Zero Trust Network Access: A cornerstone for Data-Centric SASE
Symantec Secure Access Cloud helps ensure your SASE journey is guided by Zero Trust principles
The Revolution in Network Security is Here
At Symantec, as a division of Broadcom, we see and hear from our customers that it is a revolution that is completely turning the current network perimeter focused security model inside-out. As opposed to the traditional, network-centric IT architecture, it envisions a new, application-centric architecture. According to a PwC survey, “83% of employers now say the shift to remote work has been successful for their company.” But with this new security paradigm there is now more data from users, the cloud, digital devices, and edge architectures outside the enterprise data center than within. It is a revolution based on the philosophy of Zero Trust and its principles of least privilege and implicit trust of no one or nothing.
This new vision was converted into the architecture which was suggested by Gartner and is called Secure Access Service Edge (SASE), and more specifically, Data-Centric, hybrid SASE. That is, SASE that enforces least-privilege access, data governance and strong data security, regardless of by leveraging Zero Trust model. It offers a new and comprehensive architecture for reimagining and reinventing network security.
Zero Trust Network Access
Adopting Zero Trust Network Access (ZTNA) is the newest phase of this on-going revolution in network security. It is one of the critical components of the SASE architecture along with Data Loss Prevention (DLP), Secure Web Gateway (SWG) and Cloud Access Security Broker (CASB).
ZTNA directly addresses the reality that the new boundary of network security is a borderless, software-defined perimeter (SDP) that embraces and extends around every digital device and user, application and service - running across the network from on-premises to cloud to edge.
Adopting Zero Trust Network Access (ZTNA) is the newest phase of this on-going revolution in network security.
ZTNA solutions, such as Symantec Secure Access Cloud, provide an alternative security model that removes the need to backhaul traffic between remote users and the core network’s data center. Compared to the network based solutions, it provides a greater level of security through cloaking the organization’s workloads from the internet as well as continued authorization of the user’s access to specific applications.
This expanded capability allows ZTNA to provide continuous access and governance for users to the applications they need to use on the device of their choice. While at the same time preventing lateral movement inside the data center to applications and data to which the users are not verified.
Cornerstone for Data-Centric, Hybrid-Capable SASE
ZTNA offers a new network security model that reflects the reality of the modern enterprise network and its migration to the cloud. As a solution designed for a software-defined and cloud-based networking universe, ZTNA offers far more security and onboarding & maintenance simplicity for the modern enterprise than most legacy-based network products.
The advantages of ZTNA versus legacy-based network products include:
- Lower operational costs with easy maintenance and onboarding
- Granular access and governance for BYOD
- Streamlined user experience (no agent needed)
- Higher security
- Better performance
Most important, however, is the fact that ZTNA is not a stand-alone product in the traditional sense. But rather, ZTNA should be considered as a cornerstone for building the enterprise Data-Centric, Hybrid SASE architecture.
Stronger Data Protection for Unmanaged Devices
Among the many benefits of Symantec ZTNA solutions - Symantec Secure Access Cloud, is that it removes the limitations on deployment modes for those organizations which use agent-based deployments to enforce security.
Agent-based deployments negatively impact the user experience (UX) and enterprise security when users switch their devices while working remotely as well as change their roles or assume new positions.
A good example, is how agent-based deployments affect the security for unmanaged devices. With much of the enterprise working from home (WFH), the requirements for a secure workforce have changed. According to the survey mentioned earlier, more than 60 percent of enterprises are planning to consolidate and significantly reduce their current office spaces. It’s easy to see why as the same survey reveals that more than 80 percent report that the shift to remote work has been successful for their companies.
The number of people using unmanaged devices to WFH severely challenges agent-based security administration. Deploying and upgrading agents in response to every new device is both time-consuming and creating strains on IT security budgets. For users, the situation is just as bad. Until their agent-based solution is upgraded, they are prevented from working the way they prefer or normally would do as they are prevented from accessing sensitive data on their unmanaged devices or experience “overblocking.” (Overblocking crops up when access security solutions have a default filter mode which deny legitimate access to the network because the blocking is too broad and inflexible to discriminate more precisely.)
Secure Access Cloud users have the same ease of use and experience on their unmanaged devices as they enjoy on their managed devices.
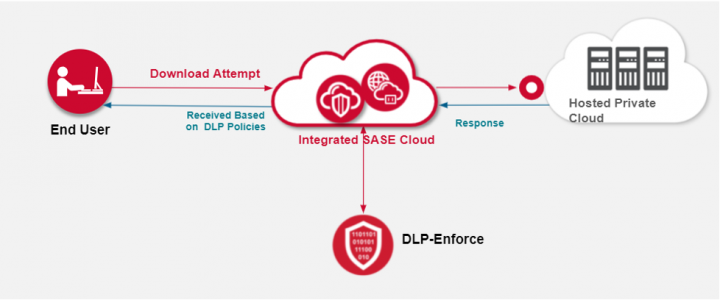
Secure Access Cloud, when integrated with an enterprise DLP solution completely changes this scenario. It allows access to corporate assets from unmanaged devices but also specific downloads or uploads of sensitive private information, leveraging the existing DLP policies. For example, the user might be able to download some “non sensitive” data using his unmanaged devices, while being restricted to online editing on a different file. This file may include personally identifiable information (PII), protected health information (PHI) or any type of sensitive data as classified by DLP. Secure Access Cloud users have the same ease of use and experience on their unmanaged devices as they enjoy on their managed devices.
The IT security team also has far more granular visibility into user requests for access. They can set policies that provide greater security by implementing a data-centric least-privileged model, while allowing or preventing explicit actions or access to specific URIs within the applications themselves, without having to resort to over-blocking the access or restricting user access to their unmanaged devices.
This single-pass solution delivers the same native UX for all remote access scenarios, without compromising data security and supporting a customer’s digital transformation. This puts Symantec Secure Access Cloud at the forefront of ZTNA solutions and a key capability for data-centric SASE.









We encourage you to share your thoughts on your favorite social platform.