Securing the OSs of Today and Tomorrow
Symantec Endpoint Security is the answer to protecting modern devices – in addition to traditional endpoints – in a single solution
The divide between traditional and mobile devices that has long existed in enterprise endpoint security is quickly fading. CISOs and their teams are increasingly seeing the importance of securing mobile devices, in addition to traditional workstations. Employees often read their emails for the first time on their phones and conduct a fair share of business transactions on them. Mobile devices are also increasingly used for multi-factor authentication (MFA) into sensitive corporate systems. In fact, mobile endpoints now outnumber traditional endpoints in the workplace. It only makes sense, then, to extend endpoint security to mobile as well.
While sophisticated security teams realize they must protect data consistently across all of today’s operating systems and endpoints, I argue this is no longer enough. We need to be ready to protect both today’s – and tomorrow’s – operating systems.
Few organizations are ready for a new breed of “modern” OSs that is starting to run on traditional workstations. “Modern” is no longer just mobile, but also traditional OSs that are becoming always-connected, more locked-down, and enablers for constant access to personal and corporate data in the cloud through available networks.
Symantec is the only vendor that protects all major operating systems – traditional and modern – in one solution. In addition to providing comprehensive protection on popular operating systems like Windows, macOS and Linux, Symantec Endpoint Security addresses the growing trend of modern OSs such as Windows 10 in S mode, Windows on ARM, iOS and Android, and delivers advanced protection capabilities to combat the types of threats that target these newer OSs. While modern OSs are designed to be “secure by default,” as we learned with mobile, even a locked-down OS can be exploited.
When Traditional Becomes Modern
As business users expect constant connectivity and are always on the move, traditional OSs are evolving to accommodate these behaviors. The newer Windows and macOS versions are borrowing a page from mobile OSs. Windows on Arm is “always on, always connected,” featuring integrated LTE Advanced connectivity. Out-of-the-box connectivity means certain services and apps, like email clients, continue syncing in the background (just as on mobile devices), positioning Windows on Arm as an appealing platform to business users. There is already a wave of these new Arm-based PCs/devices coming from Microsoft, Lenovo, Samsung, and others. Microsoft recently announced two new Surface devices: Surface Pro X and Surface Neo, both of which are running Windows on Arm.
Additionally, Microsoft is securing workstations running Windows 10 in S mode much the same way iOS and Android devices are secured. In S mode, applications that users install from the Microsoft Store are sandboxed (like app sandboxing on mobile). These user-installed apps run in their own user partition so they can’t access system files, or data and files from other applications. This minimizes the risk of data breaches, as any malicious code that is downloaded onto the PC will be contained, unable to affect the OS and other apps and files.
For all the benefits that constant connectivity brings, it can be a double-edged sword.
As these types of devices become more common and connected computing becomes a business necessity, security teams need to be prepared to protect new modern OSs. While locked-down systems are supposed to be more secure, we’ve seen that OSs like iOS and Android are susceptible to their own set of threats, including OS vulnerabilities, network-based attacks, and malicious and vulnerable apps.
Furthermore, for all the benefits that constant connectivity brings, it can be a double-edged sword. Always-connected devices are always reachable; even when you hit the power button, the device is still connected to a network and still active. These devices are also more vulnerable to network threats as they connect more to public Wi-Fis. Any poorly-secured device that has been compromised and then accesses a corporate resource or network serves as a potential avenue of attack. These risk factors make modern OSs an attractive, high-value target for hackers.
Endpoint Security Protection for Modern Operating Systems
Until recently, the thinking in enterprise was that measures for securing traditional endpoints needed to extend to mobile devices. Today, it is clear the model has turned: organizations will need to extend mobile endpoint protection techniques to traditional endpoints as their OSs become more connected and more locked-down. To be successful in the future, organizations need to have a strong modern security foundation.
The good news is that Symantec Endpoint Security is already doing this. We’ve been leading the way in protecting modern OSs for years, through our robust mobile threat defense solution. We’ve borrowed concepts like network integrity for securing iOS and Android devices and applied them to Windows 10 devices, providing active and automatic protection from modern threats. The Endpoint Security app is built on Microsoft’s Universal Windows Platform (UWP), meaning it can be distributed through the Microsoft Store and can run on Windows 10, Windows 10 in S-Mode and Windows on Arm devices.
