Android Malware Steals Uber Credentials and Covers Up the Heist Using Deep Links
The latest Android.Fakeapp variant steals user credentials then uses deep links of the legitimate Uber app to hide the fact.
While analyzing the most recent Android.Fakeapp malware variants, we came across a sample that was using a quite novel and different monetization technique, in addition to the regular overlay tricks asking users to enter their credit card details. This one would be of particular concern to Uber users on Android, which number in the millions worldwide.
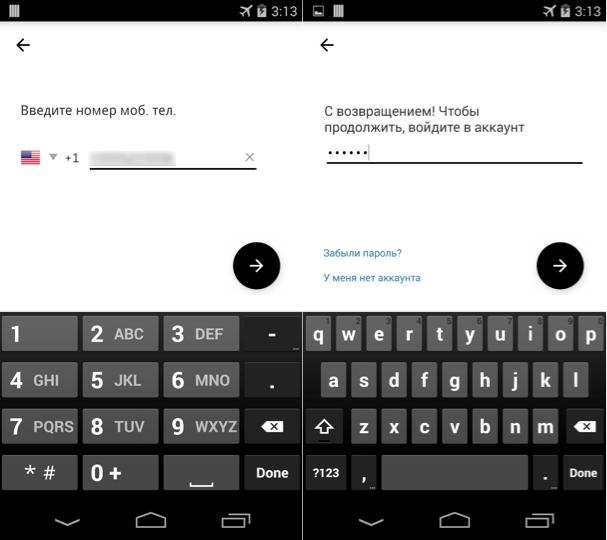
The Fakeapp variant we found had a spoofed Uber application user interface (UI) which pops up on the user’s device screen in regular intervals until the user gets tricked into entering their Uber ID (typically the registered phone number) and password.
Figure 1 shows the fake Uber app UI displayed by the malware to get the user to enter their details. Once the user clicks the Next button (->), the malware sends the user ID and password to its remote server.
Next, the malware tries to cover up the heist. To avoid alarming the user, the malware displays a screen of the legitimate app that shows the user’s current location, which would not normally arouse suspicion because that’s what’s expected of the actual app.
This is where creators of this Fakeapp variant got creative. To show the said screen, the malware uses the deep link URI of the legitimate app that starts the app’s Ride Request activity, with the current location of the victim preloaded as the pickup point.
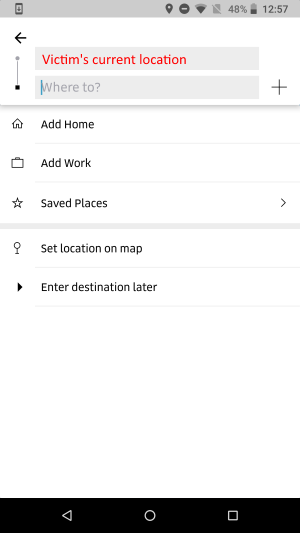
To show the said screen, the malware uses the deep link URI of the legitimate app that starts the app’s Ride Request activity, with the current location of the victim preloaded as the pickup point.
Deep links are URLs that take users directly to specific content in an app. Deep linking in Android is a way to identify a specific piece of content or functionality inside an app. It is much like a web URL, but for applications. For example, the Uber app has the following deep link URI for its Ride Request activity:
- uber://?action=setPickup&pickup=my_location
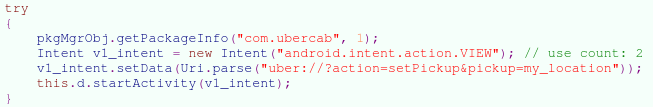
Figure 3 illustrates the code snippet of the malware that fires the VIEW intent with the Ride Request deep link URI after exfiltrating the Uber credentials to its remote server.
This case again demonstrates malware authors’ neverending quest for finding new social engineering techniques to trick and steal from unwitting users.
Mitigation
Symantec recommends users follow these best practices to stay protected from mobile threats:
- Keep your software up to date
- Refrain from downloading apps from unfamiliar sites and only install apps from trusted sources
- Pay close attention to the permissions requested by apps
- Install a suitable mobile security app, such as Norton, to protect your device and data
- Make frequent backups of important data
Protection
Symantec and Norton products detect the threat discussed in this blog as Android.Fakeapp.







We encourage you to share your thoughts on your favorite social platform.