Symantec Content Analysis: Multi-layered Threat Protection
Offering more flexibility and scalability
Over the summer, when Symantec, a division of Broadcom (NASDAQ: AVGO), rolled out its new Secure Web Gateway (SWG) solution, it also announced the decoupling of hardware appliances into separate hardware and software components to offer more convenience to customers. In a follow-up move, Symantec Content Analysis (CAS) is similarly being decoupled to offer customers more purchasing flexibility and scalability.
Paired with Symantec ProxySG, Secure Messaging Gateway, Symantec Endpoint Protection, Security Analytics or other third-party tools, CAS offers customers a unique way to determine whether something is malicious and then prevents bad files from getting to an endpoint and causing damage.
I caught up with Mitch Merrifield, from Symantec’s Network Information Security team to learn more about the changes, including the simplification of the CAS licensing program.
Q: What are the terms of the new enterprise licensing that’s being announced?
A: Our new CAS enterprise licensing allows a customer to buy hardware and software separately. The licenses are based on the total processing capacity that customers need. That offers clear advantages when we think about flexibility, scalability, and cost savings. For example, you can now deploy using a single license, either on hardware in a virtual environment or even in the public cloud. And scaling becomes a lot easier since the customer will be able to add more capacity at any time to their license and deploy more based on the same license. Also, customers can resize their existing deployments. They can aggregate them all in one place. They can split up their instances. And so, any way that an organization needs to deploy Content Analysis, they can now do that with a single license.
Q: From now on, they won’t need to buy capacity before they need it?
A: Exactly. So, when it comes to disaster recovery, you won’t find licenses sitting idle; they can be purchased and spun up on demand.
Q: On the subject of licensing issues, what were you hearing from customers?
A: Two things. Hardware was being sold as a monolithic appliance. So once customers purchased capacity for that appliance, they held it for whatever their depreciation time was. There was limited flexibility; whether it accomplished what they needed in the next year or the year after that didn't matter. They just bought a big thing. The difference now is that when they buy hardware, they only need to install the software they need today and then add more capacity over time. They could even reduce capacity and save money on licensing if they find they won’t need that capacity in the future.
On the software side, they were buying a fixed license, but each time that they needed more, they had to buy a new license. Take an example: if they had 400 virtual Content Analysis instances, then they had 400 licenses. Now they have one license. And that license renews just once a year, instead of 400 renewals every year. So from an administrative point of view, it's just a lot easier. This simplifies procurement purchasing management, and deployment management.
Paired with Symantec ProxySG, Secure Messaging Gateway, Symantec Endpoint Protection, Security Analytics or other third-party tools, CAS offers customers a unique way to determine whether something is malicious and then prevents bad files from getting to an endpoint and causing damage.
Q: On a big picture level, why will customers find this a better approach to threat detection?
A: Simple, single layer defenses are no match for sophisticated attacks that can evade basic protections. SOC and IR teams are getting inundated with alerts. There’s just too many for them to handle effectively. Sandboxing can certainly provide some help in detecting unknown threats, but they are often slow and don’t offer real-time protection. If your threat intelligence is limited, so will your ability to detect a threat and some attacks may go undetected for extended periods. Security organizations invest heavily in a number of technologies. But if there is weak integration between tools, you are stuck with an entirely manual process and remediation is slow.
Q: So, what makes this a better approach to threat detection?
A: Content Analysis basically delivers what we call multi-layer file inspection, and the intention is to prevent unknown threats from getting into an organization. This happens by having sources like ProxySG and Secure Messaging Gateway and other tools that can send content to Content Analysis for deep inspection. We use a number of words, like interrogation and analysis and scanning, to basically determine whether specific content is malicious and should be blocked. The goal here is to work with various termination points to identify that content as far away from the endpoint as possible. When it works with the proxy, the idea is that we'll find it at the network level and determine that something is malicious and be able to prevent that file from causing malicious activity before it gets to the endpoint.
Q: On a day-to-day level, how would a multi-layered approach play out?
