Symantec: Helping to Protect Your Mobile Devices
Security is important now more than ever
We are definitely in strange times. What was once a world of face to face interactions: meeting in person with customers, grabbing my laptop and booting up with a brisk 64GB of memory, have now turned into virtual interactions due to COVID. What this virtual environment has also enabled, is that the bad guys are getting smarter and leveraging mobile technology to further their own malicious activities and agendas such as harvesting credentials, or tricking people into giving up their personal information. This makes it is especially important for enterprises today to be vigilant, as the remote working environment extends more to mobile devices.
With this increase, comes the need to ensure you have a solid Mobile Threat Defense (MTD) solution in your mobile environment.
Symantec, a division of Broadcom (NASDAQ: AVGO), is seeing attackers using mobile as a delivery method for malware, with one area being Smishing (or Phishing via SMS). This is where the attacker sends a text, sometimes “catered” to the recipient with a little social engineering, which contains a URL/Link to a malicious or suspicious website. The same method can be used in “QR” Quick Response codes sometimes referred to as Qrishing, it’s just a different delivery method. The reason this is important is because we now live in a world where we grab our phones before anything else, we are constantly connected to our jobs and personal lives: meaning email, banking, healthcare, or any applications and information on that device can potentially be at risk.
Symantec Researcher, Kevin Watkins, wrote an article in May about the increase in SMS phishing that attackers were taking advantage of due to COVID. With this increase, comes the need to ensure you have a solid Mobile Threat Defense (MTD) solution in your mobile environment. This is not a “Nice to Have”, this is a must, and without protecting your mobile devices, you are leaving one of the most targeted platforms we see today vulnerable to attacks.
What Should You Do?
- Ensure you have both MDM (Mobile Device Management) and MTD (Mobile Threat Defense). On occasion I’ll speak with a customer that only has MDM, and MDM alone will not protect you against advanced attacks such as malicious or risky apps, or network based threats.
- Leverage a MTD (Mobile Threat Defense). This provides “on device” resource detection and protection to block access to corporate resources when that device presents a risk. If your end users device becomes compromised or has a high risk score, do you want that device accessing corporate email or any SaaS based application?
- Ensure you are protected against network based attacks based attacks (Man In The Middle/SSL Stripping). This is extremely important as most any Wi-Fi SSID (Service Set Identifier) can be duplicated, and mobile devices (without folks even knowing it’s happening) can inadvertently be routing all their traffic through the attacker’s hardware.
- Ensure you have full visibility into device health, incidents, suspicious urls, installed apps, and a full risk analysis on those apps. Do you know the risk associated with the apps installed on your devices? Are any of those apps violating any corporate policy, AUP (Acceptable Use Policy), or putting the device and end user at risk?
Symantec acquired Skycure in 2017, and integrated their tools and technologies into Symantec Endpoint Mobile (SEP Mobile) that is now part of (SESE) Symantec Endpoint Security Enterprise. SESE is a robust product that integrates with the most prominent MDM providers (Mobile Device Management), with patented technology to help provide privacy of the end users device and data, while providing protection at the same time.
Symantec Intelligence Services
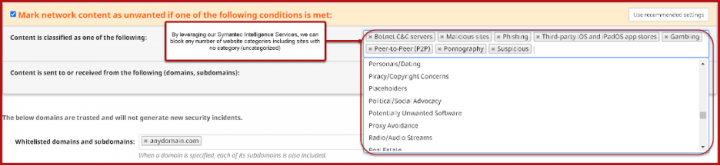
One specific technology to note is the Symantec Intelligence Services that we integrate with the SEP Mobile solution. Through protection actions the customer can fully define in the console, they can block and alert on any web traffic attempts to websites the customer might note as an AUP (Acceptable Use Policy) violation such as: Gambling, Malicious, Suspicious, or Proxy Avoidance just to name a few. Symantec Intelligence Services has well over 80 website categories and was integrated into SEP Mobile, making this one of the many added features that brings the power of website analysis, into the SEP Mobile product. This is just one example of the many different integrations we have including our WSS (Web Security Services/Cloud Proxy) solution, and our CASB solution.
Important Policies
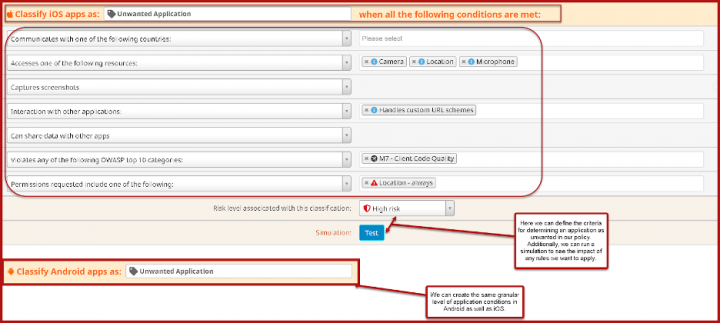
To add onto the protection stack in SEP Mobile, we also have a very powerful Unwanted Application policy which allows you to get as granular as you wish based on your security posture. By using this in tandem with our Protection Actions policy, this will allow you to block access to any Cloud based (SaaS) or internally hosted application.
Staying Secure
By leveraging SEP Mobile to protect your corporate or BYO (Bring Your Own) devices, you can ensure they will remain secure wherever they might be (in the office or remote). SEP Mobile is included in our endpoint security stack called Symantec Endpoint Security Enterprise (SESE), that protects all of the endpoints in your environment, including mobile devices, laptops, workstations, and servers. SEP Mobile is also included in our flagship offering Symantec Endpoint Security Complete (SESC) which builds on SESE and adds EDR, Active Directory Defense, Threat Hunting, Attack Surface Reduction, and other technologies for the most robust endpoint security offering in the market.
Examples:
This is an example of our integration with our Symantec Intelligence Services technology and how we can use this feature to block mobile device web traffic by category.
As seen below, you can define at a very granular level, the criteria for how to classify unwanted applications on mobile devices. This allows you to trigger protection actions based on the device risk posture.
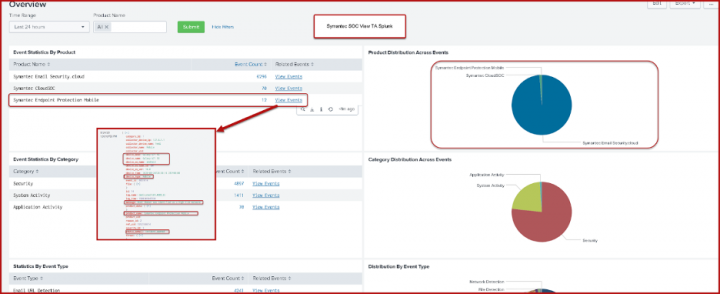
Using Symantec's ICDx (Integrated Cyber Defense Exchange), you can feed SEP Mobile incident data into any Security Operations Center (SOC) dashboard of your choice such as Kibana or Splunk (Symantec SOCView app for Splunk shown below). This data integration will help provide full visibility into incidents, and the ability to track trends and discover hidden issues in your enterprise.

SMS Phishing Campaigns Take Advantage of Coronavirus Pandemic
Symantec finds that 1 in 20 COVID-19 related SMS messages contain phishing attempts or other high-risk content.








We encourage you to share your thoughts on your favorite social platform.