Essentially, we’re able to deliver out-of-the-box, automatic detection and protection against device and network-based threats, without requiring drivers and kernel extensions to run natively on modern devices. This includes protection against malicious apps and profiles, risky Wi-Fi and carrier networks (evil twin hotspots, fake corporate hotspots, etc.) and exploits of unpatched app and OS vulnerabilities. With our network integrity feature, any time the network state changes – let’s say you disconnect from one network and connect to another – Endpoint Security automatically performs tests on that network, similar to how our mobile security agent validates networks that your mobile devices connect to. If a threat is detected, we immediately activate protection actions such as VPN tunneling or blocking access to sensitive corporate resources.
Let’s look at a specific example of Endpoint Security protection on mobile devices. An employee connects to a fake corporate hotspot at their organization’s campus, believing it’s the real corporate network. There is a man-in-the-middle (MiTM) attacker on the network who can see all of the employee’s traffic, including his credentials as he attempts to authenticate to a corporate resource. Mobile users are generally socially engineered into installing a root certificate authority (CA) on their device to allow for seamless decryption of their traffic. On an Endpoint Security-protected device, a VPN tunnel would automatically be activated upon detection of the threat to block the MiTM attacker. This allows the employee to continue using their device seamlessly while protected from the network threat. Endpoint Security can also detect root CAs on both iOS and Android.
Without these automatic detections and protections, sensitive corporate data could end up in the attacker’s hands. In addition, if the organization was relying on a third-party service for enforcement, the attacker would have been able to block it, underscoring the need for on-device protection.
If a VPN tunnel cannot be established, our Sensitive Resource Protection (SRP) can be activated as a fallback layer of protection. Admins can define company resources they want to protect, such as an email or AD domain, in the security policy, and in the case of a network attack, these resources will be isolated on the device, safe from exploitation by malicious actors.
Beyond network threats, Endpoint Security provides protection against app, OS-level, and network content exploits, across all OSs. In terms of protection at the app level, we perform app scanning and analysis on the public app stores, and can block malware or terminate malicious processes before they leak sensitive data. Windows 10 in S-mode may prohibit non-Microsoft Store apps in an attempt to make the OS more secure, but that doesn’t mean the Store is completely clean of risky apps. We’ve repeatedly found deceptive, potentially unwanted applications (PUAs) with risky behaviors and dodgy content built for Windows 10 and Windows 10 in S-mode.
Risky apps can also sneak their way into Apple systems – and we're leveraging our vast mobile app reputation database to stay one step ahead, even on the latest closed macOS versions. MacOS Catalina requires that all new software and apps be notarized. This means that Developer ID-signed software must undergo automatic scans and security checks to validate that it is not malware. The notarization service is intended to prevent the unauthorized use of trusted developer certificates to distribute software. But as one app developer points out, “it doesn't protect against malware authors simply paying $100 (perhaps with fraudulently obtained credit card numbers) to sign up for their own Apple Developer account and notarize their own software with their own Developer ID certificate and their own Apple ID.” This has actually happened here and here, and there have been cases where malicious code has gotten into apps without developers even being aware of it, via the supply chain method. At Endpoint Security, we have extensive experience detecting exploitation of Apple enterprise developer certificates on iOS and can detect these types of threats:
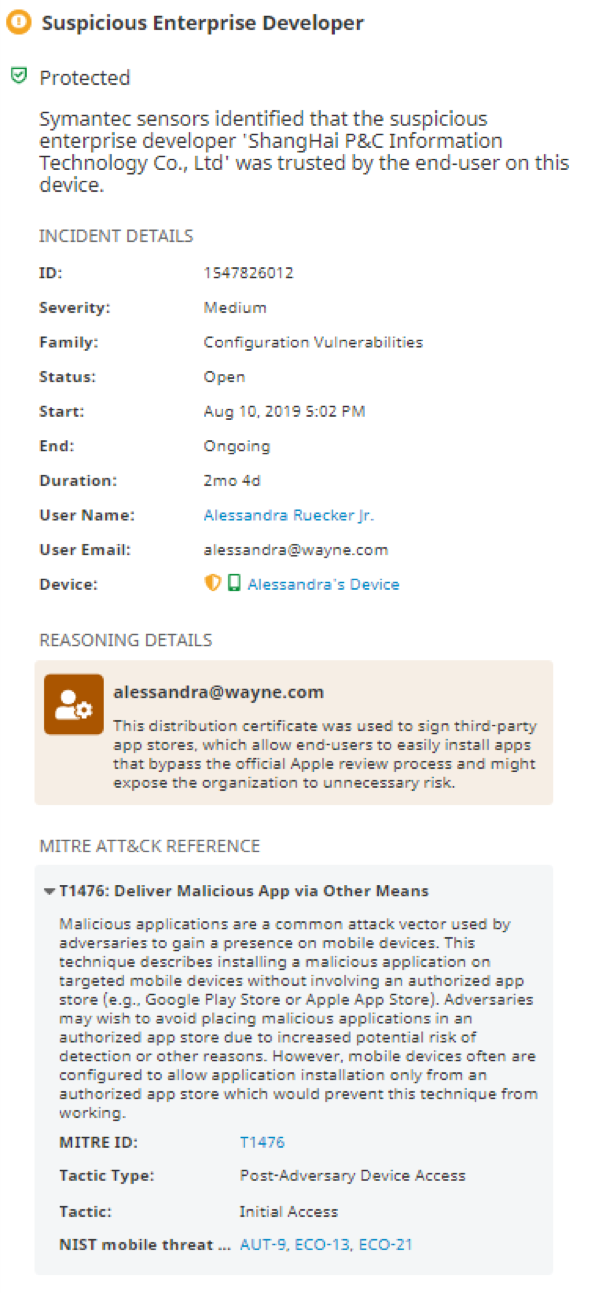
At the OS-level, Endpoint Security provides vulnerability management for all OS versions. For example, we can detect which endpoint doesn’t have a specific Microsoft patch installed. We also detect vulnerable app versions and can trigger patching and updating to non-vulnerable versions.
Windows, iOS, new OS? There’s an Endpoint Security Technology for That
Visibility is a critical component of any security product, especially for admins. But in modern, locked-down OSs, where other security products need access to elevated privileges to run agents properly – Endpoint Security’s UWP-based agent runs natively. If a risky network is detected, an event and alert are automatically raised in our Integrated Cyber Defense management (ICDm) cloud console with details about the detection.
It’s important to note that this visibility extends across ALL operating systems in an environment. If a threat is detected on any endpoint, events, alerts, and security incidents will appear in the ICDm console, giving security teams unprecedented insight into their entire threat exposure.
Our detections and protections are part of a single product stack that incorporates several different technologies working together under the hood. You don’t have to worry about going through multiple RFPs to acquire separate products, each with their own levels of protection, policies, enforcement, and management for each type of OS you want to protect. You get full coverage in one license, with single agent installation. Simply decide what devices you want to protect, and Endpoint Security provides the technology that best fits each one. That seamless integration and simplicity is hard to come by anywhere else.
The future is an Ever-Connected OS
Traditional and mobile OSs are converging. The result is modern OSs that run on traditional workstations but are designed to accommodate constant connectivity and cloud access, anytime, anywhere. These systems are different from the legacy code that is the traditional Windows and macOS we’ve been accustomed to. They are adapting to different user behaviors, device types and functionalities, bringing with them a host of benefits, but also security challenges. These changes require a new security model that can protect against increasingly-sophisticated modern threats. Symantec Endpoint Security is the only solution with the technology stack to protect these modern systems in addition to traditional OSs, with a single agent installation. Our robust protection, detection and response capabilities extend across all OSs and endpoints in your environment, ensuring they stay safe from all attack vectors. In view of the many changes OSs are undergoing, tech writer Navneet Alang recently proclaimed that “we’re losing control of our computers.” I’d argue, organizations that don’t properly protect modern OSs like mobile, will be losing control. Are you ready to protect your endpoints as this shift occurs?

Endpoint Defense Starts with Prevention
It’s no longer enough to discover and expel attackers as the dangers posed by endpoints continue to climb










We encourage you to share your thoughts on your favorite social platform.