Formjacking: Major Increase in Attacks on Online Retailers
Symantec has blocked almost a quarter of a million instances of attempted formjacking since mid-August.
Symantec has seen a major uptick in formjacking attacks recently, with publicly reported attacks on the websites of companies including Ticketmaster, British Airways, Feedify, and Newegg by a group called Magecart being the most notable examples.
Formjacking is a term we use to describe the use of malicious JavaScript code to steal credit card details and other information from payment forms on the checkout web pages of e-commerce sites. Formjacking is not a new technique, but recent campaigns are interesting as they are large, sophisticated, and have increased dramatically since mid-August 2018.
Symantec’s Intrusions Prevention System (IPS) technology proactively protects website users from formjacking attacks.
How does formjacking work?
When a customer of an e-commerce site clicks “submit” or its equivalent after entering their details into a website’s payment form, malicious JavaScript code that has been injected there by the cyber criminals collects all entered information, such as payment card details and the user’s name and address. This information is then sent to the attacker’s servers. Attackers can then use this information to perform payment card fraud or sell these details to other criminals on the dark web.
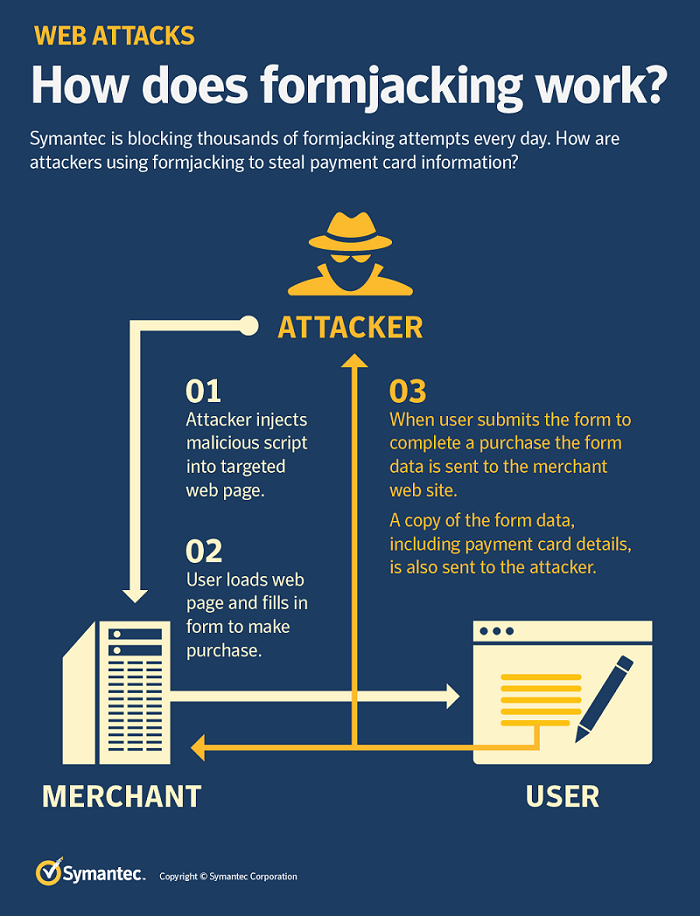
How big is this campaign?
This is a significant and sustained campaign, with activity increasing substantially in the week of September 13 to 20.
According to Symantec telemetry, since August 13 we have blocked 248,000 attempts at formjacking—almost a quarter of a million instances. However, more than one third of those blocks (36 percent) occurred from September 13 to 20, indicating that this activity is increasing.
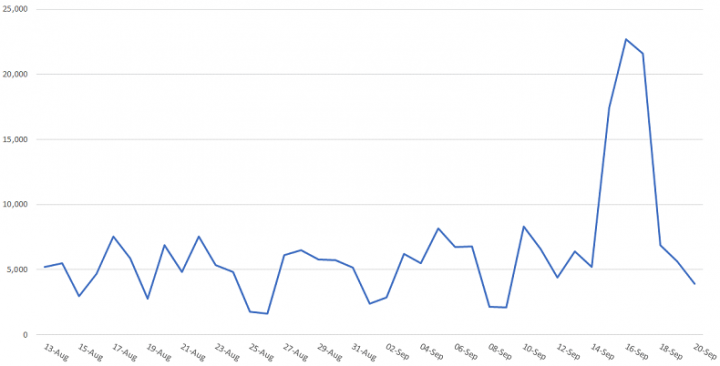
If we compare the week of September 13 to 20 to the same week in August, the number of instances of formjacking blocked by Symantec more than doubled, jumping from just over 41,000 to almost 88,500—a percentage increase of 117 percent.
Since August 13, we have blocked an average of 6,368 formjacking attempts every day.
Our data shows that any company, anywhere in the world, which processes payments online is a potential victim of formjacking
What types of businesses are these attacks targeting?
As we can see from the publicly reported attacks, Magecart is targeting large e-commerce businesses like Ticketmaster, British Airways, and Newegg.
