The Living Off the Land Surge
Attackers adapt to new workforce trends to hide in plain sight
Stop me if you’ve heard this before: “2020 was a transformational year, changing the way people all over the world live and work.” Yes, we get it. The last year brought many disruptions to the workplace and left security teams scrambling to protect their new environments. But, what exactly were the biggest changes that brought these disruptions? Have attackers changed their tactics too? Symantec’s Threat Hunter team, part of Broadcom, just released new research on the growth of Living off the Land attacks, and the results are worth highlighting.
In essence, Living off the Land (LOTL) refers to attackers using either operating system features or dual-use tools (legitimate tools put to malicious uses). LOTL is by no means new. Our Threat Hunter team has been tracking it for more than five years, when it used to be a novel and niche attack tactic. Now we see it as one of the mainstays of sophisticated attack techniques.
In essence, Living off the Land (LOTL) refers to attackers using either operating system features or dual-use tools (legitimate tools put to malicious uses).
The appeal to attackers is obvious, as LOTL provides them with an opportunity to fly under the radar. A legitimate tool is less likely to raise suspicions (and less likely to trigger an antivirus detection). With attackers and employees using the same tools and processes, malicious activity becomes a needle in the haystack, hidden among the vast (and growing) legitimate activity on the victim’s network. Worst still, living off the land tactics enable attackers to curb the use of malware until much later stages in the attack chain, as in the case with ransomware, leaving the victim little or no time to respond.
While the Living of the Land research white paper (available here for download) goes into great detail on the most popular Dual-use tools leveraged by LOTL attacks, as well as provides several attack case studies, here are a few key takeaways:
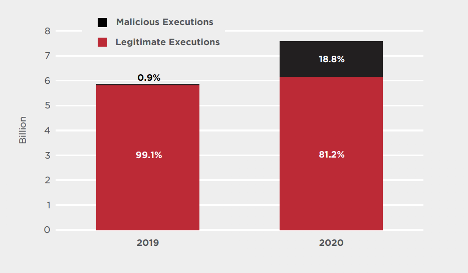
- Dual-Use tool use is exploding: 2020 saw a 29.4% increase in popular dual-use tools in customer environments. From 5.9 billion executions in 2019 to 7.6 billion in 2020.
- Malicious use of dual-use tools also boomed, but notably, grew exponentially compared to legitimate use. From 0.9% of total executions in 2019 to 18.8% of total executions in 2020.
- While a detection heavy security solution may alert on the possible misuse of these tools, the sheer numbers indicate that preventing execution is far preferable to having incidents created and putting the burden put on the SOC to distinguish between good and bad usage of legitimate tools.
So, what conclusions can be drawn from this new research?
- A boom in dual-use tools allows attackers to hide in plain sight. This trend is forcing changes in how to stop them.
- Protection will be critical in stopping these attacks. Detection may seem to be the answer, but the sheer number of malicious and legitimate usages makes treating each one as an incident impossible. Strong balance in both Protection and Detection is critical. (SES Complete recently completed the rigorous MITRE attack 3rd party testing and the results highlight why this balance is so important.)
- Device hardening is a key component of Protection. But no two customer environments are the same. Companies rely on dual-use tools differently, and a one-size-fits-all approach to security does not work. The next innovation in endpoint security will come in the form of custom protection that adapts to the customer's ever changing threat landscape. Stay tuned for more on this soon!

Multi-Factor Authentication: Headache for Cyber Actors Inspires New Attack Techniques
Two-factor or multi-factor authentication is used to secure organizations and accounts from attackers, making it a problem for malicious actors. Recent attacks show how they are attempting to bypass or avoid it completely.









We encourage you to share your thoughts on your favorite social platform.