You Can Solve it with Symantec Endpoint Security
In an ever-changing world, it’s good to know you can have the best
The COVID pandemic has turned workplace norms inside out. Last year, almost 70 percent of full-time workers telecommuted. They liked it so much that three quarters of them want to keep it that way. While the move could save billions in office rent, it presents a spectacular security challenge.
Teleworkers access corporate networks from a multitude of personal computers, smartphones and tablets that are often shared. Many depend on cloud and server architectures that are vulnerable. There are also more applications introduced to the workplace than ever before. The result is a huge expansion of the attack surface which makes security all the more important.
That’s why you need the best protection: Symantec
Symantec, as a division of Broadcom, has industry-leading endpoint solutions to secure laptops, desktops, iOS phone and tablets, Android phones and tablets, servers, storage, human-machine interface and operational technology, cloud workloads, containers, and cloud storage.
You don’t need to take our word for it
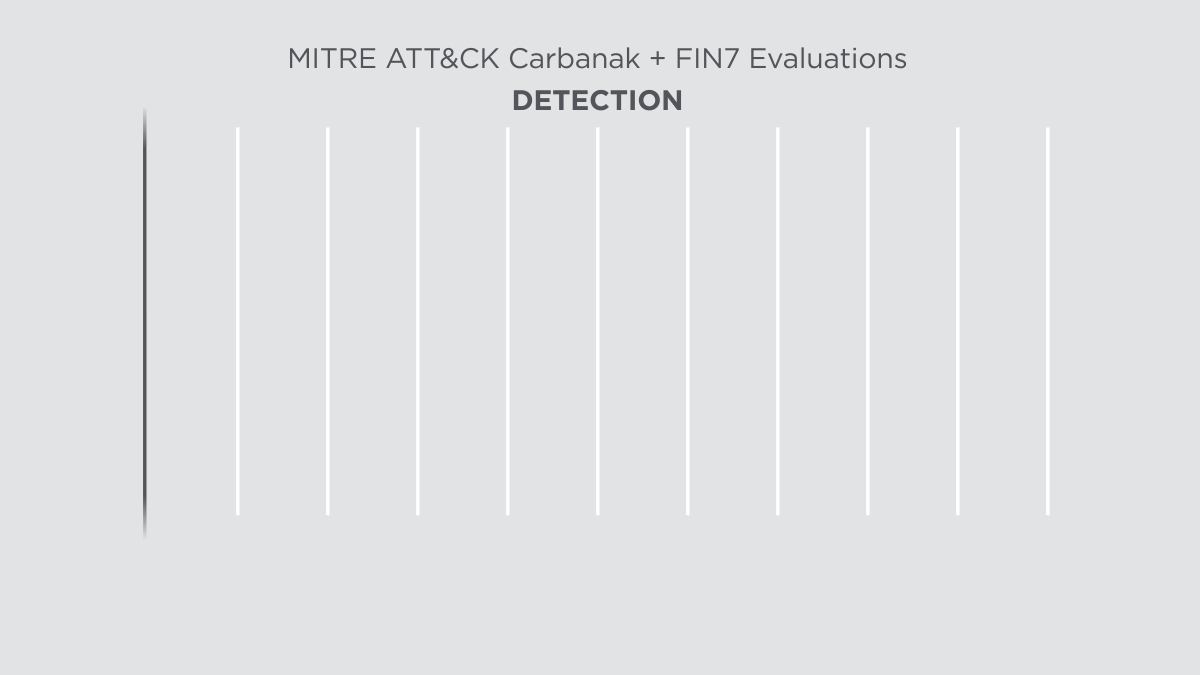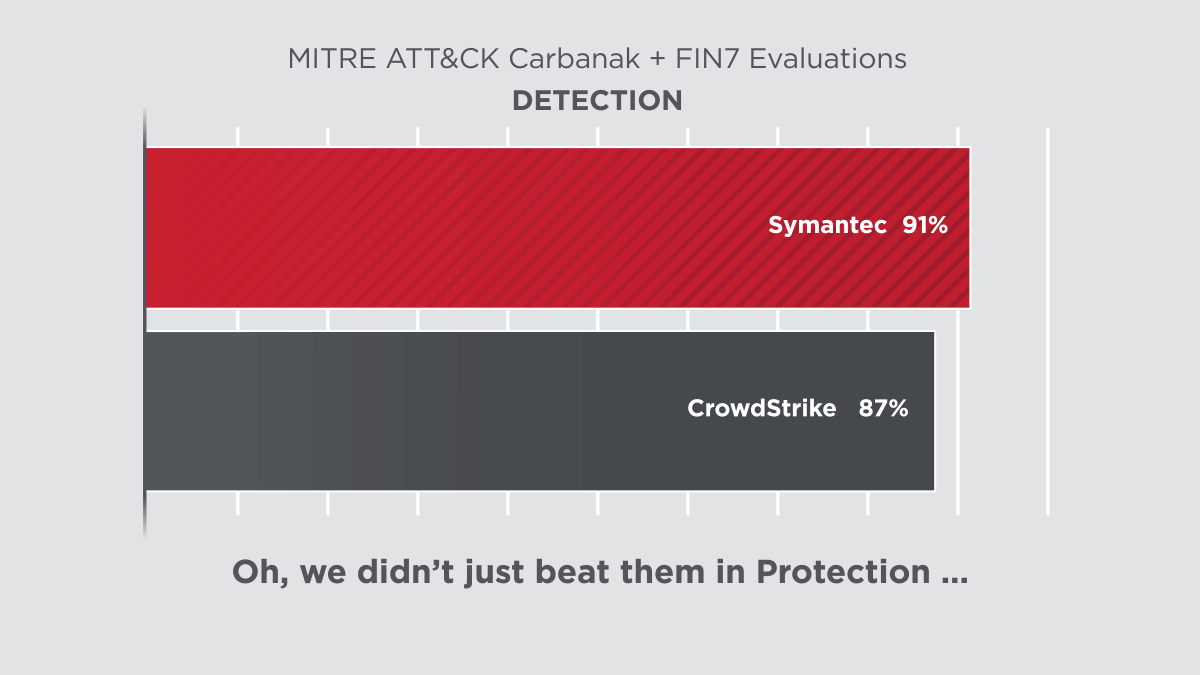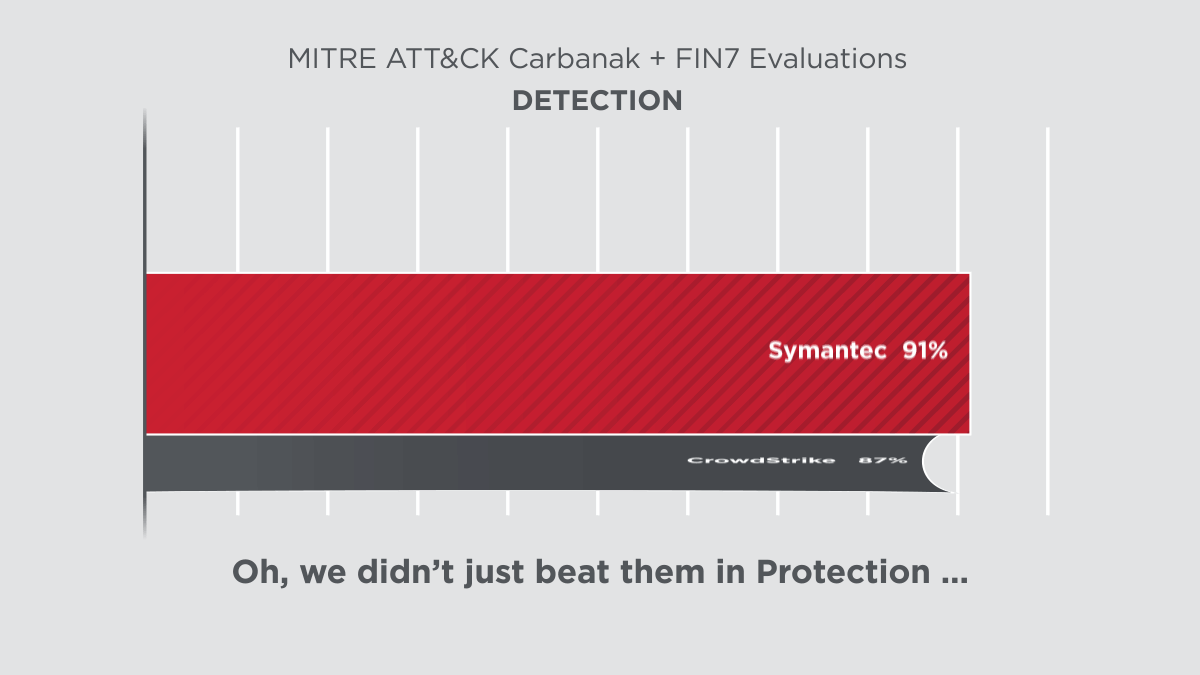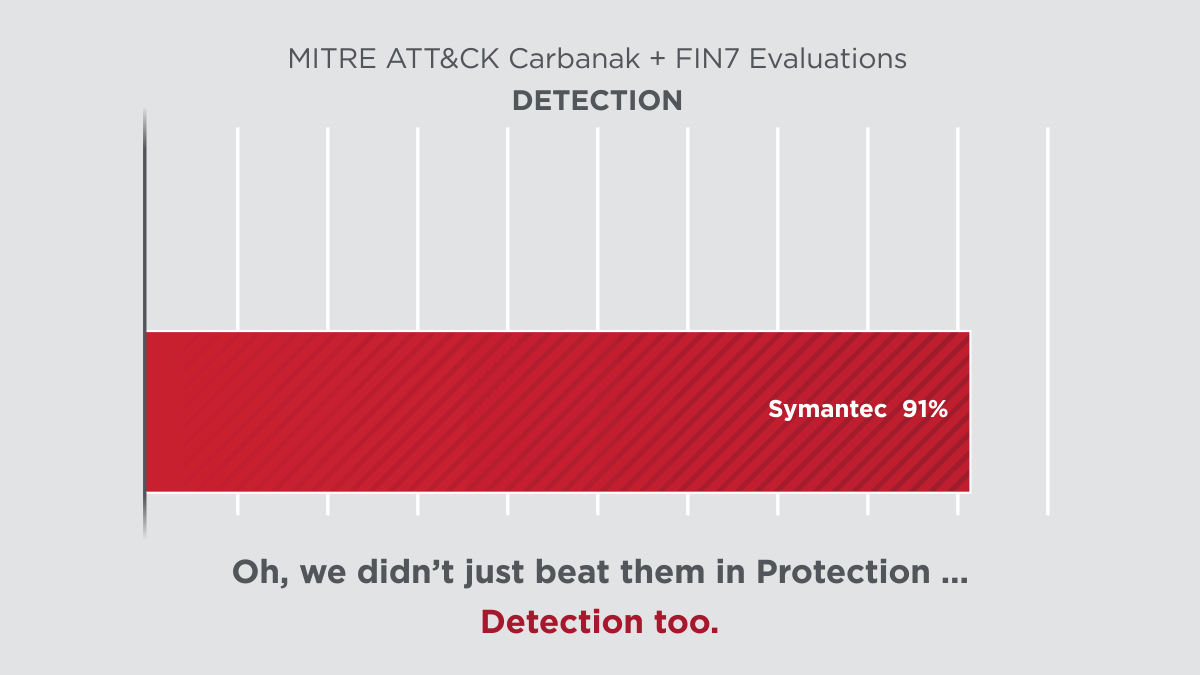
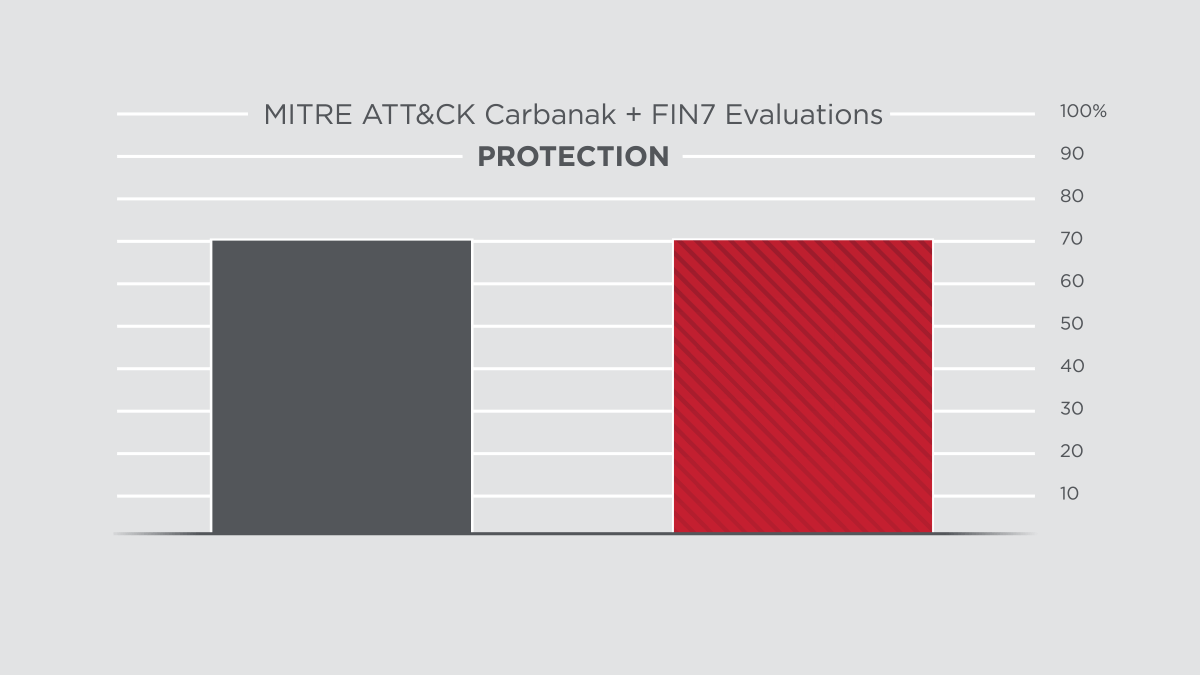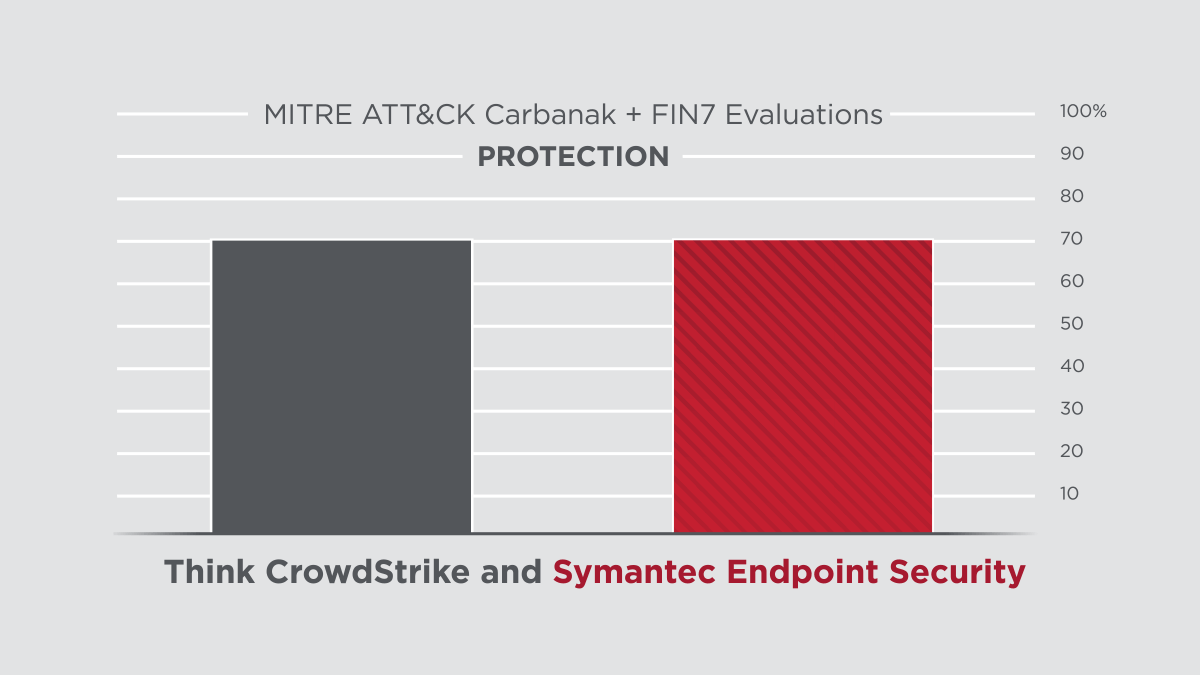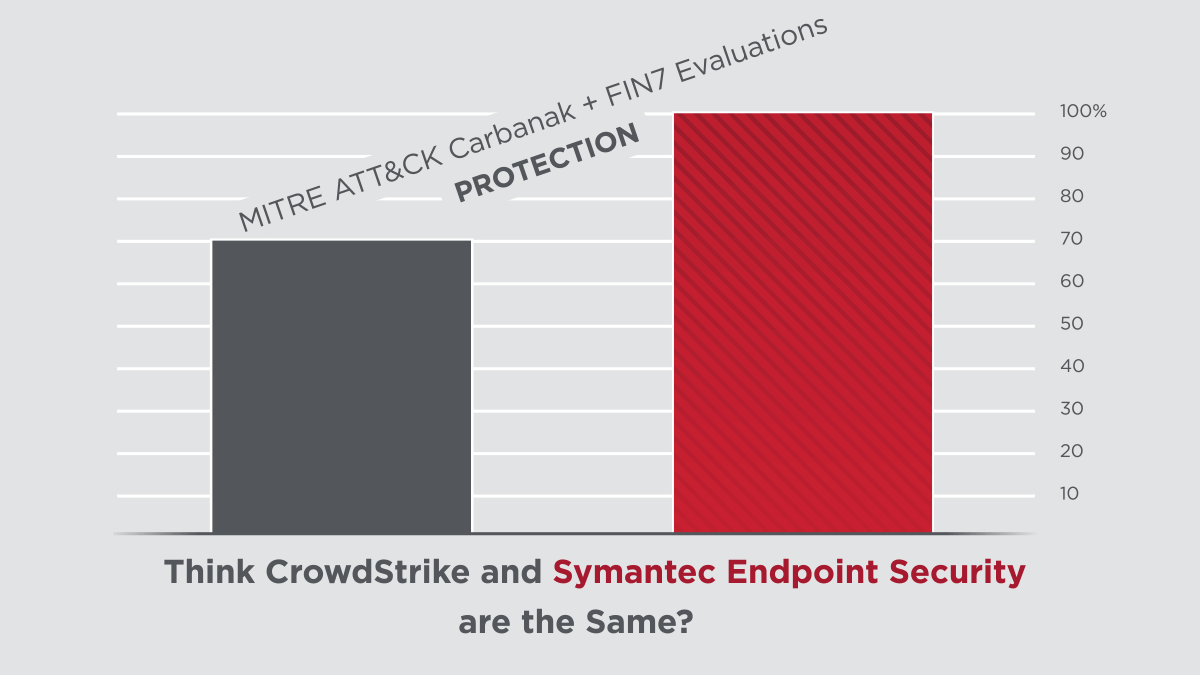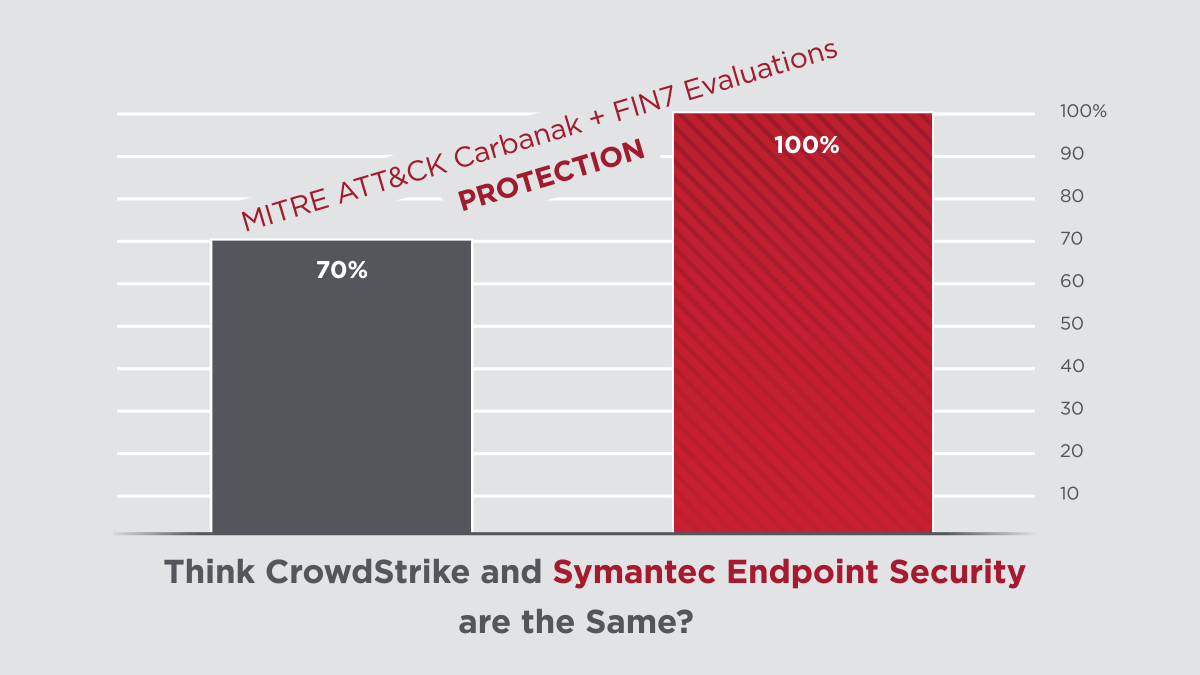
Symantec’s latest protection and detection innovations delivered clear results in the 2020 ATT&CK Evaluations, performed by MITRE Engenuity. The assessment subjected the security offerings of 29 different vendors to 174 detection tests and 10 prevention tests. Symantec scored 100% in all prevention tests and 91% in all detection tests. Not only are we a clear leader in protection, but also in combined protection and detection among our top competitors.
