Beyond The Vault – Where to Take Your PAM Implementation Next with Symantec
What are the critical capabilities that you should be implementing next and why?
Many data breaches and insider attacks exploit privileged accounts and credentials. This is not surprising when you consider that privileged identities have elevated access to the most sensitive resources and data in your environment; they literally hold the keys to the kingdom. As the role of compromised privileged accounts and credentials has become clear, regulatory bodies and auditors have focused their attention on controls that organizations must implement to mitigate these risks. As a result, privileged access management (PAM) has been a hot technology for the past few years.
The first capability that most organizations deploy is the privileged credential vault. Removing shared passwords from the hands of multiple users and putting them into an encrypted data store yields significant benefits, including but not limited to enforcing policy-based access control over which credentials a privileged user may access; monitoring all privileged activity and linking that activity back to an individual user; and rotating these credentials automatically on a periodical basis to comply with security mandates. But is this enough? Where should organizations evolve their PAM deployments next?
Symantec, a division of Broadcom Software, suggests the following critical capabilities that will complement your privileged credential vault.
Verification through Strong Authentication
Multifactor authentication is being mandated by many industry and regulatory laws for privileged access. Because this is not natively supported in many systems, PAM tools are often used to implement this capability by requiring users to present this level of credential before granting access to privileged credentials stored within their vaults.
Symantec PAM supports a wide range of MFA credentials, and can even provide them to organizations that do not already have a solution through Symantec VIP. Symantec VIP is a leading user-friendly, cloud-based, strong authentication service that provides secure access to sensitive data and applications anytime, anywhere, from any device enabling a critical piece of your Zero Trust security strategy.
Accountability through Session Recording
One of the fundamental issues with privileged accounts is that users are given elevated access to sensitive apps, infrastructure, and data with no accountability. Even worse, understanding what the privileged user did, either accidentally or maliciously, to repair the damages can takes days or weeks of investigation.
Symantec PAM enables full attribution for shared account activities. The solution separates user authentication from shared account access, enabling the ability to link session-based clicks, commands, and entries to the individual user who “checked out” the credential. This audit data is stored in an encrypted, tamper-proof vault, where you can view it with internal tools or export it. The solution can also capture a video recording of all privileged user activity to improve accountability and provide forensic evidence of malicious activity.
Mitigation through Risk & Behavioral Analytics
Organizations often lack visibility into how privileged credentials and accounts are being used every day, so they cannot detect anomalies in user behaviors. That situation, combined with the expanded access granted to users, gives both external hackers and malicious insiders more pathways through which to exploit potential vulnerabilities.
Symantec PAM supports User and Entity Behavior Analytics (UEBA) through an option module called Threat Analytics. This tool continuously monitors all privileged user activity and compares current activities against historical data to detect changes in behavior. When detected, advanced algorithms can assess the risks associated with these activities, and if needed, trigger automated mitigation actions to address the risk.
Prevention through Granular Access Controls
As was learned from the recent Solar Winds attack, determined hackers will find sophisticated ways to penetrate your defenses, gain access to your network, and compromise a privileged credential. In fact, this is the third principle of Zero Trust: assume breach. The question is, how do you minimize the damages a hacker can do once they are inside?
Symantec PAM provides highly granular and role-based access controls for physical, virtual, and cloud resources using an agent-based approach that can help prevent or minimize damages of an actual breach. Unauthorized commands are blocked and logged, and the security team can be notified about policy violations. Socket filtering detects leapfrog attempts, regardless of the command used, and blocks attempts to create an outbound socket or connection. Symantec PAM provides centralized Separation of Duties (SoD) policy store to ensure that administrators have only the privileges they need, even when users are accessing the same “root” or “system admin” account.
Symantec PAM provides highly granular and role-based access controls for physical, virtual, and cloud resources using an agent-based approach that can help prevent or minimize damages of an actual breach.
