Symantec’s Global Intelligence Network: 20+ years of Intelligence Analyzed and Categorized
One of the largest civilian security threat intelligence networks in the world
If you want to get a taste for how things can change over time, 20 years is a good time measurement.
For example, here we are in 2021. And while 2001 might not seem like a long time ago, keep in mind that 20 years ago, the Golden State Warriors finished their season with a record of 17-65, Blockbuster Video stores were still going strong (and not giving a thought to a little company called Netflix), and Apple was still a few months away from releasing the first iPod, and, eventually, upending the music industry.

Yes, times and trends change. But, one thing that remains as consistent is Symantec's, as a division of Broadcom, commitment to threat intelligence gathering and analysis. And after 20 years, our Global Intelligence Network (GIN) is emblematic of how our experience, and the sheer scale of real-time data that we analyze and assess, provides the best tools and experts around when it comes to identifying and detecting threats quickly and protecting customers from attacks.
Symantec’s GIN is one of the largest civilian security threat intelligence networks in the world. Our GIN correlates information from 175 million endpoints, more than 126 million attack sensors, 160 million email account users and 80 million web proxies. And with that, we analyze more than 9 billion petabytes of security data, categorize 75 million malicious activities, and process 1 billion security requests a day.
With such scale, Symantec’s GIN is capable of identifying threats even before zero day. The game of cat and mouse becomes moot because of our ability to quickly let customers know about threats, provide them with the tools they need to block attackers from getting inside their networks, and detect and delete threats should an attacker manage to get inside an organization.
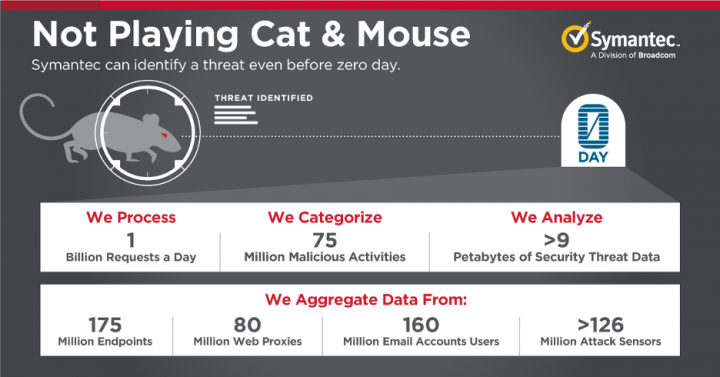
We don’t wait around for bad things to happen. With its ability to identify so-called 'One-Hit Wonders', Symantec’s GIN is unique. These One-Hit Wonders are the kinds of sites that network attackers put up, use to do whatever malicious activities they have in mind, and then take down all on the same day. A security vendor who relies on data that is, for example, seven days old before assessing an attack- is basically letting the bad guys get away. Our GIN goes after One-Hit Wonders the day they attempt their attacks and works to stop those attackers before they can wreak havoc on a network.
While collecting data on threats is extremely important, our GIN is about more than that. We leverage data from third-party threat feeds, analysts and customers who are willing to share their telemetry with us. With that information, Symantec applies machine learning along with advanced analytics to glean insights on threats and attacks. We store all of that in a data lake in the cloud for the quickest possible access and use.
And we don’t forget the human factor, either. Our GIN’s tools and solutions are bolstered by a team of thousands of analysts that work 24 hours a day, seven days a week, to bring experience, expertise and technical knowhow to the battle against organizational threats of all stripes and colors. You can say that when the machine can’t identify something, we have the humans in place to take over and get the job done.
We don’t wait around for bad things to happen. With its ability to identify so-called 'One-Hit Wonders', Symantec’s GIN is unique.
But, even with all of our skills, scope and size, we have not forgotten about the need of companies to ensure the privacy of individuals. We neither collect, nor retain, any sensitive information that is unnecessary. We do this through the use of data-minimization and privacy-by-design principles. We obfuscate data when necessary in order to ensure the privacy of legitimate users, while still collecting the information needed to identify and fight back against threats and attacks.
Whatever a company’s cyber security requirements may be, Symantec can customize a solution to fit those needs. The key ingredient is machine learning built on decades of Symantec experience and the GIN, working with large organizations to automate the configuration of protection settings and deliver the highest level of custom protection with zero impact to productivity.
Our decades of intelligence expertise is also verified by the reach Symantec’s GIN has among the biggest companies in the world. We serve more than 90% of Fortune 50 companies, and 8 out of every 10 companies in the Fortune 500. And we have assisted in the arrest of more than 150 alleged cyber criminals.
The status of Symantec’s GIN has been 20 years in the making. And when you have 20 years of experience under your belt, you’re going to see things that others won’t. The best intelligence is real-time intelligence, and that is what Symantec’s GIN has delivered as part of the world’s largest global security community. And that is also what customers can expect, and will get, in the years to come.







We encourage you to share your thoughts on your favorite social platform.