Symantec Mobile Threat Defense: A Snapshot of Mobile Security Incidents in Q1 2019
From the FaceTime bug to risky apps leaking millions of sensitive files from employee devices – mobile security threats kept us busy this quarter
It was an active winter for mobile security attacks: hackers exploited new and old ways to break into our mobile devices, creep on user privacy and threaten enterprise data, including using legitimate avenues such as Apple’s Developer Enterprise Program. Mobile security breaches spread across the threat landscape – some triggered by popular apps used every day, as well as by known OS vulnerabilities and network exploits. And, in case anyone doubted it, threats affected both Android and iOS, sparing no victims.
Here is a taste of notable mobile security incidents that happened this quarter, curated by Symantec’s Modern OS Security team, committed to the protection of modern endpoints and operating systems in enterprise.
Pirate App Stores Exploited Apple Tech to Distribute Hacked iPhone Apps
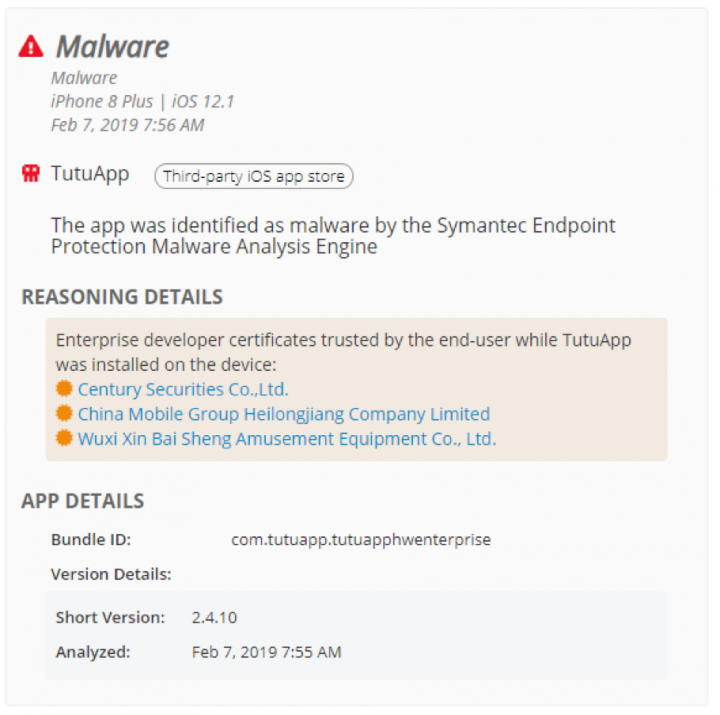
Hackers exploited Apple technology to distribute modified versions of popular apps like Spotify, Angry Birds, and Minecraft to enterprise employees. Using enterprise developer certificates, pirate app distributors such as AppValley and TutuApp provided hacked versions of apps to consumers, misusing Apple’s Developer Enterprise Program which was introduced to allow companies to distribute business apps to employees without needing to go through the App Store’s official review process. Once they are trusted by mobile users, enterprise developer certificates can be deployed to allow the use of sideloaded apps on iPhones, and so certificate misuse can open devices to malware and risky apps.
Incidentally, following the discovery of the Apple certificate exploitation, Symantec Endpoint Protection Mobile (SEP Mobile) detected the presence of 3rd-party app store TutuApp on a number of corporate-owned iOS devices among SEP Mobile’s global pool of customers. SEP Mobile also found a number of sideloaded apps on the devices after identifying suspicious enterprise developer certificates that were trusted by mobile users while TutuApp was installed. The 3rd-party app store was classified as malware and, based on the company’s compliance policy, access to corporate resources was blocked on the device to keep sensitive data from being exposed.
Golduck Malware Extended to iPhone Apps, Risking Customer Data
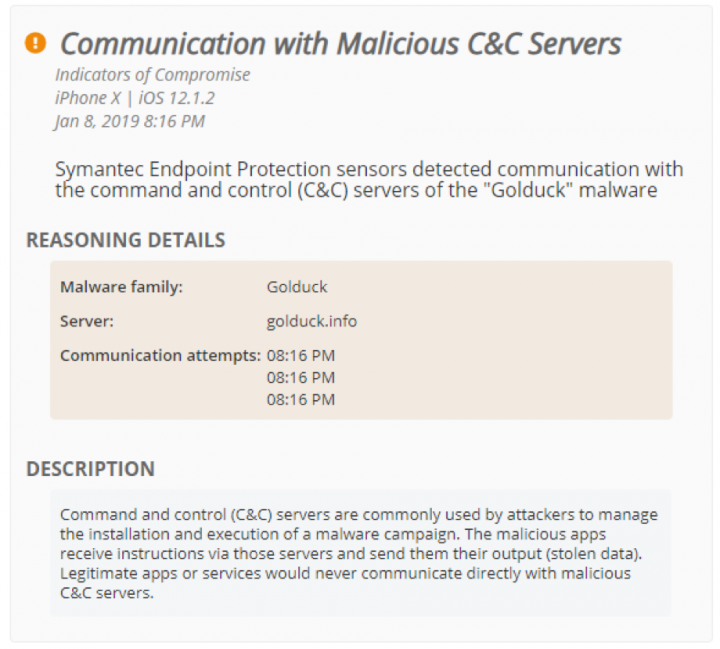
In January, security researchers identified several iPhone apps linked to Golduck, a traditionally Android-focused malware campaign, first discovered by Appthority (acquired by Symantec) in 2017. Popular game apps on iOS were found to be communicating with Golduck’s command and control server, which enables hackers to run malicious commands on a victims’ device, such as sending SMS messages to earn money. Malicious and risky apps remain one of the biggest and most common threats to enterprise mobile security, with one in 36 devices having a high-risk app installed.
