How to Make the Most of Symantec CloudSOC CASB (Part 4)
Expanding visibility into managed SaaS applications for data at rest monitoring
This blog discusses how to maximize the use of CloudSOC CASB through use of Securlets, CloudSOC’s proprietary term for API connectivity between CloudSOC and a managed SaaS application. Securlets provide granular visibility of SaaS app user’s historical activities in monitored SaaS apps as well as providing granular remediation capabilities to remove exposed or risky data.
The importance of a Securlet - Visibility, Policy Compliance, Content Inspection, Threat Detection
If Audit’s ShadowIT monitoring is in place or inline monitoring of data in motion via Gateway, is API connectivity to monitor SaaS apps needed?
The answer is yes, absolutely!! In fact, Securlet rollouts target inspection of Data at Rest (DAR) and retrieving user historical activities in the SaaS app, and while Securlet activation usually follows deployment of ShadowIT, implementation can precede deployment of ShadowIT monitoring. Securlets are fundamental as they provide:
- Visibility and control into your established SaaS apps where significant risk may already exist
- Monitoring of user activity for noncompliance with acceptable usage policies
- Scanning Data-at-Rest (DAR) for detection of sensitive content and exposures
- Detection of malware and risky user behavior for awareness of potential threats and risk
Visibility - You cannot protect what you don’t know about!
ShadowIT analysis, while a great phase one in a cloud security initiative, cannot provide the complete level of visibility and detail that API integration with a managed SaaS app can provide. Similarly, inline inspection methodologies provide real-time activity awareness for users following that connectivity path, but not users who may have access to the SaaS app via different channels nor for historical activity and exposures.
Securlets provide visibility into all user’s activities and the information they are managing. Additionally, API connectivity enables users to remediate existing exposures that may have been in place for years. It is extremely important to deploy Securlets so you can eliminate existing risk and content exposure.
Since many organizations have adopted the use of O365 as their collaboration platform, the examples below are presented in the O365 Securlet context. But, the topics discussed are also applicable to other sanctioned SaaS apps (like Google Workplace, Box, Slack, etc.) where API connectivity between CloudSOC CASB and the SaaS app can be established . Below is a screen snippet of CloudSOC’s O365 Securlet Dashboard.
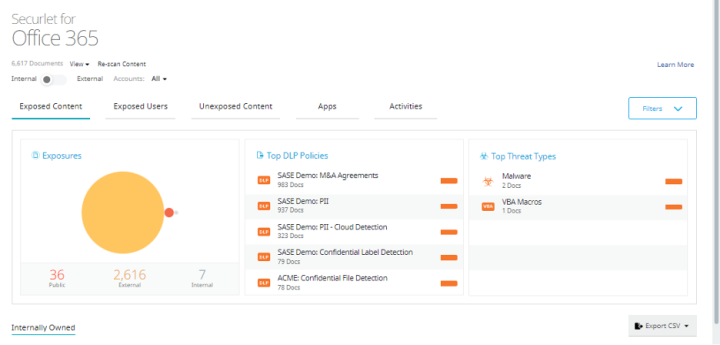
From a visibility perspective, we can see several things from the outset:
- 36 files are shared “publicly” (aka anonymously)
- 2,616 files shared to external domains such as partners or personal O365 subscriptions
- 7 files shared “internally” which means every user in the organization with the link, could see that file
There is also visibility into other significant aspects related to content exposure and threat detection:
- Several Data Loss Prevention (DLP) policies (PII, confidential data, etc.) have been violated
- Malware has been discovered sitting at rest in the SaaS app
This example represents a small demo environment, so numbers are small. It is not unusual to see file counts in the millions for larger organizations, especially those with hundreds of thousands of employees. So, how do you address mountains of findings? Using these dashboards, most organizations will prioritize remediation efforts for content inspection issues by grouping criteria. Some examples:
- Removing the public share link on shared folders since folder contents may inherit sharing
- Focusing on publicly shared files that also violate a DLP PCI/PII policies
- Triaging internally shared files that violate DLP policies focused on employee privacy law
Trends and Best Practices
Different SaaS apps often differ on how they do things, so it is not unusual to see variation. In the last two years, customers have been configuring O365 to not allow “any” public sharing of data. The first value in the dashboard displaying publicly shared files is often zero (0). In this case, a good best practice is to create a CloudSOC policy that notifies an admin if “any” file is shared anonymously to the public. In this way, if the primary configuration of O365 fails, the admin will know right away.
CloudSOC Securlets also provide deeper visibility into the details of user activities. Below is the O365 Securlet activities view for the O365 user activity that CloudSOC CASB is collecting.
This view provides visibility into general user activity as well as their compliance to Acceptable Usage Policies defined in CloudSOC Protect and/or in Symantec DLP. For example, in the CloudSOC Investigate app below, we see some policy violations in red that may warrant attention; but we also see some administrative activity that may be of interest if the person performing that activity was not authorized to do so. Note how each activity has “drill down” visibility into the underlying details of the activity.
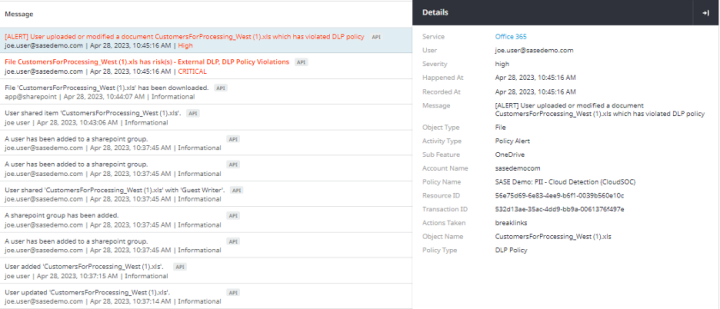
Overall, Securlets provide the granular visibility needed to identify SaaS app security issues for awareness and response. In the next blog article, we’ll continue to discuss additional views and benefits of Securlets. We’ll also go into how the information can be used by other CloudSOC applications and integrations such as:
- CloudSOC Detect for UEBA concepts.
- CloudSOC Protect for acceptable policy usage enforcement.
- CloudSOC Investigate for awareness of user activities and policy violation.
- CloudSOC integration with Symantec DLP for content inspection of Data at Rest (DAR)
If you have any questions about any of the topics discussed and would like more information, please see the white paper Cloud App Security with Symantec DLP Cloud or contact your Broadcom sales representative to schedule a more in-depth discussion of the CloudSOC/CASB offering.

How to Make the Most of Symantec CloudSOC CASB
What the Experts* Advise

How to Make the Most of Symantec CloudSOC CASB (Part 2)
First things first: Ensure complete visibility with CloudSOC CASB Audit










We encourage you to share your thoughts on your favorite social platform.