How to Make the Most of Symantec CloudSOC CASB (Part 5)
Expanding visibility into managed SaaS applications for data at rest monitoring
In the previous blog, we discussed data governance aspects and how CloudSOC CASB provides expanded visibility into SaaS app user behavior and content management history. Continuing from the Securlet discussion we will provide additional benefits provided by CloudSOC Securlets. These include enhanced visibility into areas of policy compliance, User Entity and Behavior Analytics (UEBA), and threat detection. For example, CloudSOC Securlets provide automation for:
- Enforcing greater access control for SaaS app users
- Providing greater visibility into administrative actions
- Identifying your most exposed and risky users
- Visibility of SaaS users’ behavior across multiple SaaS apps
How do Securlets (API inspection) help?
The answer is Visibility, Policy Compliance, Content Inspection, Threat Detection
The Pareto Principle (aka 80/20 rule) is a principle that states 80% of all outcomes are derived from 20% of causes. CloudSOC Securlets help organizations understand which of their users present the most risk so that response measures can be initiated in the most impactful and efficient manner.
From a CloudSOC CASB perspective, Securlets not only collect immense amounts of user activity and scan data at rest (DAR) for view in the Securlet dashboards, they also share this information with other CloudSOC applications for more specific analysis, such as behavioral anomaly detection.
Below is a list of CloudSOC applications that consume data provided by CloudSOC Securlets’ API connectivity to SaaS applications
- CloudSOC Detect provides UEBA capabilities
- Securlets track user activity which is then provided to Detect to maintain a risk profile for each user. This helps organizations detect when users may be performing anomalous or risky behavior!
- CloudSOC Protect for acceptable policy usage enforcement
- Securlets provide both information for execution of notification policies and access for remediation of risk such as removing shared links or quarantine of malicious content.
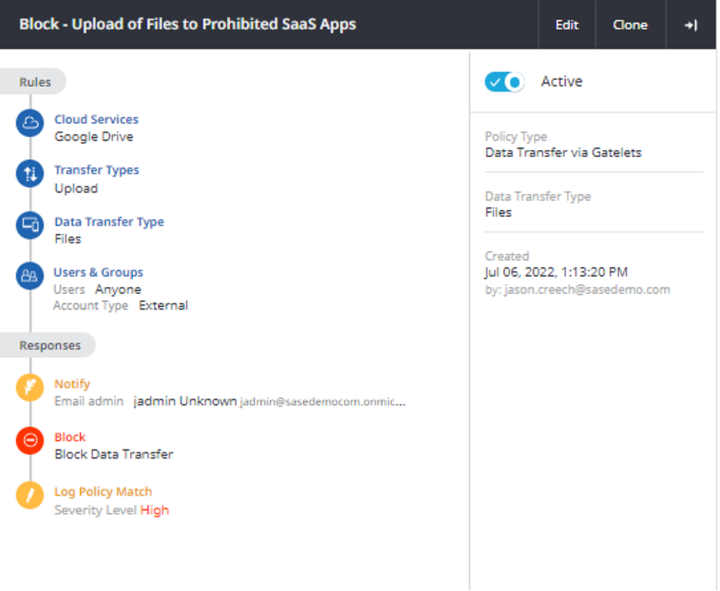
- CloudSOC Investigate for awareness of user activities and policy violation
- Each SaaS app API provides data in different ways. CloudSOC Investigate provides a normalized view of user behavior, content inspection policy violations, risky user detection in a normalized and consolidated audit log to assist with awareness and understanding of exposures the organization may be facing. The outcome is a better understanding of where risk may lie in terms of SaaS app user activity, acceptable usage violations, and data exposure.
- Note in the Investigate dashboard below, a color-coded trend line is presented with activities ranked by severity in bar chart views followed by activity listing. Via this view, high severity events can be selected, and granularity of each activity is provided which provides greater context so that higher priority issues can be addressed.