Shortly after the iOS-Golduck link was discovered, SEP Mobile detected communication to Golduck’s C&C server from a number of iOS devices with SEP Mobile running on them. Our on-device protection action automatically and immediately blocked the app’s communication with the malicious C&C server, protecting both managed and unmanaged devices in real-time.
HospitalGown Vulnerability Leaked Sensitive Enterprise Data, Including Medical Records
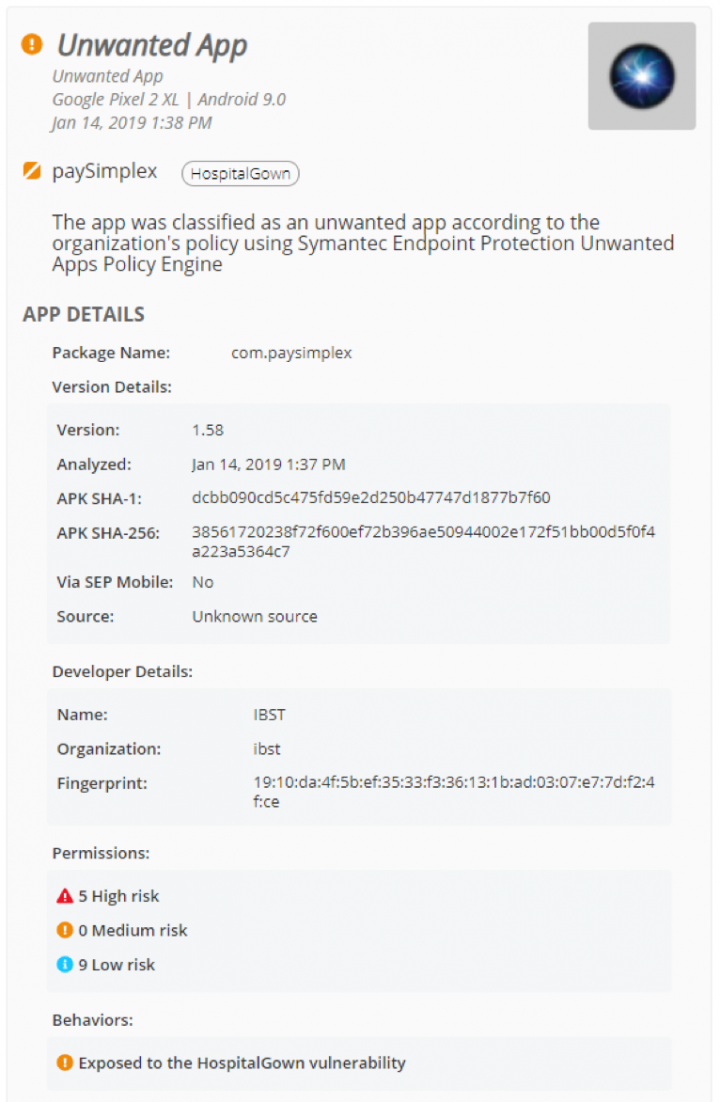
A new variant of the HospitalGown vulnerability, initially discovered by Appthority in 2017, was found to put enterprise app data at risk including financial documents, medical records, and customer invoice and billing details. HospitalGown data exposures occur when app developers fail to properly secure backend servers with firewalls and authentication. Research by Symantec found that apps connected to poorly-secured datastores have leaked more than 200 million data records, including 1.6 million user and employee login credentials.
After defining apps that are exposed to HospitalGown as “unwanted” in its environment, a SEP Mobile customer was able to prevent an app with this vulnerability from leaking sensitive corporate information. SEP Mobile detected the app as exhibiting risky behavior and blocked its communication on the device.