As MITRE's assessment showed, Symantec’s Endpoint Security solution provides robust threat blocking capability where other products, such as CrowdStrike, are just not able to perform.
Symantec Endpoint Security Complete deploys a range of technologies that deliver proactive attack surface reduction and innovative attack prevention providing the strongest defense against the hardest-to-detect threats, particularly those that rely on stealthy malware, credential theft, file-less, and “living off the land” attack methods. Among these powerful technologies are:
- Advanced Machine Learning and Artificial Intelligence – which uses advanced device and cloud-based detection schemes to identify and connect the dots between evolving threats across device types, operating systems, and applications. Attacks are blocked in real-time, so endpoints maintain integrity and negative impacts are avoided.
- Advanced Exploit Prevention – which combines sandboxing and file behavioral monitoring with technique-based blocking of in-memory zero-day exploits of vulnerabilities in popular software.
- Adaptive Protection – which surgically limits behaviors of trusted applications with minimal operational impact but maximum protection from the dual-use techniques attackers rely on.
Attacks on the rise: Symantec protects you against them all
Ransomware attacks are on a meteoric rise. The latest big incident may have affected between 800 and 1,500 companies around the world. The assault began with a supply-chain attack against Kaseya, an IT management software provider that caters to enterprise IT teams and managed software providers. The attackers were reported to be the REvil Russia-linked hacking group responsible for other recent high-profile attacks such as the one targeting the meat processor JBS. REvil has gone dark in the last month, but most expect the criminal outfit will be back soon.
New trends are showing that ransomware gangs will often take the time to steal data and delete backups before they encrypt victim’s devices, providing a stronger incentive to pay up to ensure restoration.
Supply chain attacks are particularly pernicious and expected to quadruple this year. Here an attacker breaks into a software vendor and modifies the product. The company then ships the infected code to its customers. The most recent SolarWinds Orion attack was a trojan that modified a SolarWinds’ Dynamic Link Library file which was then distributed to the company’s 18,000 customers. That included 40 federal agencies and nearly all Fortune 500 companies. The exploit opened them all to sustained intrusion, espionage and embarrassment.
Living off the land attacks use common applications that are on the endpoint already – many are built into the operating system, and most are ones that companies already employ in their day-to-day business operations. Attackers can lurk in those applications and it can be nearly impossible to identify anything as suspicious since it looks like normal activity.
Protect yourself: choose Symantec Endpoint Security
The slew of high profile breaches over the last 6 months demonstrate that enterprises need to step up their security posture. Advanced technologies are required to thwart advanced threats. Luckily, you don’t need to purchase a plethora of solutions for full protection. All of Symantec’s advanced protection and detection technologies are available with Symantec Endpoint Security.
If you’re a Symantec Endpoint customer working on-premise, in the cloud, or if you’re in transition, you’ll continue using the same agent. And new customers get a choice of deployment options right out of the box. With Symantec Endpoint Security, you get a robust solution, and you get a simple path to deploying it in your environment, too. When you choose Symantec Endpoint Security, you’re choosing the best!

Symantec Endpoint Shines in the 2020 MITRE Engenuity ATT&CK® Evaluations
Finding breaches is good but preventing them is critical








We encourage you to share your thoughts on your favorite social platform.