To get an insight into the type of businesses that are being targeted by formjacking attacks, we examined 1,000 instances of formjacking blocked by Symantec over a three-day period from September 18 to 20.
Symantec data showed that from these 1,000 instances 57 individual websites were impacted. These websites were mostly online retail sites ranging from small niche sites to larger retail operations. Websites affected ranged from a fashion retailer in Australia, to a supplier of outdoor accessories in France, and a fitness retailer in Italy. Other retailers affected included a supplier of parts for cars and sites selling kitchen accessories and customized gifts.
While the compromise of larger organizations such as British Airways and Ticketmaster makes headlines, our data shows that any company, anywhere in the world, which processes payments online is a potential victim of formjacking.
Who is Magecart?
Magecart is the attack group behind the recent formjacking attacks on British Airways, Ticketmaster, Feedify, and Newegg. Magecart has been active since at least 2015. The group injects web-based card skimmers onto websites to steal payment card data and other sensitive information from online payment forms.
The group used to primarily focus on hacking into Magneto online stores, but it appears to have changed tactics recently, and we now see it using formjacking and supply chain compromise to steal payment card data.
How are websites being compromised?
There are many ways attackers can attempt to compromise websites, but in the Ticketmaster formjacking case the Magecart attackers used a supply chain attack to gain access to the website and change the code on its payment page.
We wrote about supply chain attacks in ISTR 23 and predicted we would continue to see them occurring frequently in 2018—and we have. Supply chain attacks can allow attackers to gain access to large companies by exploiting weaknesses in smaller businesses used by the larger company to provide different services. The famous Petya/NotPetya campaign, for example, was distributed via a supply chain attack. Supply chain attacks are particularly challenging because it doesn’t matter how good your business’ cyber security is if other businesses with access to your network can be exploited by attackers.
The uptick in formjacking attacks came to wider notice following the Ticketmaster breach, which was reported in June. The Magecart attackers injected malicious JavaScript code onto Ticketmaster’s website after they compromised a chatbot from tech firm Inbenta that was used for customer support on Ticketmaster websites. Magecart was then able to alter the JavaScript code on Ticketmaster’s websites to capture payment card data from customers and send it to their servers. The code may have been on the Ticketmaster website for almost a year, with international Ticketmaster customers warned they may have been affected if they bought tickets between September 2017 and June 2018. Inbenta said Magecart had exploited a number of vulnerabilities to target its front-end servers and alter the chatbot code.
Following the Ticketmaster breach it was revealed that Magecart was widely targeting third-party companies that are used on e-commerce sites to manage analytics, website support, and other services. The report at that time said at least 800 e-commerce sites had been hit in that campaign. The danger is that if Magecart can compromise one widely used third-party supplier, they could potentially infect thousands of sites in one go.
Feedify is one such third-party service that is used by many websites to serve up push notifications to website visitors. It was notified by a threat researcher on September 11 that some of its JavaScript code had been modified with the Magecart script, which prompted Feedify to delete the code. However, within 24 hours the code had been modified again, Feedify again deleted it but it once again reappeared, with threat researchers subsequently warning users of Feedify to stop using it until the issue was resolved.
Magecart’s attack on British Airways—which the airline said impacted 380,000 passengers—was, along with Ticketmaster, its most high-profile attack so far. In the attacks on both British Airways and U.S. electronics retailer Newegg, the Magecart attackers took steps to avoid detection, including setting up spoofed web domains designed to look like those of the legitimate company. They even purchased paid SSL certificates from Comodo to make them look more like legitimate servers.
British Airways and Newegg were both compromised in a similar manner, with a small amount of JavaScript code added to a page on the companies’ websites to allow entered payment information to be sent to the Magecart attackers’ servers via the spoofed domains. The attacks took place in a similar timeframe, with Magecart present on British Airway’s website from August 21 to September 5, and Newegg’s website from August 14 to September 18.
In the cases of both British Airways and Newegg the initial infection vector that allowed the attackers to gain access to the websites is not known.
Protection
Victims may not realize they are victims of formjacking as generally their websites continue to operate as normal, and attackers like Magecart are sophisticated and stealthy and take steps to avoid detection.
Symantec customers are protected from formjacking attacks.
Network-based protection
- Web Attack: Mass Injection Website 19
- Web Attack: Mass Injection Website 62
- Web Attack: Mass Injection Website 63
File-based protection
Website owners should also be aware of the dangers of software supply chain attacks, as these have been used as the infection vector in some of these formjacking attacks. Software supply chain attacks can be difficult to guard against, but there are some steps that website owners can take:
- Test new updates, even seemingly legitimate ones, in small test environments or sandboxes first, to detect any suspicious behavior.
- Behavior monitoring of all activity on a system can also help identify any unwanted patterns and allow you to block a suspicious application before any damage can be done.
Producers of software packages should ensure that they are able to detect unwanted changes in the software update process and on their website.
Website owners can also use content security policies with Subresource Integrity tags (SRI) to lock down any integrated third-party script.







We encourage you to share your thoughts on your favorite social platform.