Symantec Mobile Threat Defense: Leveraging MTD to Protect Against Hacked Routers
New technology protects mobile users from DNS hijacking attacks and gives greater visibility into what’s happening on your network router
Researchers at Symantec recently spotted an interesting mobile security affecting one of our customers. While trying to access the Banco do Brasil website on his phone, an employee was redirected to a different IP address, arriving at a fake website that looked exactly like the legitimate site operated by the Brazilian bank.
Our system found that the network connection through which the employee tried to access the Banco do Brasil website was subject to “suspicious domain name system (DNS) resolutions.” This indicates that DNS server settings were modified. Attackers generally change DNS settings to spy on victims’ communications, intercept their traffic, and redirect them to different destinations. In this particular DNS server incident, it appeared someone had changed the default DNS server into a “rogue” server in an attempt to intercept employee traffic and send them to cloned, fake phishing sites.
Sound familiar? It should.
The incident is likely part of a wider malware campaign that targeted Brazilian bank websites just a few months earlier. In October 2018, security experts reported increased activity of a malicious agent trying to modify the DNS server settings in the home routers of thousands of Brazilian residents. The DNS hijacking campaign – dubbed GhostDNS – attempted to redirect victims’ DNS requests for certain websites, in particular Banco do Brasil, through a malicious DNS server. Instead of bringing victims to the legitimate sites, the malicious DNS server would take them to nearly-identical phishing websites where the attacker attempted to steal their personal credentials. More than 100,000 home routers have been hacked by GhostDNS to date, mostly in Brazil, with over 50 domain names, such as Netflix, Citibank.br, Itau Unibanco, and other Brazilian bank sites, said to have been targeted by the malware campaign.
It All Starts with Your Router
While we don’t know the extent of GhostDNS’s success, we know where the problem began – a place that is often overlooked when people think of Wi-Fi connection security: a router. Like in similar DNS hijacking campaigns (VPNFilter and DNSChanger to name a few), the attackers were able to get access to DNS server settings by hacking into vulnerable routers. This is done fairly easily. Publicly-known vulnerabilities, such as weak passwords and outdated firmware, can be exploited to remotely execute code and gain control of routers.
Once inside, hackers can override a router’s network DNS settings, leaving it vulnerable to a number of potentially harmful attacks and activities such as:
- Man-in-the-Middle attacks where a malicious third party can intercept communications and redirect users to malicious websites
- Phishing attacks in which a victim is tricked into entering personal information, such as usernames and credit card numbers, on forged websites that seem reputable by mimicking the appearance of real websites
- Spying on user behavior on the network (what sites they are visiting)
- Injecting fake content into insecure traffic, for example fake news on insecure news websites
- Malware attacks in which scam sites prompt users to download malware disguised as legitimate software
- Exploitation of browser vulnerabilities to gain remote code execution on mobile devices (victims are redirected to an attacker’s DNS that launches browser-based exploits to infect devices with malware)
Most of these attacks occur without the end-user having any idea something is wrong. Furthermore, even after a mobile device has disconnected from the infected router network, attackers can continue to control a compromised device if it has been infected with malware, as in the last two examples above.
What You Can Do About DNS Hijacking
DNS hijacking is a not a new phenomenon and we’ve seen increased efforts to prevent attacks or mitigate their impact in recent years. One solution more website operators are turning to is the adoption of a web security mechanism known as HTTP Strict Transport Security (HSTS). Browsers with an HSTS policy refuse to load a website if it is served over an unencrypted connection (HTTP), what DNS hijackers attempt to do. However, it’s not impossible for attackers to circumvent this security mechanism by installing valid domain name certificates on their malicious DNS servers. There have been instances where attackers have managed to access fraudulent certificates, enabling them to make phishing websites appear to be secured with valid HTTPS encryption.
As in our Banco do Brasil example above, mobile users may not notice - or even be able - to recognize if a website they are accessing is a phishing site. The good news is that with SEP Mobile’s protection against untrusted DNS servers, they don’t have to know. SEP Mobile, Symantec’s Mobile Threat Defense (MTD) solution, ensures users are safeguarded from DNS hijacking threats in all scenarios: where web security mechanisms such as HSTS exist, where HSTS can be bypassed by attackers, and where no security mechanisms exist at all. Organizations can be confident that whatever network threats their employees are exposed to, they are automatically protected.
SEP Mobile detects network threats such as unwanted DNS servers by analyzing all the different network connections mobile devices encounter. We look at the data to find suspicious anomalies using: 1.) Symantec’s Global Intelligence Network, one of the largest crowdsourced threat intelligence networks in the world; 2.) Reputation services that collect information and categorize websites according to security risk; and 3.) our patented Active Honeypot technology which thoroughly analyzes network connections end-to-end to keep communications safe.
How to Protect against Network-based Attacks
As the first mobile threat defense (MTD) solution to offer protection against suspicious DNS servers, SEP Mobile not only safeguards organizations and their employees from DNS hijacking attacks, but it also extends their security visibility beyond the mobile device itself. As mentioned before, because one of the most common ways attackers can modify a network’s DNS server is by hacking into the router, when suspicious DNS resolutions are detected on the network, this is often a sign of a compromised router.
In practice, if SEP Mobile detects a network attack like DNS hijacking, two simultaneous things happen. First, our automated network protection actions kick in, such as: tunneling traffic from the mobile device through a secure VPN connection or blocking the mobile device from accessing sensitive corporate resources (email, work applications, etc). Second, both enterprise security admins and end-users receive alerts on the threat, with the alert suggesting that the network router may have been compromised due to suspicious domain name resolutions.