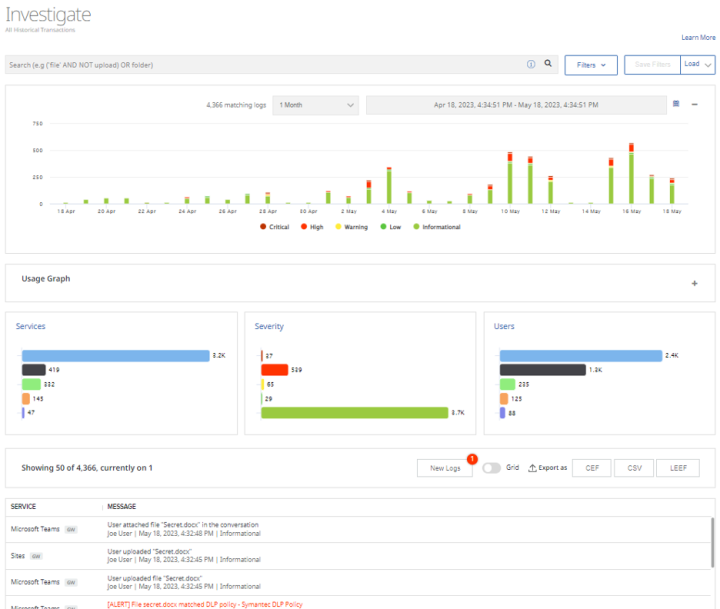
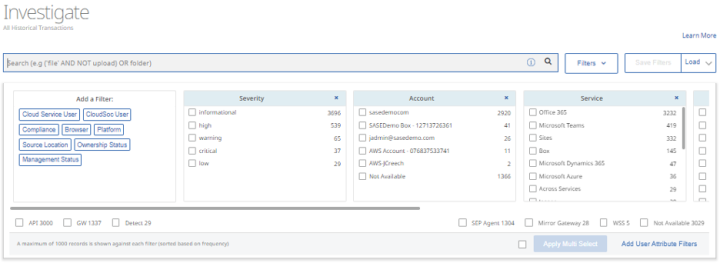
- In this Investigate dashboard, a key best practice is understanding use of dynamic filters to hide all but the top risks that need to be addressed. The advanced query bar supports Boolean search strings which can be saved as filter templates so more complex queries can be reused.
- CloudSOC integration with Symantec DLP for content inspection of Data at Rest (DAR)
- In part four of this blog series, we discussed some content inspection aspects Securlets provide via integration with Symantec’s Data Loss Prevention (DLP) solution - DLP Cloud. Prevention of data exfiltration has been one of the more prevalent use cases in the CASB market. Understanding how data is shared and the overall impact of risk exposure is a top concern. With DLP Cloud, content is detected and shared with the Cloud Detection Service for inspection using DLP policies. This content inspection occurs in the cloud, which efficiently minimizes the bandwidth consumed by other vendors’ approaches since the content is not sent over the organization's perimeter unless there is a content inspection policy violation.
- Note that data is not necessarily just in files. One of the benefits of understanding how CloudSOC Securlets work is that it can help administrators expand use cases. For example, the Office 365 Securlet can scan email subject lines and body for sensitive content. MS Teams messages can be scanned for risk as well.
- Additionally, DLP Cloud supports all DLP detection methods. This includes other methods such as EDM and OCR, which provide advanced methodologies for more efficient detections.
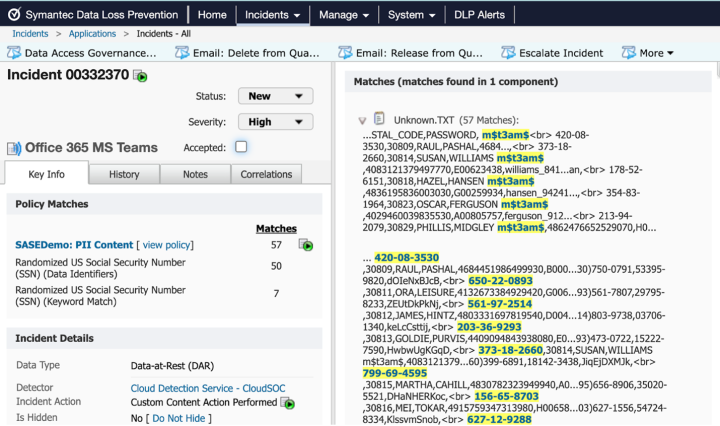
- In the screen snippet below, we can see an example of a content inspection incident in the DLP Enforce console. It describes the discovery of sensitive information in MS Teams messages. Note on the left-hand side, additional criteria of the content and user is provided which is unique to CloudSOC integration with DLP.
Look for the best possible outcome
The above information is a small percentage of what can be done with DLP Cloud’s Securlets, the CloudSOC applications and integration with DLP. The outcome of understanding these components and how best to use them is that resource utilization is maximized, content exposure is eliminated, and you have a better understanding of where risk may lie in your SaaS apps.
But not all SaaS apps are alike, in the next blog (Part 6), we will cover the IaaS Securlets (AWS, Azure, GCP) and show how, in addition to activity monitoring and content inspection capabilities, Securlets also provide Cloud Security Posture Management (CSPM) for these IaaS platforms to help security professionals understand how misconfigurations of the management plan can pose additional risk to their organization.

How to Make the Most of Symantec CloudSOC CASB (Part 4)
Expanding visibility into managed SaaS applications for data at rest monitoring










We encourage you to share your thoughts on your favorite social platform.