More than 100,000 Home Routers Hijacked by GhostDNS
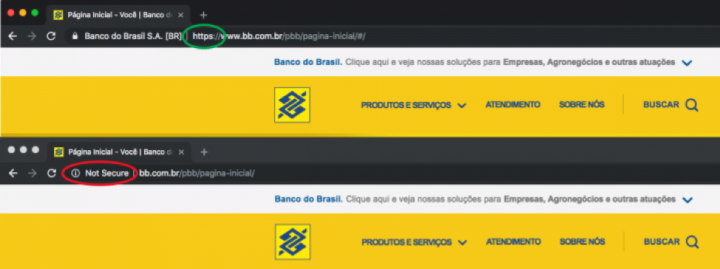
As the year began, researchers from the Modern OS Security unit detected untrusted DNS servers in networks used by Android devices in our install base. While trying to access the Banco do Brasil website through the network, the mobile users were redirected by the suspicious server to a different IP address, arriving at fake website that looked exactly like the legitimate bank site. The incident followed renewed activity by GhostDNS, a known DNS hijacking campaign, at the end of 2018. GhostDNS attempts to trick victims into entering their personal credentials on phishing websites that look identical to Brazilian bank sites. Hackers were able to easily break into more than 70 types of routers with known security vulnerabilities, allowing them to modify DNS settings and redirect victims’ traffic.
DNS hijacking campaigns like GhostDNS usually initiate their activity in vulnerable routers and affect all devices, not just mobile, connecting to the compromised networks. The untrusted DNS server detected by SEP Mobile was found to have similar attributes to GhostDNS. Our system activated network protection actions to secure the affected devices and alerted the admins that the router in the specific network may have been compromised.
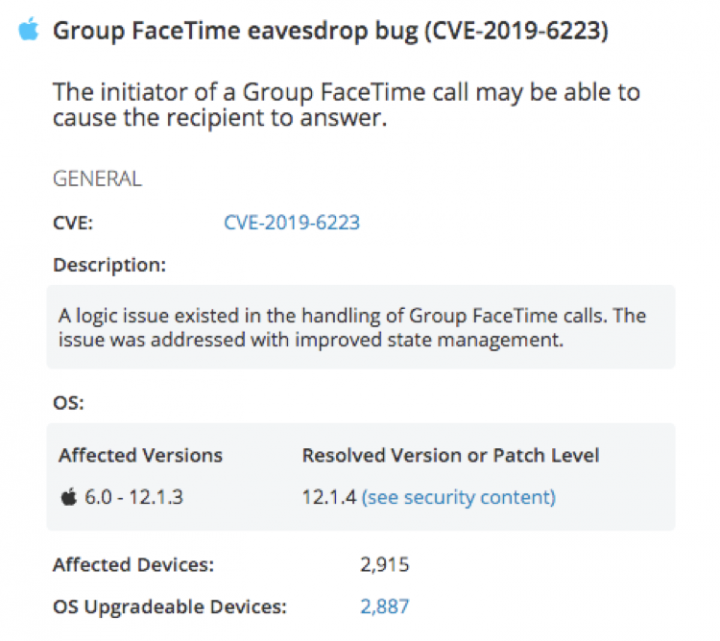
iPhone FaceTime Bug Allowed Hackers to Listen in on Private Conversations
iOS users received some unexpected news in January when a major security vulnerability in Apple’s popular FaceTime calling app was discovered. The vulnerability allowed users who initiated a Group FaceTime call between three or more people to access the microphone and front-facing camera of the person they were calling, without victims being aware of it. Once the vulnerability was exposed, Apple quickly took the Group FaceTime functionality down so that users wouldn’t be affected, and subsequently patched the vulnerability in the release of iOS 12.1.4. However, the incident underscores just how easily a mobile operating system vulnerability – across all operating systems – can be exploited to threaten user privacy and data.
Jailbreak for iOS 12 – iOS 12.1.2 Released
February saw the release of a new jailbreak for iOS 12, allowing iPhone users to unlock restricted access to apps and functionality not permitted by Apple – and opening the door to security exploits. While Apple constantly introduces new OS versions and more sophisticated security measures to patch iOS vulnerabilities, the frequency of these updates only highlights how often security flaws continue to appear on iOS (and Android for that matter).
Security Professionals are Taking Note: Mobile Tops Enterprise List of Concerns
Verizon’s 2019 Mobile Security Index made our list of highlights because it demonstrates organizations’ increasing concern over mobile threats. The report found that the majority of organizations (41%) rank mobile devices as their biggest cyber security challenge. Still, organizations are not doing enough to protect themselves against mobile risks, with two-thirds saying they are less confident about the security of their mobile assets than other devices.
*** The above list is just a small sample of incidents among many other stories that made headlines this quarter – such as Facebook’s collection of personal data via “research” VPNs installed on iPhones, a high-risk Android vulnerability that went undetected for years, and iPhone apps using analytics SDKs to record users’ screens without them knowing – reminding us that mobile attacks reach across all threat vectors and operating systems. Bearing these risks in mind, organizations need to make sure they have the right tools and protections in place to effectively secure their data.
SEP Mobile customers can stay on top of the latest mobile threats through the Mobile Security Headlines tab in their environments. We’ll return with a highlight of next quarter’s top threats at the end of Q2.









We encourage you to share your thoughts on your favorite social platform.