Symantec and Anomali: Anomali Match Cuts Through the Noise
Aggregating data to identify and remediate APTs quickly
How often does it happen? You’re hard at work tracking down indicators of compromise (IOCs) when your CISO asks about a threat that has just been discovered – but which has actually been in the wild for six months. To find out whether your organization has been breached, you’ve got to scan historic data – if you have it. As scenarios like this become commonplace, cyber security analysts are becoming overwhelmed. There are simply too many attacks – and too much information‐ the proverbial needle in the haystack.
Symantec, as a division of Broadcom Software, believes that one of the keys to being able to not only identify if you have been breached, but do so in the fastest way possible is to ensure you have unified control points, security telemetry, analytics, and operations in one enterprise system. This is referred to as XDR, Extended Detection and Response and works well as you also leverage telemetry from all of your threat vectors.
Symantec also utilizes the Global Intelligence Network (GIN) for unparalleled visibility and protection. Applying artificial intelligence to analyze over 9 petabytes of security threat data, Symantec offers the broadest and deepest set of threat intelligence in the industry. This level of visibility across endpoint, email, and web traffic allows us to discover and block advanced targeted attacks that would otherwise go undetected.
Applying artificial intelligence to analyze over 9 petabytes of security threat data, Symantec offers the broadest and deepest set of threat intelligence in the industry.
When you have been breached, time is of the essence. Every second a threat remains active, malware can do its work, data can be exfiltrated and financial losses can add up. To mount an effective cyber security defense, you must identify breaches quickly. But the ability to review historic data is also essential. You need to do both. Fortunately, Anomali Match is here to help.
As the name suggests, Anomali Match equates the profiles of advanced persistent threats (APTs) to threat actors, then performs a retrospective search over hundreds of millions of events, turning up more matches for detailed investigation and remediation. By cutting through the noise, Match makes security analysts more efficient. Instead of sifting through reams of false positives, analysts can focus on threats that pose a clear and present danger.
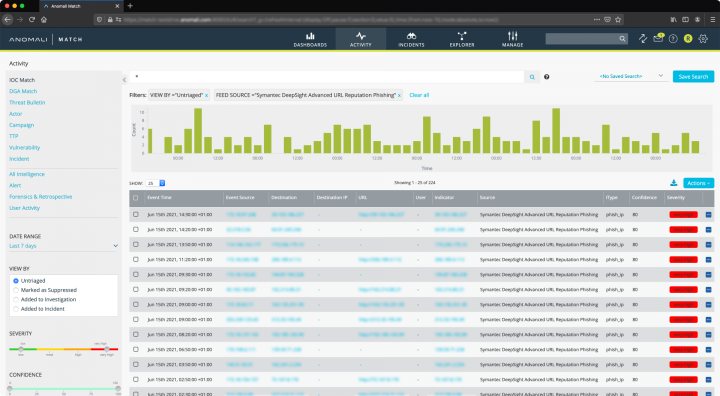
Match works hand‐in‐glove with Integrated Cyber Defense Exchange (ICDx), a software layer that normalizes telemetry data from a broad spectrum of threat vectors. ICDx brings that telemetry data together in one place, where it is fed into Match.
Match then applies artificial intelligence (AI) technology, including Machine Learning (ML) algorithms to the data in search of APTs. When threats are identified, automated workflows perform blocking and remediation through Symantec Endpoint Detection and Response (EDR).
To mount an effective cyber security defense, you must identify breaches quickly. But the ability to review historic data is also essential. You need to do both. Fortunately, Anomali Match is here to help.
Match helps complement existing security tools to increase threat detection and response. For example, SIEMs can struggle with handling threat intelligence at scale, and when threat intelligence platforms slow down performance, users tend to avoid them. However, Match is designed to perform at scale while retaining contextual information from the threat intelligence platform. And you might think that with the ability to correlate millions of events in real-time, Match would be a complex task to implement. Not so. In just four clicks, you can enable Match to pull data from ICDX.
With the ever‐increasing volume of threats and the correspondingly high noise level, it’s impossible to analyze each indicator of compromise (IOC) individually. With Match, you can identify threats quickly, scan historic data and apply defensive measures where they are most needed. Threats are multiplying and information overload is continuing to build. There’s simply no time to lose.

Threats Evolve. Shouldn’t Your Cyber Defense?
Integrations aggregate threat intelligence for deep analysis and fast response










We encourage you to share your thoughts on your favorite social platform.