Symantec Enterprise Can Help Secure Remote Workers From Brute Force Attacks
This is the most effective way to keep your Remote Desktop Protocol (RDP) application safe, especially in this current threat landscape
It goes without saying that COVID-19 has impacted how we live, how we socialize and how we work. It has changed the way employees access information and this transformation has created significant complexities for enterprises and has exposed major security vulnerabilities through the entire fabric of their architecture.
Since spring of this year, Bank Info Security reports the number of brute force attacks on RDP based resources multiplied itself twice across the world. (See image below) Those numbers shouldn’t come as a surprise given that during these unprecedented times, most companies across the globe have had to very quickly readjust their way of working, many employees now working remotely from home as a result of COVID-19.
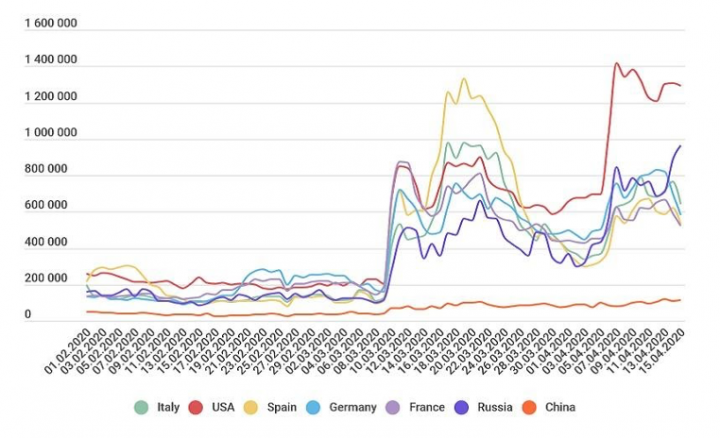
Disruptive technologies typically play a part in the reason why network security adjustments need to be made. It is part and parcel of change but usually we can see it in the distance, it’s a gradual evolving process. Contrary to this idea, COVID-19 snuck up on us, the virus has had to force organizations to rapidly shift how they work which has majorly impacted the threat landscape causing numerous malicious network attacks, namely Brute Force attacks.
Brute force attacks, in three dimensions
A Brute-force attack is pretty intuitive: the attacker intentionally has to try the whole set of possible combinations, until he finds the correct one. The options they can use include horizontal, vertical and diagonal attacks:
- Horizontal Attack: the attacker might try to compromise the accounts of multiple users across the organization
- Vertical Attack: the attacker can apply his whole power to compromise the one legitimate user
- Diagonal Attack: the most efficient attack is applying both horizontal and vertical methods, where attacker shifts both username and password at each try
Horizontal or Diagonal Brute Force attacks are much harder to detect, since the attackers can try one username/password pair at a time for a few times only. When the number of failed logins is low, it’s challenging to spot the attack for the alert systems.
Will that trivial method ever go out of fashion? No, I don’t believe it will, and for a very good reason, the successful rate of these kind of attacks is 1:1000 According to the Microsoft RDP brute-force attacks study, around 0.08% of RDP brute-force attacks are successful, and RDP brute-force attacks last 2-3 days on average.
How to keep the attackers at bay
Let’s delve into the ideal conditions that make brute force attacks possible, and why attackers consider them valuable.
- Exposure to the Internet
If any resource is exposed to the Internet, the attacker can access it and execute a brute-force attack. When resources are not exposed the attacker cannot reach the application as the surface attack is eliminated.- Advice: Get it off the Internet!
- Lateral Movement
Let’s say the attacker got lucky and was able to compromise one of your machines using RDP brute-force attack, or gained access to your corporate network using a convincing phishing lure. Nothing prevents them from trying the same method on other machines from within the organization- Advice: Use a Software Defined Perimeter (SDP) in order to avoid Lateral Movement.
