APT41: Indictments Put Chinese Espionage Group in the Spotlight
Seven men have been charged in the U.S. in relation to attacks by China-linked espionage operation which Symantec monitors as two distinct groups – Blackfly and Grayfly
The U.S. government has charged seven men in relation to hundreds of cyber attacks against organizations in the U.S. and multiple other countries in Asia and Europe. Two of the men, who were based in Malaysia, were arrested and their extradition to the U.S. has been requested. The other five are based in China and remain at large.
The attacks were attributed to a China-linked organization dubbed APT41 and involved a combination of intellectual property theft and financially motivated cyber crime. While some of our peers monitor APT41 as a single operation, Symantec regards it as two distinct actors: Grayfly and Blackfly.
Grayfly
Grayfly has been particularly active in recent years, mounting high volume espionage attacks against organizations spread across Asia, Europe, and North America. They are interested in a wide range of sectors, including food, financial, healthcare, hospitality, manufacturing, telecoms, and government. It is known for using the Barlaiy/POISONPLUG and Crosswalk/ProxIP (Backdoor.Motnug) malware families in its attacks. Victims are frequently compromised by exploiting public facing web servers.
In recent attacks, Symantec has seen Grayfly deploy Backdoor.Motnug against targeted organizations in conjunction with publicly available Cobalt Strike malware. Backdoor.Motnug provides the attackers with comprehensive remote access to the network and creates proxy connections allowing access to hard-to-reach segments of a target network. In one attack against a telecoms provider, Grayfly was seen using an internal tool capable of interacting with an SMS database, demonstrating that intelligence gathering was the motive of the attack.
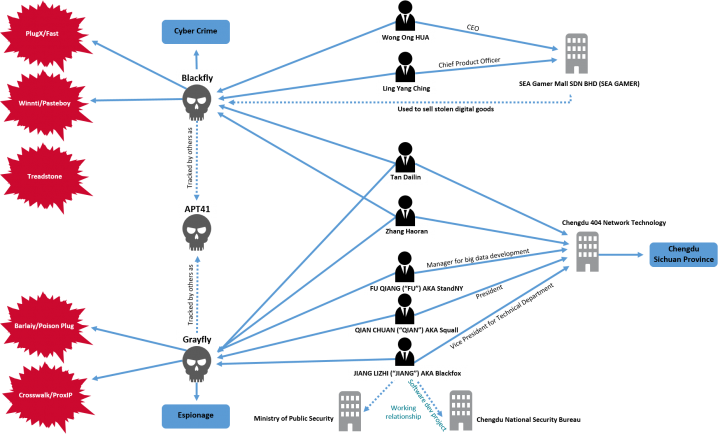
Prosecutors in the U.S. have charged three Chinese men – Jiang Lizhi, Qian Chuan, and Fu Qiang – with involvement in attacks that involve Grayfly tools and tactics. The trio are based in the Chinese city of Chengdu and all hold senior positions in a company called Chengdu 404. The company describes itself as a network security specialist and claims to employ a team of white hat hackers who can perform penetration testing along with “offensive” and “defensive” security operations.
The indictment alleges that the three men were also involved in attacks against over 100 different organizations in the U.S., South Korea, Japan, India, Taiwan, Hong Kong, Malaysia, Vietnam, India, Pakistan, Australia, the United Kingdom, Chile, Indonesia, Singapore, and Thailand. Jiang was said to have a “working relationship” with the Chinese Ministry of State Security which would provide him and his associates with a degree of state protection.
Blackfly
Blackfly has been active since at least 2010 and is known for attacks involving the PlugX/Fast (Backdoor.Korplug), Winnti/Pasteboy (Backdoor.Winnti), and Shadowpad (Backdoor.Shadowpad) malware families. The group is best known for its attacks on the computer gaming industry. However, Symantec has also observed attacks on the semiconductor, telecoms, materials manufacturing, pharmaceutical, media and advertising, hospitality, natural resources, fintech, and food sectors.
Recent Blackfly activity observed by Symantec saw the group deploy a slightly modified version of the Winnti malware against a telecoms organization in Taiwan. A feature of the attack was their use of the names of security vendors in naming files in an attempt to avoid raising suspicions. A dropper was signed with an invalid certificate with the subject "McAfee, Inc." The dropper then delivered several DLLs with file names that referenced Symantec software. The attackers had not compromised Symantec software, and were not leveraging it in the attack.
In a separate indictment, prosecutors allege that two Malaysian nationals – Wong Ong Hua and Ling Yang Ching – were involved in attacks that involved Blackfly tools and tactics. Wong is the founder and CEO of a company called Sea Gamer Mall, while Ling is its chief product officer and a shareholder. The duo are alleged to have collaborated with other attackers to mount a string of attacks against computer game companies in order to obtain in-game digital items, such as currencies, and then selling them for profit.
The link between Grayfly and Blackfly
While Grayfly and Blackfly appear to be distinct operations, the indictments allege that there is a link between the two groups. Two Chinese men – Zhang Haoran and Tan Dailin – are charged in a third indictment with collaborating with both groups. The two men are reported to have worked for a time at Chengdu 404, the company that prosecutors identify as linked to Grayfly attacks. However, they are also alleged to have collaborated with the charged Blackfly actors in order to make additional money by mounting attacks on computer gaming companies. The indictment alleges that in several instances, they used their unauthorized access to gaming company networks to kick other attackers off the network, effectively eliminating their competition.
Unwelcome attention
Grayfly and Blackfly have been prolific attackers in recent years and, while it remains to be seen what impact the charges will have on their operations, the publicity surrounding the indictments will certainly be unwelcome among attackers who wish to maintain a low profile. Symantec remains committed to tracking the activity of these groups in order to protect our customers from their attacks.
Protection/Mitigation
Symantec products protect against threats discussed in this blog with the following detections:
- Backdoor.Motnug
- Backdoor.Korplug
- Backdoor.Winnti
- Backdoor.Shadowpad
Indicators of Compromise
| Group | IoC |
|---|---|
| Grayfly | 9436d1602817a27eabeeec37aeea231d1c51374967fab88111aec6f69fd91266 |
| Grayfly | 09f43c6da5bd098b843782e60aa4bb3272d8d980ca518e2198a51935442aeb40 |
| Grayfly | 723f149e48dcb0d56634a0777c10e22544cd7fa20fb6ec8d18603d7f2853de13 |
| Grayfly | 6e4bc3236f579646a8ddfcaa1705b1fee51c54e4b7b5df73471ffe07c25b67ce |
| Grayfly | 7dffb681cc182f497129f54e6127589f654ca46d7cba4ba71080c853454c27b5 |
| Grayfly | 76bcda2ebfc327af2654b33e66860e0300e69e6c573a1f3b61db68826e6c2558 |
| Grayfly | 8e57ac0c473975e2c057fe3d540a42c56c943bfd429fff084fac177f3a22b947 |
| Blackfly | 50749284ea13d19eb7bcbf97c67fdcb711457a6ff2df1f71ebc66256787e164c |
| Blackfly | fc052b4ed84a45a1b0bcad8b5ffa18a5f57d753f0570ac627612b145a7cf7207 |
| Blackfly | b3547b6378168eb22e72cf1125c0f68c8159a001a7737ea3bb257fe1bc6d90c8 |
| Blackfly | 561294e08cadd3b03da9eec271bd0bf4d20a6509bed80f40f483bc7e17caa678 |
| Blackfly | bd739804e7a6e43a4338495603d96e230c48e020435c334354bb6676b5beeb46 |







We encourage you to share your thoughts on your favorite social platform.