Sodinokibi: Ransomware Attackers also Scanning for PoS Software, Leveraging Cobalt Strike
Organizations in the healthcare, services, and food sectors among victims.
Researchers at Symantec, a division of Broadcom (NASDAQ: AVGO), have spotted a Sodinokibi targeted ransomware campaign in which the attackers are also scanning the networks of some victims for credit card or point of sale (PoS) software.
It is not clear if the attackers are targeting this software for encryption or because they want to scrape this information as a way to make even more money from this attack.
The attackers are using the Cobalt Strike commodity malware to deliver the Sodinokibi targeted ransomware to victims. Eight organizations had the Cobalt Strike commodity malware on their systems, with three of the victims subsequently infected with the Sodinokibi ransomware. The victims infected with Sodinokibi were in the services, food, and healthcare sectors. The companies targeted in this campaign were primarily large, even multinational, companies, which were likely targeted because the attackers believed they would be willing to pay a large ransom to recover access to their systems.
The attackers are aiming to make a lot of money - for victims infected with Sodinokibi the ransom requested is $50,000 in the Monero cryptocurrency if paid within the first three hours, and $100,000 after that.
Tactics, tools, and procedures
The attackers leverage legitimate tools in these attacks, and at one point we observed a legitimate remote admin client tool by NetSupport Ltd being used to install components during these attacks. In April, Symantec threat researchers found evidence of Sodinokibi attackers using similar tactics, when they spotted them using a copy of the AnyDesk remote access tool to deliver malware and other tools in at least two attacks.
The attackers in this campaign also use ‘legitimate’ infrastructure to store their payload and for their command and control (C&C) server. The attackers are using code-hosting service Pastebin to host their payload (the Cobalt Strike malware and Sodinokibi) and are using Amazon’s CloudFront service for their C&C infrastructure, to communicate with victim machines.
Pastebin and CloudFront are both legitimate services but have been observed being exploited by bad actors for similar malicious activity in the past. The advantage for malicious actors of using legitimate services to host payloads and for their C&C infrastructure is that traffic to and from a legitimate service is more likely to blend in with an organization’s legitimate traffic, and so is less likely to be flagged as suspicious and blocked.
Cobalt Strike is an off-the-shelf tool that can be used to load shellcode onto victim machines; it has legitimate uses as a penetration testing tool but is frequently exploited by malicious actors. The tactics used in this series of attacks are similar to tactics seen used in other targeted ransomware attacks before. Microsoft released research in April into attacks by six ransomware gangs, including Sodinokibi, and said that many of the groups employ similar tactics. The vector for most attacks observed by Microsoft was either the exploitation of vulnerable network devices or brute-force attacks on Remote Desktop Protocol (RDP) servers, and initial intrusion was followed by the use of living-off-the-land and commodity tools to perform credential theft and lateral movement before deploying the ransomware payload on multiple computers. So the tactics employed in this attack campaign are tactics commonly used by targeted ransomware gangs.
Once on a network, the attackers take various steps to reduce the chance they will be detected and to increase the chances of their attack working. The attackers attempt to disable any security software on the machine so their activity can’t be detected. They also enable remote desktop connections so they can use them to launch malicious commands.
The attackers also appear to be interested in stealing credentials on victim machines, and are observed adding user accounts, presumably in an attempt to maintain persistence on victim machines and also in a further attempt to keep a low profile on victim networks.
We see the attackers using encoded PowerShell commands in some of these attacks. PowerShell is a Windows command line tool that has many legitimate purposes but is also frequently abused for nefarious purposes by malicious actors using living-off-the-land tactics.
We see the Sodinokibi ransomware deployed on three of the victims that were infected with Cobalt Strike.
Sodinokibi
Sodinokibi is a targeted ransomware - we saw targeted ransomware attacks increase by 62 percent in 2019, and targeted ransomware is one of the biggest threats on the cyber security landscape currently.
Sodinokibi (aka REvil) first appeared in April 2019, but the actors behind it are widely believed to be the same actors who operated the GandCrab ransomware. GandCrab was a highly active targeted ransomware that first appeared in 2018. However, in June 2019 its operators announced that they were ‘retiring’, claiming that they had made more than $2 billion from the ransomware. However, it’s widely thought that they simply turned their focus to the Sodinokibi ransomware instead.
Sodinokibi was originally believed to be operated by one group but it is now thought to operate as a ransomware-as-a-service (RaaS), where one group maintains the code and rents it out to other groups, known as affiliates, who carry out attacks and spread the ransomware. Any profits made are then split between the affiliates and the original gang.
Since it appeared on the scene, Sodinokibi has been one of the most prolific targeted ransomware strains and has been seen in numerous high-profile incidents. Actors using Sodinokibi were apparently responsible for the hack of foreign exchange service Travelex on New Year’s Eve. The attack left the company offline for almost a month and caused huge disruption to its business, according to public reports. The attackers were said to have demanded a ransom of $6 million in that incident, with Travelex reportedly eventually paying $2.3 million to regain access to its systems. In January, it was reported that Sodinokibi’s average ransom demand was $260,000, so this was a huge ransom.
Sodinokibi hit several other high-profile companies in the last year and, similar to the Maze ransomware group, announced in December 2019 that it would release data stolen from victims if its ransom demands weren’t met. Since that announcement, the gang has been observed offering the data of victims for sale on hacking forums, and at the beginning of June an auction site was launched where the group said it will sell off stolen data to the highest bidder.