A: It would feature multiple types of scanning and analysis, so you’re better protected against targeted malware attacks, Trojans, and web spyware and the rest. Also, identifying malware using mobile techniques lets a SOC team prioritize and dramatically reduce the number alerts that it has to address. This is a big differentiator as the technologies that we have within Content Analysis and ProxySG can very quickly identify malicious things and help defenders rapidly make decisions. The upshot is that fewer things need to go to sandboxing.
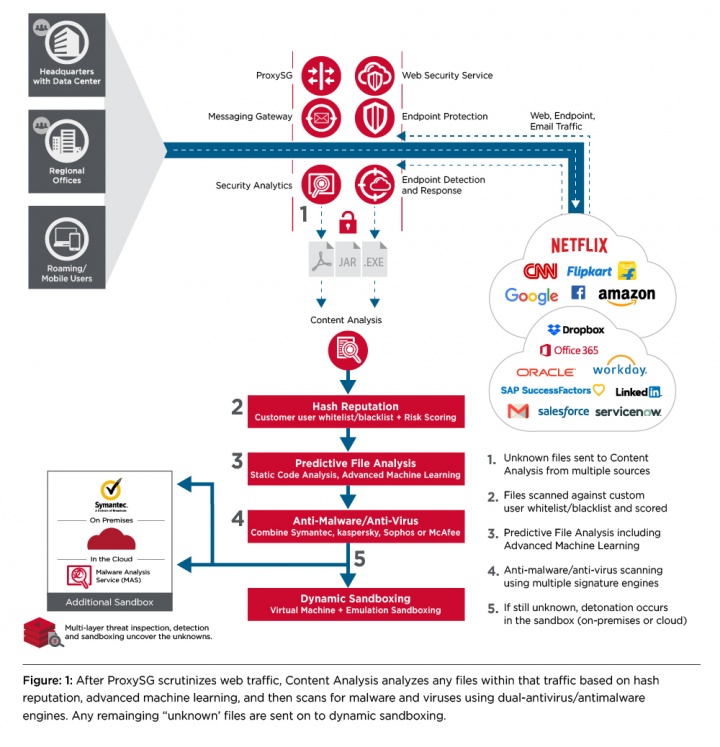
Q: How does this compare with other approaches used for threat detection?
A: Other organizations might use a more single layer, simple approach and say, `Well, that's good enough.’ Our approach features multiple layers that are more effective at finding malicious content. All those capabilities that have previously been on some kind of legacy hardware are now available on this new platform that we announced for ProxySG. It’s the same hardware platform; Content Analysis can sit side by side with ProxySG or by itself. It can also be deployed as a virtual appliance or in a customer’s cloud environment, all with the same license.
Q: What happens when the system determines that a file contains malicious content?
A: If something’s determined to be malicious, the system will basically communicate back to ProxySG which can then terminate the session. That’s the use case where Content Analysis is attached to ProxySG. At the same time, the content might have come from an endpoint where it could get inspected. The content might have come from Symantec Security Analytics where it could get inspected further. And the steps after detection in each case may be different.
Q: Can you offer an example of this type of threat protection in action?
A: Sure. We have a large Fortune 20-sized company that experienced close to 42 billion web requests over a 30-day period coming through. And our secure web gateway core component did what it was supposed to do. It analyzed the traffic, categorized the websites and blocked 48 million malicious sites. Some 2.4 billion files were then sent to Content Analysis for inspection. Of those, 539,000 files ended up in the sandbox – of which only 389 risky files were identified – a very manageable number for this customer’s IR team. They were so excited with the results that they created their own version of this funnel slide to show to their board and convey the effectiveness of their Symantec solution, powered by Proxy and Content Analysis.
Q: That seems like a huge saving in time for the SOC team, would you agree?
A: Massive. It meant that their security operations and response teams had far fewer files to deal with so they didn’t have to waste time and resources. Before they deployed this process, they were dealing with 4,000 events on a monthly basis. Now it's down to less than 400 risky files that are identified as needing deeper investigation. This is what makes Symantec Content Analysis unique.

Symantec Enterprise: It’s Time to Shift the Appliance Paradigm
Introducing the new Secure Web Gateway








We encourage you to share your thoughts on your favorite social platform.