Three Hidden GitHub Risks and What You Can Do About Them
Security best practices for GitHub you should know
The best thing about GitHub is how easy it is to collaborate on source code. But this ease has hidden security risks. Firstly, the source code stored in GitHub often contains proprietary or business sensitive data and securing these assets becomes a priority. Secondly, as repositories could also be home to sensitive developer - or runtime - centric data such as API keys, Private Keys, OAuth IDs etc and intellectual property (like source code), exposure of this content could result in privacy breaches, compromised confidential data and other forms of abuse. Thirdly, because GitHub is often set up as a Trusted Site to make it easy for developers to collaborate, this access point can be abused by attackers trying to infiltrate malware into your organization.
DLP Cloud secures your Enterprise Github Cloud instance by providing access governance, Data Loss Prevention (DLP) content inspection and Threat Protection to any GitHub instance via two paths:
- API: Enterprise GitHub Securlet with content inspection for DLP and Threats
- Gateway: GitHub Gatelet for inline content inspection and adaptive access control
Building out your GitHub security system
There are 2 primary threat models that you need to guard against:
- The exfiltration of sensitive data through either exposure of Enterprise GitHub repositories to the Internet or exfiltration via uploads to commercial business-foreign GitHub repositories
- GitHub is used to spread malware due to the fact that GitHub often is in the Trusted Sites of your browser to allow Developers to freely interact with their repositories leaving the door open for attackers to use the wildcard in their advantage
Your security strategy should center around these 4 aspects:
- Governance: Actionable visibility and insight in the use of GitHub within your organization
- Access Control: Apply appropriate controls to GitHub that support user productivity (recognizing that developers’ access will differ from the general user profile)
- Data and Credential Protection: Safeguard business sensitive data (that may be embedded in source code) and intellectual property from exposure
- Threat Protection: Prevent the spread of malware that may be distributed using GitHub
Securing GitHub with Symantec DLP Cloud
DLP Cloud includes a powerful combination of capabilities that range from audit, access controls, user behavior analytics, inline content scanning and direct inspection of applications for data and malware risk. In this section we’ll show how it supports the four stages of your security strategy.
Governance - Actional Visibility and Insight
How is GitHub being used in my organization?
CASB Audit provides visibility and insights into the users, their usage details in terms of uploads/downloads and Business Readiness Rating for SaaS apps. This ShadowIT tool can be leveraged for awareness into the various accounts and repositories that have been accessed and by whom. This data can be used by Admins to determine whether to Sanction or Unsanction these accounts.
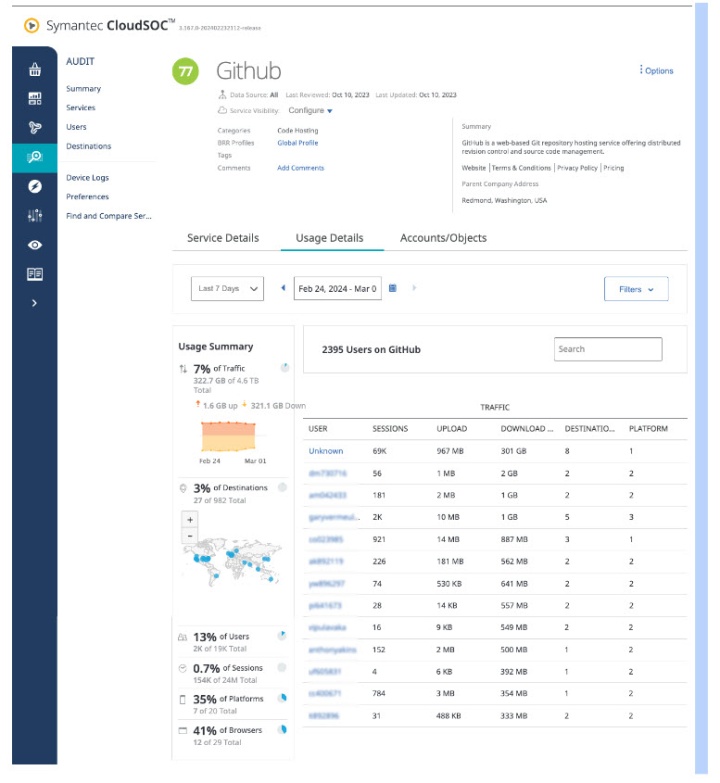
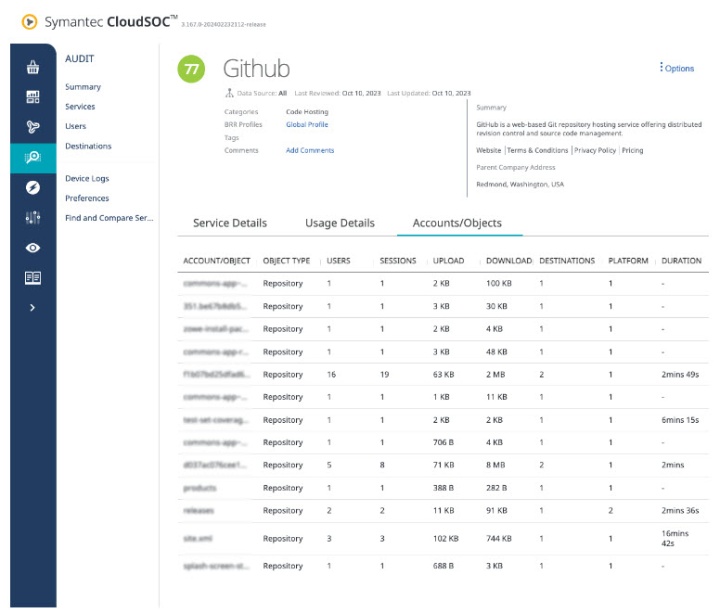
Do I have any high risk users?