Victims
The three victims that were infected with Sodinokibi in this campaign were in the services, food, and healthcare sectors. The food and the services companies that were infected were both large, multi-site organizations that were likely capable of paying a large ransom - the type of company that would typically be targeted with Sodinokibi. However, the healthcare organization appears to have been a smaller operation. Interestingly, this victim’s systems were also scanned by the attackers for PoS software. It may be that the attackers realized this business might not be in a position to pay the large ransoms usually demanded in a Sodinokibi attack, and so scanned for PoS software to determine if they could profit from the compromise in another way, or they may have been scanning for this kind of software simply to encrypt it too.
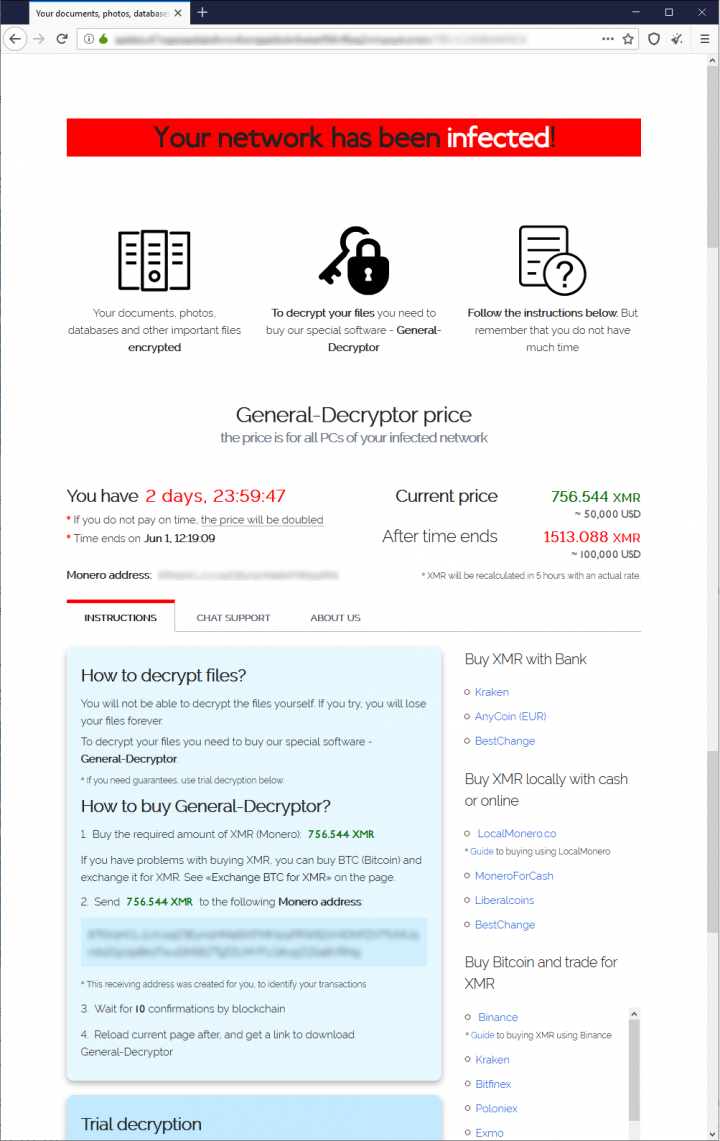
The attackers requested that the ransom be paid in the Monero cryptocurrency, which is favored for its privacy as, unlike Bitcoin, you cannot necessarily track transactions. For this reason we do not know if any of the victims paid the ransom, which was $50,000 if paid in the first three hours, rising to $100,000 after that time.
Conclusion
While many of the elements of this attack are ‘typical’ tactics seen in previous attacks using Sodinokibi, the scanning of victim systems for PoS software is interesting, as this is not typically something you see happening alongside targeted ransomware attacks. It will be interesting to see if this was just opportunistic activity in this campaign, or if it is set to be a new tactic adopted by targeted ransomware gangs.
One thing that is clear is the actors using Sodinokibi are sophisticated and skilled and show no sign that their activity is likely to decrease anytime soon. The companies targeted with this ransomware tend to be large corporate organizations, so companies like this need to be aware of the threat posed by this kind of activity.
Endpoint Protection
Ransom.Sodinokibi
Trojan.Agentemis (aka Cobalt Strike)
Indicators of Compromise (IoCs)
| Indicators of Compromise (IoCs) |
|---|
| 2d22d812117ff4ca4d8bcbd45ec20c77f52e907bf7320d44f6a4fd6c7beb066e |
| 362fc55f5cd3d5338827de0eafdb7eb34c26885345706852184db95ad9996a5c |
| 462257012d62ead365af0198457c64cc07a0597461ce79496c0f22b91273dcde |
| 982f8e3329ef811bde84fd0cd5009dbfda6ed5e22e10eea796ac128e787f4f50 |
| d41fd38a8478bf788f5dc0acf0e070dd360ddc9bfff0804e6b5254cc0116aa81 |
| 102.129.224.148 |
| 23.81.143.21 |
| 5.101.0.202 |
| d2zblloliromfu.cloudfront.net |
| https://pastebin.com/raw/09FvgM1g |
| https://pastebin.com/raw/4DhjNfkK |
| https://pastebin.com/raw/kehkNbH6 |
| https://pastebin.com/raw/Q9FdzgH2 |
| https://pastebin.com/raw/QtwtkUR0 |








We encourage you to share your thoughts on your favorite social platform.