It should be noted that this level of control is not needed for every element of your infrastructure. For example, two critical aspects in a Zero Trust Architecture are the Policy Decision and Policy Enforcement Points, both of which are the focal areas for an attacker once they have gained access to an environment. These systems must be safeguarded with the most stringent application of a layered defense model, which should include the implementation of fine-grained access control for privileged users and accounts.
Secure your DevOps through Secrets Management
Software is the key driver of growth, innovation, efficiency and productivity, and DevOps pipelines are at the heart of many digital transformations, but simple continuous delivery is not enough anymore. You need both intelligent and secure pipelines to help you release higher quality software at greater velocity and reduced risk. Although privileged access is more commonly associated with people, the reality is that numerous applications have privileged access to sensitive resources, and in many cases, this access is granted via hard-coded administrative credentials that are ripe for theft and misuse, often with little to no security protecting them at all.
Symantec PAM eliminates hard-coded, hard-to-change passwords from applications and scripts through secrets management, providing effective protection and management of these so–called “keys to the kingdom”. Application–to–application passwords and other credentials are stored in an encrypted vault, and requesting applications must authenticate to the solution before these credentials are released. Additionally, Symantec PAM further enables enterprises to automate the creation and provisioning of new devices within the solution via REST APIs, which ensures that each new server, container, and environment has its privileged credentials and accounts protected as soon as it is created by the DevOps tool chain.
Protect your Hybrid Environments
As your IT environment has expanded outside your four walls to incorporate public cloud resources and software-as-a-service (SaaS) applications, the traditional way of approaching administration and operations has also quickly fallen apart—mainly because it fails to protect new attack surfaces like management consoles and APIs.
Symantec PAM is designed to prevent security breaches across virtual, cloud, and physical environments by protecting sensitive administrative credentials, controlling privileged user access, proactively enforcing security policies, and monitoring and recording privileged user activity. It can not only discover, protect, and provide granular separation of duties for cloud consoles and APIs and virtual resources, but it can also secure privileged access on your legacy mainframe environment and mission-critical servers.
Least Privileged Access through Identity Governance
The second principle of Zero Trust is to ensure least privileged access. In fact, organizations are subject to an ever-expanding list of data security regulations and standards that mandate increased auditing and control over users with privileged access. Compliance with these regulations and audits generally focus on two points:
- Control the access of privileged users to critical resources and the actions that they can perform on those resources.
- Govern the access of privileged users on an ongoing basis to make sure that they have only the level of access that they absolutely need (i.e., least privileged access).
PAM technologies addresses the first point; and identity management technologies addresses the second point, and when you integrate the two, this yields privileged access governance. Privileged access governance ensures that all user access to privileged accounts and credentials is required and appropriate through automatic provisioning and de-provisioning of these access entitlements and streamlined process to periodically review and certify that access to privileged accounts is still necessary. Privileged access governance significantly improves your security posture and helps address compliance. When auditors ask you for proof, you will have it.
Summary
Symantec PAM provides holistic privileged access security for improved flexibility with a single admin console for ease of use. Delivered as a software- or hardware-based appliance, it can be deployed in minutes and scales with minimal infrastructure requirements to yield a low total cost of ownership.
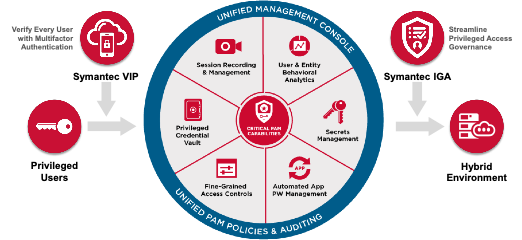
Symantec PAM offers greater defense-in-depth because it is part of our larger security portfolio, which includes Symantec VIP for multifactor authentication and Symantec IGA for privileged access governance.

The Role of Symantec Privileged Access Management
A Conversation with KuppingerCole Analyst Paul Fisher








We encourage you to share your thoughts on your favorite social platform.