Few Phish in a Sea Protected with Email Threat Isolation
While phishing attacks have become more sophisticated, users can now protect themselves in way than was ever previously possible. Here’s how
Over the past year, email-based phishing attacks have continued to present a major risk, exposing organizations to malware infections, information theft and other cyber misdeeds. This no longer needs to be the case.
Why not? Because, in July 2018, Symantec enhanced its existing portfolio of email security defenses with powerful new technologies. Those technologies can stop many phishing emails in their tracks and can short-circuit the threats posed by any malicious messages that manage to get through to their targets.
Phishing exploits – as far too many organizations have learned the hard way – aim to trick email recipients into either clicking on an embedded link or opening an attachment. The links bring users to malicious websites that often mirror the appearance of legitimate sites. Once a connection is established, the site may ask the victim to enter sensitive credentials and other private information or may simply download some form of malware to the user’s computer or device.
Phishing exploits – as far too many organizations have learned the hard way – aim to trick email recipients into either clicking on an embedded link or opening an attachment.
In the same fashion, email attachments can be used to spread malware. What may appear to be trustworthy documents, may immediately inject malware (via scripts or macros) into the unfortunate user’s device. This is a growing problem and one that it is hard for users to be vigilant against. During 2018, nearly half (48%) of all malicious email attachments were Microsoft Office files, up from just 5% the previous year, according to Symantec's annual Internet Security Threat Report (ISTR).
The phishing threat is broadly recognized, and most organizations have made at least some attempts to educate their users about safe email practices. The good news is that 78% of users never click on a phishing email all year, according to Verizon’s 2018 Data Breach Investigations Report. However, this still means that 22% of users will, and unfortunately, Verizon also found that for any given phishing campaign, on average, 4% of recipients will click on the phishing link or attachment.
That hit rate was enough to make phishing attacks the third-most common attack method used in successful cyber breaches during 2018, Verizon reported.
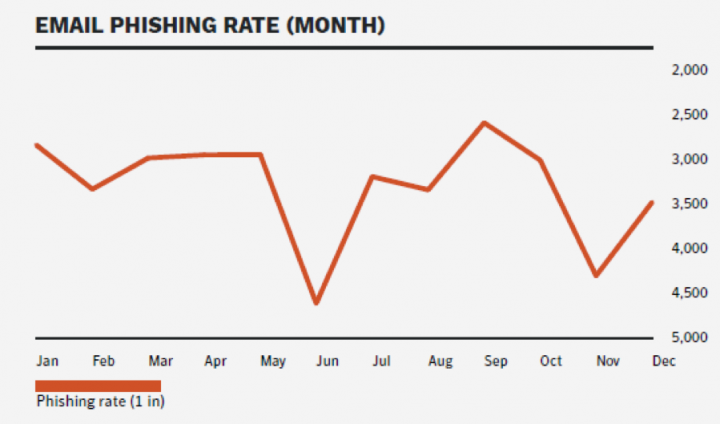
The frequency of phishing attacks has fluctuated in the recent past. Phishing assaults declined very slightly during 2018 compared to the prior year, with 1 in every 3,207 emails in 2018 representing a phishing attempt, Symantec’s ISTR reports.
Phishing attacks have also become more sophisticated, with many relying on advanced social engineering techniques and public information about targeted users to craft messages that even cautious recipients may have difficulty rejecting.
Symantec has deep visibility into phishing and other email-based exploits because our collection of on-premises and cloud-based security products and services processes more than 2.4 billion emails each day. Products including Symantec Email Security.cloud, Email Threat Detection and Response and other offerings provide a layered tier of defenses for service providers, organizations, and individuals.
The first line of defense against emails containing embedded links, of course, is to identify links to known malicious sites and to block the emails’ delivery. Many phishing exploits attempt to hide the ultimate destination site by redirecting a clicked link through multiple hops before arriving at the malicious final stop. While some security controls can only follow redirects through one or two hops, Symantec Link Protection can follow the path through these redirects to the end destination.
How ETI Neutralizes Malicious Attachments
In practice, however, it isn’t always possible to determine with certainty whether a linked site is good or bad – many fall into a gray zone. This situation may occur, for example, with sites that initially appear safe, but become weaponized some time after the initial receipt of the phishing emails that contain their links.
To deal with these nebulous websites – and also to neutralize malicious email attachments – Symantec introduced its Email Threat Isolation (ETI) technology, an industry first. In essence, this technology virtualizes web browsers in a virtual, secure and disposable container to create a safe execution environment to run the web sessions between the user and a potentially dangerous site. The user experiences nothing different from a normal website interaction but should the site attempt to download some form of malware or exhibit other threatening indicators, the threat is contained in the isolation container and eliminated. Similarly, suspicious attachments can be opened in an isolated container and presented in read-only mode to keep the user safe from infection.
By adding ETI to its layered phishing defenses, Symantec has been protecting users in a more effective way than was possible before. We identify 1 in 3,207 emails as a phishing attack (0.03%) and block these threats using click time protection. However, we also know that customers often receive emails that link to unknown websites – that is, sites that may be safe or dangerous. In these instances, our isolation technology serves to de-risk this email traffic.
To deal with these nebulous websites – and also to neutralize malicious email attachments – Symantec introduced its Email Threat Isolation (ETI) technology, an industry first.
Analysis conducted by the Symantec Technology and Response (STAR) organization shows that 7% of customers’ entire email, on average, links to such potentially risky websites. For these “gray” websites, ETI functions as a preventative measure. With ETI, users can browse these websites with complete safety, no longer at risk from malware infection or credential theft. Therefore, ETI provides a valuable layer of protection without impacting the end user experience and is a marked improvement on just blocking access to known bad websites.
Symantec ETI is offered both within the Symantec Email Security.cloud solution and is also available as a standalone product that works with other vendor’s email security solutions.








We encourage you to share your thoughts on your favorite social platform.