- Absence of Two-Factor Authentication
Brute-force is essentially a large-scale game where attackers guess every possible password in a password space. A Second Factor of Authentication increases the strength of identity verification by adding an extra layer to your basic single-factor authentication (i.e., password). This method extremely complicates the brute-force attack approach and makes it difficult for hackers to break into online accounts.- Advice: Use a Second Factor of Authentication such as SMS, an authenticator app, a biometric or a physical key.
- True Auditing and Monitoring
It's critical to monitor the suspicious connections and unusual failed sign-ins that result in authenticated sign-in events, count the distinct username that failed to sign in without success, as well as count the inbound connections from one or more of the same IP address to the different RDP resources.- Advice: Monitor and audit your logs and alerts daily in order to detect RDP brute-force traffic patterns for your resources.
How to combat the rise of the attacks
Historically, the common set of basic recommendations for fighting a brute-force attack has been to always take a passive-defensive approach, like: using corporate VPN for reducing the chance for attacker to obtain access to the service as well as use Network Level Authentication (NLA). In this way the end users are installing/upgrading the agents and the “fighters” (administrators) are installing appliances and managing many tunnels and network policies ...and it still doesn't bring you the win.
As the attacker gains access to the private network using one of the VPN vulnerabilities , the attacks will come from inside, leaving you no chance to fight with it. It might also come from the unmanaged devices used by the end users as they work from home which may be already compromised while installing agents on them.
What is your solution?
Symantec’s Secure Access Cloud provides point-to-point connectivity at the application level, cloaking all resources from the end-user devices and the internet. It also suggests a set of MFA approaches, addressing the four mentioned points by design:
- Cloak corporate resources from the end users and the internet
The resources are not exposed to the Internet anymore, but through the Secure Access Cloud facade. - Second Factor Authentication capabilities
Built in second factor authentication for RDP resources and supports integration with 3rd party MFA providers such as Symantec VIP (which is integrated, free of charge part of the solution). - Allow only point-to-point application-level access
The network-level attack surface is entirely removed, leaving no room for lateral movement and network-based threats. - Providing Full visibility
Secure Access Cloud provides extremely granular logging and reporting of user activities. Every user access and device is authenticated and authorized before access is granted.
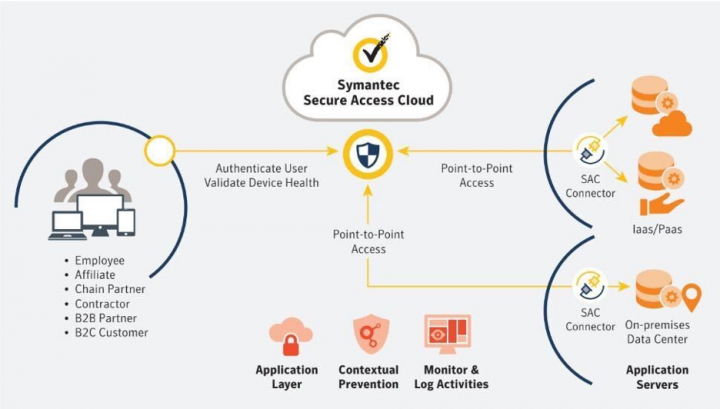
In short, Symantec’s Secure Access Cloud solution protects against all kinds of RDP server attacks. It enables more secure and granular access management to any corporate resource hosted on-premises or in the cloud.
Key Takeaways
- Leveraging an SDP solution, which adheres to the Zero Trust model, will allow secure, remote access from unmanaged devices while avoiding the lateral movement risk when allowing these devices into the corporate network.
- Implementing second factor authentication will reduce brute force impact and malicious access attempts.
- Infosec teams require full auditing and monitoring of the end users access: for detection, forensics, auditing and incident response.
- Avoid installing agents on the end user devices to keep the operation simple.
- Leverage Secure Access Cloud to enable your workforce to safely work from home.
Learn more about Symantec and Zero Trust: Here
Check out the product demo video below and understand how you can securely access your RDP hosted servers with Secure Access Cloud.










We encourage you to share your thoughts on your favorite social platform.