skeptical users have a time window where they might click through a notice without reading, or punch in information that they wouldn't otherwise.
Deception
There are a number of other finishing touches that scammers put on the scam to reel in the victim, including:
Path onto the device: Applications hide themselves as legitimate apps in domains such as settings apps (Panel Settings), or apps that play music for free. Apps will also ask for the minimum amount of permissions, so as not to concern more discerning users on installation.
Timing/delay to trigger: Variants of the Fakeyouwon malware deploy a specific operational mode depending on the location and platform of the victim’s device. Some will present malicious web content immediately, while others will delay, with the goal of fogging up any association between mysterious/strange behavior and recently installed applications. The amount of time between web-content pop-ups is also configurable. The installed-app profile in different regions results in different levels of noise from a smartphone. Smart scammers will try to emulate typical behavior for the region and stay under the radar.
Presentation of successful scam content: We've observed behavior where scam content was presented immediately again if the user spent a significant amount of time on the page. Likely, there's even further sophistication and analysis behind deciding what content to serve to the customer.
Webview vs browser: Using a webview to present web content affords some protections to the scammer: since the address bar doesn't exist in the webview context, the user can't see a potentially alarm-raising URL. Additionally, typical anti-scam/spam technology focuses on browser as opposed to webview instances. There are examples of this malware that uses the browser instead of webviews. This indicates a confidence in the malware/ad networks on the part of the malicious actors (they're less worried about users sniffing out strange URLs). The web-hosted portion of the functionality involved in these scams utilizes web redirect responses (HTTP Response 302), as well as redirect meta-elements to hide and protect malicious content from web resources that might be associated with scams via analysis.
Leveraging device admin: Although it can be a tip-off revealing malicious applications, a presentation of the "device admin" dialog can pay off for the bad guy in the long run. If the user allows the app device admin, the app has free rein to overwrite dialogs, persist across safeguards against malware, and gain access to data that typical apps don't have. If an app asks for "device admin," the rule of thumb is to decline unless you understand why it would be required.
Mitigation
Above we've outlined a hostile and subtle set of actions and innovations designed to tease money out of mobile users' pockets and into malicious actors'. Take the following measures to protect yourself against this growing and evolving form of online threat:
- Keep your software up to date
- Do not download apps from unfamiliar sites
- Only install apps from trusted sources
- Pay close attention to the permissions requested by apps
- Make frequent backups of important data
- Install a suitable mobile security app, such as Norton, to protect your device and data
Protection
Symantec and Norton products detect the malware discussed in this blog as Android.Fakeyouwon.









We encourage you to share your thoughts on your favorite social platform.