DLP Cloud uses supervised and unsupervised machine learning to analyze user's GitHub activities (with User Entity Behavior Analytics, UEBA). This analysis, performed by Risk Vectors and Detectors, will establish a baseline for acceptable behavior and assign Risk Scores to collaborators of the Github instance. These Risk Scores can then be used to drive adaptive policies. Additional Risk Vectors and Detectors can be created and tailored by a customer to meet their specific use cases and to ensure the system can evolve with a rapidly changing security landscape.
Access Control
Who is using GitHub?
While your engineering business continues, the CASB GitHub Securlet monitors the activated corporate instance and reports on common activities performed such as repositories-created, pull-requests-merged, collaborators-added and several others documented here. Policies can be created alerting Admins on any violations. CASB GitHub Gatelet monitors inline traffic and access can be enforced to limit GitHub to Sanctioned accounts and repositories only or from specific users or with specific client side software (i.e. Git client or browsers). Access to other accounts and repositories can be blocked preventing any kind of unsanctioned uploads or downloads. Additionally, policies can target blocking of certain activities and are documented here.
Data and Credential Protection
What is being sent or stored in GitHub?
Scanning the content in the source code or any other files pushed to corporate repositories for dev-centric sensitive identifiers (for e.g. keys, secrets etc.) or detection of any content deemed sensitive (for e.g customer info in test files containing PII etc.) can be set up using industry leading Symantec DLP to alert on any violations for visibility and compliance. Cybercriminals or malicious insiders with access can find ways to exploit sensitive data thereby increasing corporate risk. The DLP Content Pack has been improved to include various dev-centric data identifiers.
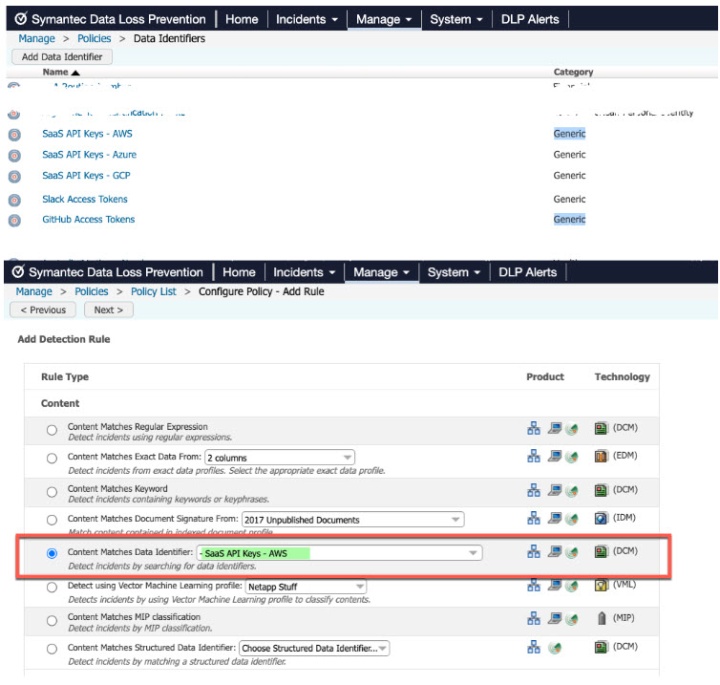
What about non-corporate GitHub accounts?