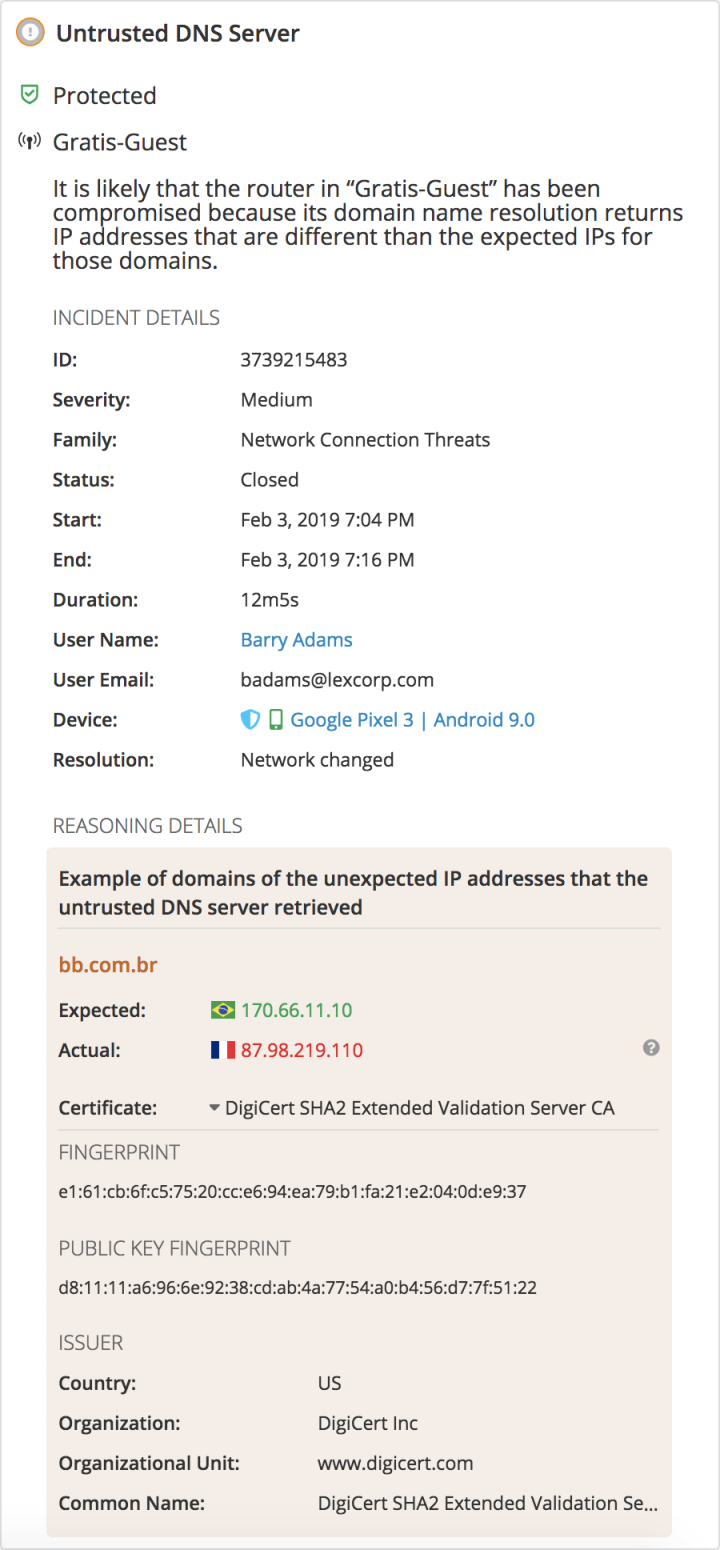
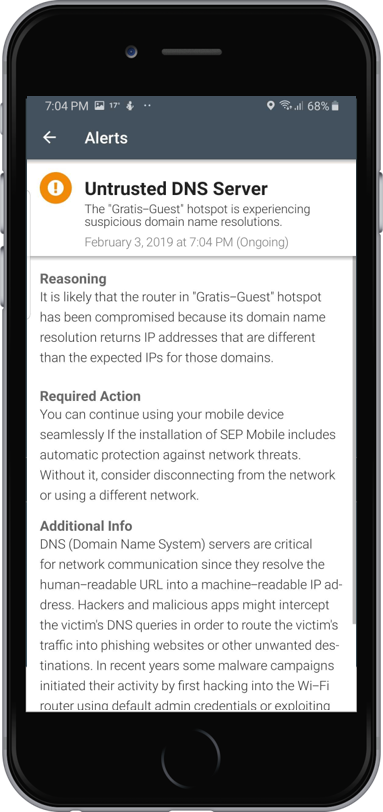
Both our protection actions and alerts can be configured in accordance with an organization’s security policy.
With mobile devices connecting to several more networks (and connecting more often) than traditional endpoints, network-based mobile attacks pose a significant security risk to organizations today. This risk, combined with the rising sophistication of attacks, and their ever-increasing ability to tap into sensitive corporate data, underscore the need for MTD solutions that provide robust protection.
Our Banco do Brasil incident had a happy ending: the end-user’s mobile device and personal data, as well as the organization’s corporate resources, were protected by SEP Mobile from falling into the wrong hands. Other organizations without advanced MTD capabilities (or without an MTD at all) may not be so lucky.

Debunking the Benefits of Zero-Touch Activation
An additional 20 seconds of user interaction can save your organization from being the victim of a mobile security breach









We encourage you to share your thoughts on your favorite social platform.