Symantec Integrations Boost Privacy and Compliance
Balancing business goals, user freedom, and security takes the power of integration
Ensuring data privacy and complying with regulatory requirements are high on the to-do list of practically every organization. Businesses and government agencies are expected to protect the personally identifiable information (PII) of customers and citizens. If they don’t, stiff regulatory penalties thanks to GDPR, HIPAA, PCI-DSS and CCPA violations await – not to mention costly legal action and severe reputational damage.
But privacy and compliance demands must not erode the productivity and morale of users. It’s all a matter of balance – difficult, yet essential to achieve. With this conundrum in mind, we at Symantec, as a division of Broadcom, have implemented several integrations to enable you to achieve data privacy and compliance – both on-premises and in the cloud – without sacrificing the user experience.
Find Data Everywhere
Without Data Loss Prevention (DLP) systems, confidential data can too easily be saved by a careless user to a USB stick or other location, causing your organization to fail compliance audits. An integrated system that provides visibility and protection, wherever your data is ensures that you are not leaving sensitive data lurking the shadows. Below are some of the important integrations Symantec provides.
DLP + CloudSOC (CASB)
Your responsibility for compliance doesn’t end where the cloud begins. Symantec DLP and CloudSOC integration extends data discovery and compliance policies to more than 100 SaaS cloud applications and services, including Office 365, G Suite, and Box. It also enables you to automate policy synchronization with cloud properties.
DLP + Secure Web Gateway and/or Email Gateway
Integration between DLP and Secure Web Gateway (SWG) stops shadow data transfer to the web, even when traffic is encrypted. DLP receives decrypted traffic from the proxy, enabling inspection and policy enforcement.
Email Security Service (ESS), meanwhile, filters unwanted messages and protects mailboxes from targeted attacks. Integration with DLP delivers unified cloud enforcement of your email data policies.
DLP + Microsoft Information Protection (MIP)
MIP performs tagging, encryption, and digital rights management, ensuring that only the intended recipient can open sensitive material, regardless of the recipient’s location or device. Integration with DLP makes great technology from Microsoft even better. DLP implements policy rules to label sensitive data. Then MIP does its thing, applying digital rights management and encryption to the data. The document thus gets identity protection and can only be opened by named individuals. The digital rights follow the sensitive material wherever it goes, even if it’s downloaded to the user’s device.
Build a Cloud-Ready Policy Superhighway
Building, deploying and maintaining DLP policies is critical to ensuring reduced data loss risk. With data found everywhere yet controlled through different systems (e.g endpoint, storage, network and cloud) there are challenges in ensuring consistent protection. Without integration, you might have to create two policies for that data, one for the cloud and the other for on-prem. With DLP integration, you create the policy only once.
For cloud protection, a Symantec Cloud Security Access Broker (CASB) is a natural point of integration. Our CloudSOC (CASB) integrations enable you to extend your continuum of policies – a policy superhighway if you will – from the edge to the core of your network. Here are two examples:
CloudSOC + Cloud Workload Assurance (CWA)
A Dev/Ops contractor misconfigures an application, causing data to leak outside the organization – hardly a far-fetched scenario. Cloud-based services such as Amazon Web Services (AWS) and Microsoft Azure are used widely, but it’s easy to misconfigure cloud-based resources, leading to PII data exfiltration and compliance violations. Symantec Cloud Workload Assurance (CWA) continuously monitors cloud resources and guides remediation with steps that are easy for administrators to follow. Integration allows it to send information to CloudSOC for centralized management.
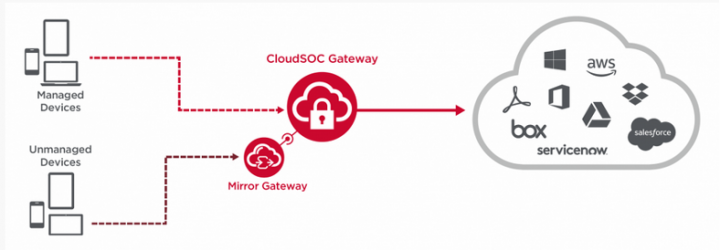
CloudSOC + Mirror Gateway
It’s not unusual for users with devices outside the scope of IT management to seek access to an organization’s cloud-based applications. These unmanaged could belong to contractors or vendors, or they could be BYOD devices of their own employees.
Your job is to enforce secure access policies or Zero-Trust Network Access (ZTNA). These policies would normally be implemented on managed devices through a Cloud Access Security Broker (CASB). For these unmanaged devices, a critical add-on is needed: Symantec Mirror Gateway. When an unmanaged device logs in, the user’s session is seamlessly redirected to an isolation chamber running a remote browser, which “mirrors” the activity of the remote user, all the while continuously inspecting traffic. The result is to enforce the security controls on unmanaged devices, without an agent, while maintaining a seamless user experience.
Knock-Knock, Who's There?
As the role of compromised privileged accounts and credentials has become clear, regulatory bodies and auditors have focused their attention on the controls that organizations must implement to mitigate these risks. Thus, organizations are subject to an ever-expanding list of data security regulations and standards that mandate increased auditing and controls over users with privileged access.
PAM + IGA
Knowing who is accessing what data gives you a leg up on the bad actors. Symantec Privileged Access Manager (PAM) controls, audits, and records access to managed devices such as servers, instances, and switches. Identity Governance and Administration (IGA) gives you comprehensive access governance and management through an intuitive interface. It also automates the granting and removal of permissions. User self-service features, meanwhile, alleviate the administrator’s management burden.
Integration between PAM and IGA enables you to know who is accessing the data and allows you to enforce a least-privileged access model – an essential tactic in a zero-trust strategy. Integration also significantly improves your compliance posture by providing proof for your auditors that access to all privileged accounts was properly reviewed and authorized.
Symantec does the heavy lifting of integration so you can achieve the right balance between protecting PII and giving employees the freedom to work
Why are integrations so vital to an effective cyber security strategy? Think of integrations as a web of protection woven tightly together. You could implement point products separately, but the result is a difficult-to-manage collection of technologies that might or might not work together. Any gap in the fabric of protection is an open invitation to cyber criminals.
Compliance penalties are no laughing matter, and customer lawsuits can lead to hundreds of millions of dollars’ worth of payments. Damage to your reputation can be incalculable and poorly integrated cyber security measures can degrade network performance and the user experience.
Symantec does the heavy lifting of integration so you can achieve the right balance between protecting PII and giving employees the freedom to work. You can have both.

Threats Evolve. Shouldn’t Your Cyber Defense?
Integrations aggregate threat intelligence for deep analysis and fast response






We encourage you to share your thoughts on your favorite social platform.