While the CASB Github Securlet or API based approach works well with when the corporate-account has been activated, what if data (code or other corporate files containing sensitive info) were uploaded to non-corporate Github accounts which can’t be addressed via API channels? This is when the Github Gatelet can be used to sanction a list of allowed vs. blocked accounts and the SaaS delineation for Github can be used in policies to allow corporate access to certain accounts. In addition this method can also be used to inspect from any 3rd party repository for files that are being downloaded like malware.
How do I inspect the GitHub Command Line Interface (CLI)?
As a majority of developers use the command line interface to communicate with GitHub, CASB Gateway also supports decoding of the proprietary GitHub protocol and sending the content in the request to DLP for blocking data-in-motion and preventing sensitive content from being committed.
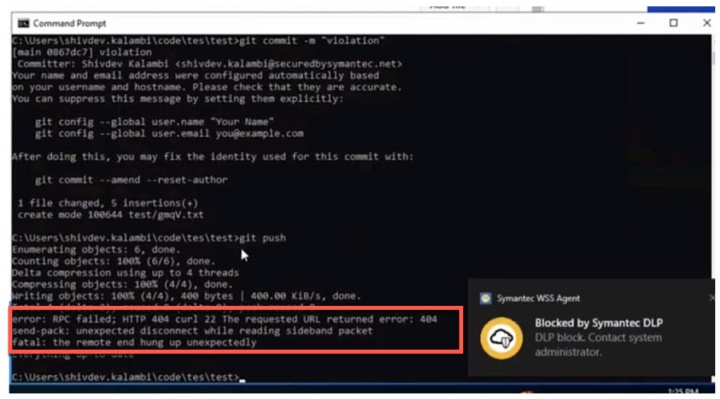
Threat Protection
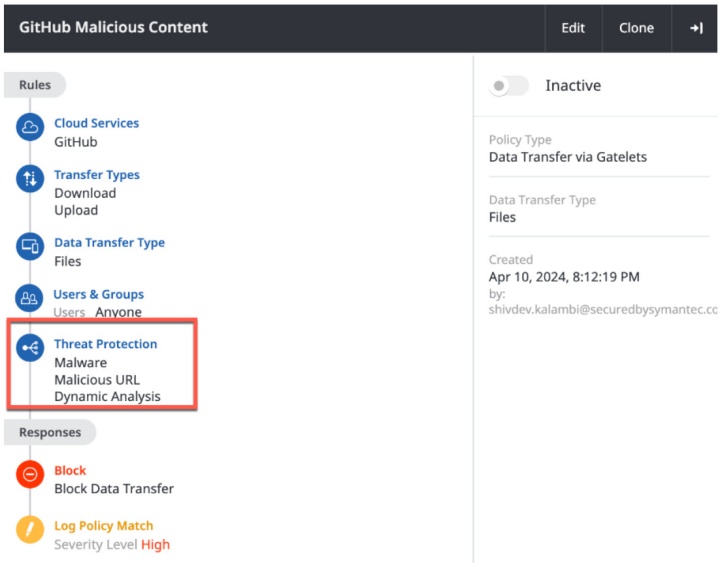
How do I stop malware infection from GitHub?
It is reported that there are millions of malicious repositories flooding GitHub. There is a real risk that developers (who tend to be inventive and very possibly sleep-deprived) will leverage a forked infected repository, thus making them vulnerable to an attack. Policies can be authored using the CASB Gateway, blocking downloads of any content containing malware, malicious URLs, etc. improving GitHub security posture. Specifically in this instance Dynamic Analysis from CASB Advanced Threat Protection can identify new and unknown malware via sandboxing/virtual execution of files.
Delivering ongoing best practices using Symantec DLP Cloud
Symantec DLP provides a number of important protections. To ensure your GitHub security posture is continually strong, we recommend that you:
- Periodically monitor GitHub Usage and Accounts/Repos in use using CloudSOC Audit
- Activate the CASB GitHub Securlet for deeper insights into Activities performed
- Define what’s sensitive and set up DLP policies to get notified. Review this at least annually (best practice is via a data governance board that meets monthly).
- Use the CASB GitHub Gatelet to:
- Block malware and malicious URL upload/downloads via CLI and Browser
- Block access to unsanctioned repositories or from unauthorized methods or users
- Block sensitive content from being uploaded via CLI and Browser

How to Make the Most of Symantec CloudSOC CASB
What the Experts* Advise








We encourage you to share your thoughts on your favorite social platform.